In memoriam – Mavis Batey MBE, codebreaker extraordinaire at Bletchley Park
 Mavis Batey MBE, codebreaker extraordinaire at Bletchley Park during World War II, died this week at the age of 92.
Mavis Batey MBE, codebreaker extraordinaire at Bletchley Park during World War II, died this week at the age of 92.
Ironically, perhaps – to cryptographers and computer scientists, at least – her MBE was awarded in recognition of her work in preserving and conserving British gardens.
This was a task to which she applied herself with conspicuous success after her secretive work as a cryptanalyst during the war.
Batey’s big cryptographic breakthrough, tackling the Italian military’s use of the Enigma encryption machine in the early 1940s, gives us an fascinating insight into how cryptanalysts think.
Where the rest of us might see random gibberish or algorithmic confusion, gifted cryptanalysts are able to spot important questions – and, more importantly, to answer them.
The enigma of Enigma
 The Enigma was an electromechanical encryption device, patented by a German engineer in 1918.
The Enigma was an electromechanical encryption device, patented by a German engineer in 1918.
It was adopted enthusiastically in various flavours by the Nazis and their European allies, and enhanced for additional security over the years leading up to the outbreak of World War II.
Enigma used three or more electrically-wired rotors that moved forward like a car’s odometer after each character, creating an electrical circuit that varied randomly every time.
So even if you typed in AAAAAA, you might get back EJMXLR.
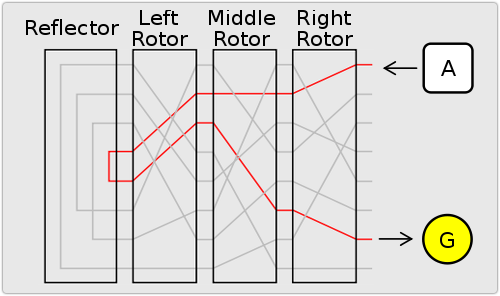
Presumably in an effort to boost the mixing effect, the designers made the leftmost rotor a “reflector” that re-routed the circuit back through the other rotors.
So, in a four-rotor engima, there were seven (3+1+3) rotors’ worth of mixed-up wiring for the current to follow.
The weak link
But one consequence of this, which would immediately be recognised today as an unacceptable cryptographic flaw, was that the reflector had to send the current back on a different wire, so a letter could never end up encrypted as itself.
For all that AAAAAA might give you EJMXLR, it could never give you BCDANF or YANQQP.
And one day, Mavis Batey looked at an intercept – not the one above, of course, but something that would have seemed just as meaningless to you or me – and realised that it had a curious characteristic.
The letter L, and only L, was missing, and she asked herself the important question, “Why?”
She surmised, correctly as it turned out, that she had stumbled across a test transmission, presumably generated by a pair of Italian radio operators who were checking that they had the day’s configuration settings correct.
(Enigma settings – the cryptographic keys – were varied each day according to closely-guarded printed books.)
The sender had simply pressed L repeatedly, so that Bletchley Park now had what’s called a known plaintext for an intercepted message.
Today, encryption algorithms are expected to be immune to attacks based on a known relationship between input and output, but for the Bletchley codebreakers it was just the start they needed.
Today’s the day
Indeed, building on this success, Batey later decrypted an Italian message that read TODAY’S THE DAY MINUS THREE.
But what did it mean?
One problem cryptanalysts face – even today, with modern computers at their disposal – is where to focus their efforts.
If you can reliably crack 1% of all encrypted messages, you are doing really well.
But if you don’t pick the right 1% to attack then you may end up knowing an awful lot about the regulations governing how Sergeant Majors should wax their moustaches, and not very much about impending attacks.
As Batey describes, the codebreakers went into overdrive:
[W]e worked for three days. It was all the nail-biting stuff of keeping up all night working. One kept thinking: ‘Well, would one be better at it if one had a little sleep or shall we just go on?’ — and it did take nearly all of three days. Then a very, very large message came in.
And what a message it was, documenting a massive attack against an Allied convoy en route from Egypt to Greece.
The Allies turned the tables, sending out a spotter plane that “just happened” to sight the Italian attackers (thus providing a plausible explanation for the intelligence), drawing the Italians into the Battle of Matapan, and subjecting them to an enormous naval setback.
Lest we forget
So, let’s take this opportunity to remember the war-time heroism of Mavis Batey MBE and the thousands of other cryptological soldiers who served so industriously against Nazism and Fascism in 1940s Europe.
→ If you have ever visited Bletchley Park (if you haven’t and you can, do it!), you will know how truly awful the working conditions were, with thousands of workers crammed into mostly cold, damp and insanitary huts to pit their intellects against what must have seemed not just unknown but unknowable. The operators of Tommy Flowers’ groundbreaking Colossus codebreaking computers, installed at Bletchley near the end of the war, famously had to wear Wellington boots to work, not merely to keep their feet dry but to avoid electrocution in the wet and leaky conditions.
And, while we’re about it, let’s draw a modern lesson from the work at Bletchley, taught to us by the Italian operator’s apparently-innocent use of LLL…LLL as a plaintext.
When using cryptographic tools, follow or exceed the manufacturer’s recommendations – don’t make up your own operating procedures, even if it feels as though you’re doing the right thing.
You can well imagine that the Italian signalman who sent the long-but-repetitious message was trying to improve things by making sure that he was ready to send and receive for the day, and not risking the mis-transmission of a real and possibly important message.
(Enigma was operationally slow and clumsy, since decryption required considerable manual effort, including transcribing the output, which appeared character-by-character on an illuminated letterboard.)
But he wasn’t supposed to do that, and if he hadn’t…
…who knows whether Mavis Batey would have deciphered that three-day warning in time?
Lest we forget.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/DG8cbub_OQY/