Just how secure is that mobile banking app?
 Ariel Sanchez, a researcher at security assesment company IOActive, recently published a fascinating report on the sort of security you can expect if you do your internet banking on an iPhone or iPad.
Ariel Sanchez, a researcher at security assesment company IOActive, recently published a fascinating report on the sort of security you can expect if you do your internet banking on an iPhone or iPad.
The answer, sadly, seems to be, “Very little.”
You should head over to IOActive’s blog to read the whole report.
Sanchez details the results of a series of offline security tests conducted against 40 different iOS banking apps used by 60 different banks in about 20 different countries.
Two problems stood out particularly:
- 70% of the apps offered no support at all for two-factor authentication.
- 40% of the apps accepted any SSL certificate for secure HTTP traffic.
Two-factor authentication
Banks are not alone in embracing and promoting two-factor authentication (2FA), also known as two-step verification.
Sites like Facebook, Twitter, and Outlook.com all offer, and encourage, the practice, for example by sending you an SMS (text message) containing a one-time passcode every time you try to log in.
The extra security this provides is obvious: crooks who steal your regular username and password are out of luck unless they also steal your mobile phone, without which they won’t receive the additional codes they need to login each time.
Interested in two-factor authentication?
![]()
You’d think that once a company had gone to the trouble of implementing 2FA for its customers, it would make it available to all its users.
But many of the banks, just like the social networks and webmail services, have let their mobile apps lag behind.
No support for 2FA, however, pales into insignificance when compared to the second problem: no HTTPS certificate validation.
The chain of trust
HTTPS certificates rely on a chain of trust, and validating that chain is important.
Here’s an example of an HTTPS connection, browsing to the “MySophos” download portal using Firefox:
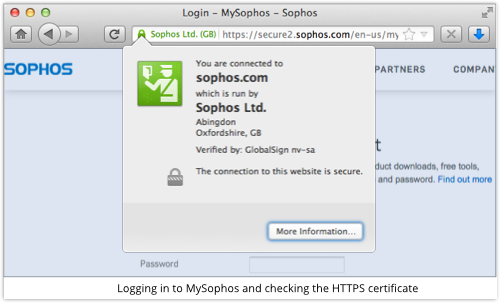
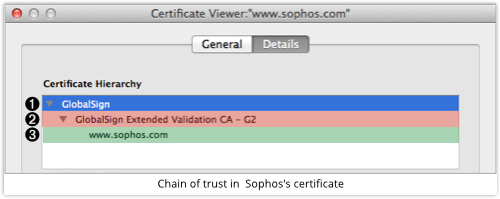
If we click on the [More information…] button, we’ll see that the chain of trust runs as shown below.
GlobalSign vouches for the GlobalSign Extended Validation CA (Certificate Authority), which vouches for Sophos’s claim to own www.sophos.com:
And GlobalSign is trusted directly by Firefox itself, with that trust propagating downwards to Sophos’s HTTPS certificate:
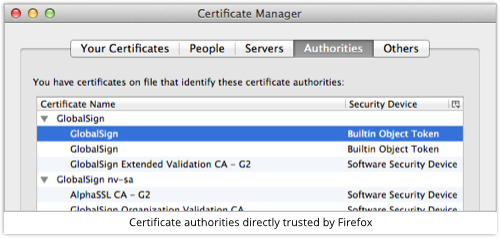
This chain of trust stops anyone who feels like it from blindly tricking users with a certificate that says, “Hey, folks, this is sophos.com, trust us!”
Anyone can create a certificate that makes such an claim, but unless they can also persuade a trusted CA to sign their home-made certificate, you’ll see a warning that something fishy is going on when the imposter tries to mislead you:
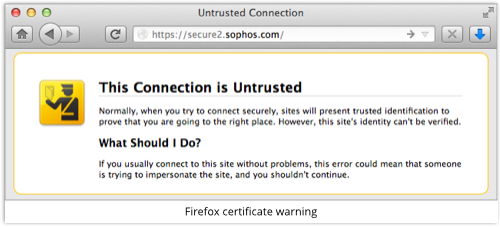
Digging further will explain the problem, namely that you have no reason to trust the certificate’s claim that this really is a sophos.com server:
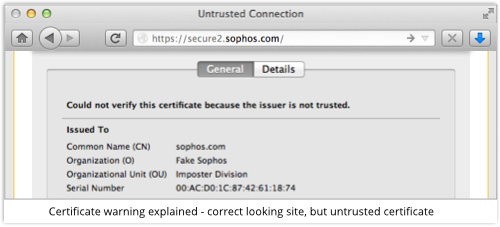
You’ll see a similar warning if you visit the imposter site from your iPhone or iPad, too:
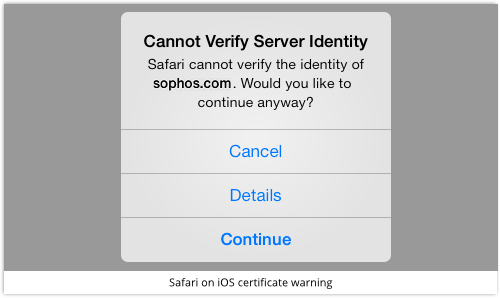
Again, digging further will reveal the untrusted certificate, and expose the deception, making it clear that you aren’t actually dealing with sophos.com at all:
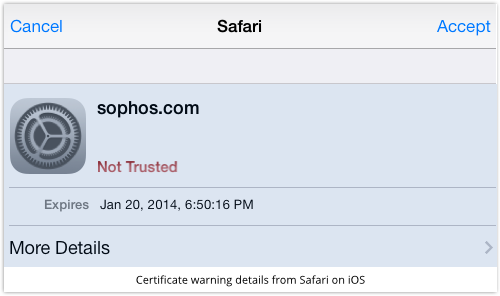
Now remember that in IOActive’s report, 40% of iOS banking apps simply didn’t produce any warnings of that sort when faced with a fake certificate.
You can feed those apps any certificate that claims to validate any website, and the app will blindly accept it.
So, if the banking app is misdirected to a phishing site, for example while you are using an untrusted network such as a Wi-Fi hotspot, you simply won’t know!
In fact, it’s not that you won’t notice, but that you can’t notice, and this is completely unacceptable.
The silver lining, I suppose, is that 60% of the 40 apps that IOActive tested did notice bogus HTTPS certificates.
The problem, though, is how you tell which camp your own bank’s app falls into.
If you aren’t sure, it’s probably best just to stick to a full-size computer, and a properly patched browser, for your internet banking.
Ironically, we wrote recently about a move by Dutch banks to set some minimum security standards that they will require customers to follow if they are to qualify for refunds of money stolen through phishing, carding or other forms of online fraud.
Sounds as though there may be a spot of “Physician, heal thyself” needed here…
Learn more about HTTPS/SSL
![]()
Image of HTTP URI on giant tablet courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/R8We-aKi8HE/