Malware Museum shows how it was “before it was all about money”
“The past is a foreign country: they do things differently there.”
If, by the past, we mean “malware in about 1990,” then they certainly did do things differently.
Mind you, a few things were the same.
By 1990, malware was known for many different platforms, including IBM mainframes, Unix, the Apple ][, the Mac and Atari.
(Sorry, Linux fans. Unix malware doesn’t just predate Windows malware, it predates Windows.)
Just like today, however, the vast majority of malware attacked a Microsoft operating system, thanks as much to its dominance as to the state of its built-in security.
Users of other operating systems assumed an attitude of superiority that they said was justified by the better security of their own operating system, but was equally well explained by plain old market forces.
Mind you, back then, the dominant platform was MS-DOS, which effectively had no built-in security.
By default, and by design (for simplicity and speed), any user could modify any byte of memory; take control of any file and therefore change it; or bypass the operating system entirely and read and write any sector on the disk, whether it belonged to an exisiting file or not.
Despite the similarities, however, the differences in old-school malware and malware authors were many:
- Almost all malware attacks were viruses. Before the commercial internet, malware spread itself “by force”, often by infecting as many other files as possible, so that one infected computer might end up with hundreds or thousands of infected programs on it. Any one of them might reactivate the infection if it were not detected and removed.
- Almost no malware attacks involved money.
- Once activated, many viruses made sure they were noticed.
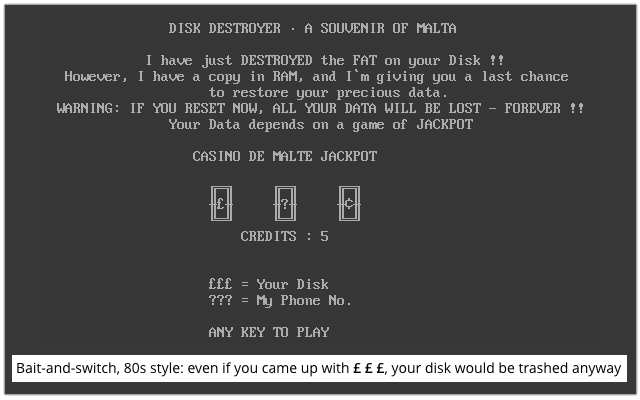
The AIDS Information Trojan of late 1989 was a notable exception, being the first known ransomware, but most viruses were about some sort of social anger. Of course, that was cold comfort to a victim who had just lost everything, with no “pay to recover” option, even if they wanted to.
That meant playing tunes; printing out messages, sometimes political; displaying graphics; messing with the keyboard; and even, in the case of the Casino virus, popping up a text-mode fruit machine that offered you a chance to win your File Allocation Table (FAT) back out of memory.
If you were involved in the anti-virus research scene back then, you will remember the challenge of replicating, decompiling and understanding these creatures all-to-well.
Although most viruses were tiny compared to today’s behemoths, and were usually self-contained, the tools for analysing them were as constrained and as slow as the computers they ran on, giving malware something of an operational advantage.
If you came into computer security in the modern malware era, once it was all about money, you’ve probably wondered, what did these things look like?
Now, instead of listening to the rose-tinted reminiscences of someone who was around back then [who would that be, then? – Ed.], you can take a look for yourself, in archive.org’s Malware Museum.
Just don’t click through if you have a deadline in the next hour or so :-)
Follow @NakedSecurity
Follow @duckblog
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/BNXeCxGT4X0/