Microsoft “failed update” phish might well sound believable – watch out!
 We get an awful lot of spam in our spamtraps.
We get an awful lot of spam in our spamtraps.
So it’s easy to get inured to spam, if you spend lots of time looking at it for research purposes.
But from time to time we find spams that are interesting enough – or at least intriguing enough – to write about anyway, such as the time 30-year-old Alex (NS, ND, GSOH) from Ukraine tried to sell us his liver (or part of it, at least).
When spammers add sickening disrespect to their regular criminality, we sometimes can’t sit on our hands about it, as when crooks used the aftermath of the Boston Marathon bombings to spread malware.
And occasionally we find an attempt at phishing that we grudgingly have to admit shows a resourceful sense of occasion.
We don’t respect it, and we disapprove as much as ever, but we have to say, “That’s not so far-fetched that you’re bound to delete it without a second thought.”
→ Phishing, don’t forget, is where cybercrooks try to charm/trick/persuade/terrify you into logging in to verify/check/win/dispute something such as a username/setting/iPad/invoice… only for you to realise, once you’ve put in your username, password and other details and clicked [Submit], that you were on an imposter site all along.
As you’ve probably heard, and perhaps experienced first hand if you are a Windows user, Microsoft’s Patch Tuesday updates have suffered some clumsiness lately.
In September, some updates turned up over and over (or “over and over and over”, as one reader put it) until Microsoft pushed out updates to the updates and things settled down.
So this email, though not exactly expected, isn’t outrageously obviously bogus at first sight, and might even relate to problems you’ve experienced recently:
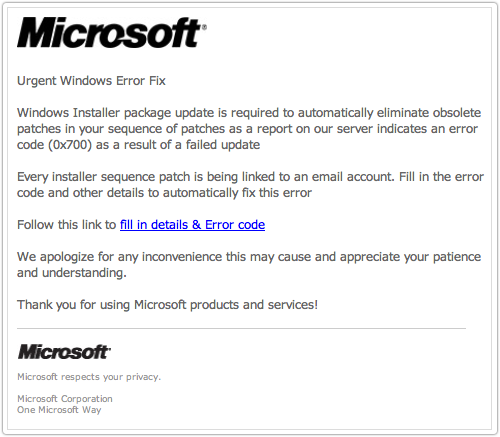
Windows Installer package update is required to automatically eliminate obsolete patches in your sequence of patches as a report on our server indicates an error code (0x700) as a result of a failed update
Every installer sequence patch is being linked to an email account. Fill in the error code and other details to automatically fix this error
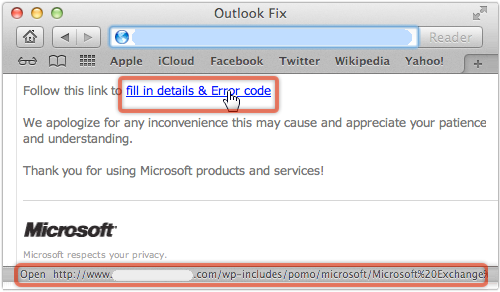
The link you’re asked to follow should be outrageously obviously bogus, however, since it neither links to Microsoft, nor uses HTTPS (secure HTTP):
The lack of HTTPS is cast into harsh relief when what looks like an official Microsoft login screen appears, where you would expect a secure page:
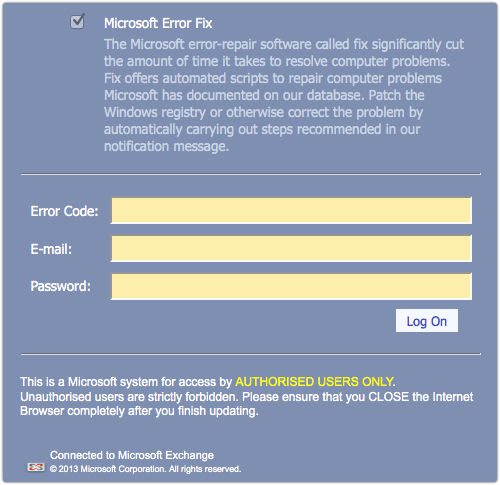
In short, be careful with emails you weren’t expecting, and be sure to check that the details add up – in this example, the missing HTTPS and the curious domain name don’t add up at all.
If in doubt, leave it out!
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/5JGEjtdzMFs/