Microsoft Patch Tuesday
 Microsoft’s Patch Tuesday for March 2014, the second-to-last scheduled patch that Windows XP users are ever going to see, will fix critical holes in all versions of Windows.
Microsoft’s Patch Tuesday for March 2014, the second-to-last scheduled patch that Windows XP users are ever going to see, will fix critical holes in all versions of Windows.
OK, not quite all versions: stripped-down Server Core installations will receive updates, but not critical ones.
There are five bulletins listed for for March – so far, anyway: in February, Microsoft officially pre-announced five updates, only to sneak in two more critical fixes at the last minute.
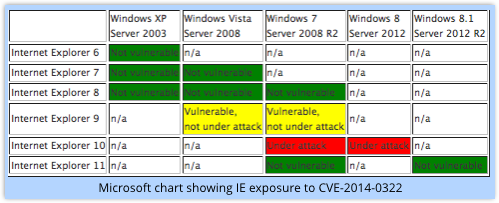
As usually happens, March’s patches include an everyone-gets-this Internet Explorer security update that applies from IE 6 to IE 11, in 32-bit and 64-bit versions, for Intel and ARM flavours of Windows.
What’s not yet clear is whether the recently-reported IE zero-day known as CVE-2014-0322 is amongst the bugs that will be patched.
The good news is that it won’t be a disaster if this zero-day isn’t fixed, even though it constitues a critical flaw, because there are already numerous workarounds and protections against the exploits that are so far known in the wild.
→ Microsoft ususally defines Windows and IE vulnerabilities as critical if they could theoretically lead to remote code execution, even if a way to exploit the hole – often referred to as weaponising it – is known only for one version of Windows or IE. It’s not always easy, or even possible, for hackers to take a security bug from “I can crash IE remotely” to “I can take over your browser at will,” so (fortunately) not all critical vulnerabilities end up weaponised for all versions or platforms.
As workarounds and mitigations for CVE-2014-0322, you can do the following:
- Apply Microsft’s Fix It tool, provided in Advisory 2934088.
- Use an anti-virus that can block files associated with the exploit (e.g. Sophos Anti-Virus reports them as Exp/20140322, Troj/SwfExp-CL and Troj/ExpJS-LA).
- Turn off Flash in your browser. Although the exploit doesn’t use a hole in Flash, current in-the-wild attacks load a Flash object first as part of the weaponisation.
- Upgrade to IE 11. The vulnerability does not exist in IE 9 or earlier, or in IE 11.
Nevertheless, let’s hope Microsoft will be closing the CVE-2014-0322 hole for good on Tuesday 11 March 2014: for further information once the Patch Tuesday updates have actually shipped, please visit the SophosLabs Threat Analysis pages.
Of course, even if you aren’t worried about CVE-2014-0322 in particular, you’ll be patching IE anyway.
As mentioned above, all supported IE versions are receiving updates in this month’s Bulletin One, which is denoted Critical – Remote Code Execution.
And if you are still using XP, take heed that all five bulletins this month – two critical and three important – are relevant to you. (Bulletin Five affects XP, but only if you have Silverlight installed.)
Yet in May 2014, when all other Windows users are getting the latest fixes, you’ll be getting nothing, except perhaps ever-increasing interest from cybercriminals.
Keep in mind: the first choice for a hungry lion is the buck that has fallen furthest behind the herd.
Oh, and lest we forget, OS X users get a look in this month: you’ll need to update Silverlight if you have it installed on your Mac.
→ I know what you’re thinking. I wondered this, too. “Do I have Silverlight on my Mac without realising it? Did I install it ages ago to access a website I never visited again, and then forget all about it?” You can answer that at the Get Microsoft Silverlight site.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/ZXApXx3Rv3k/