Misleading advertisements lead to hijacked browser settings
A few hours ago Mrs. W was looking to install a fresh copy of iTunes on her PC and performed a quick Google search.
Above the first (and correct) result was an ad. Nothing unusual about that, except that this particular ad screamed “SCAM!”
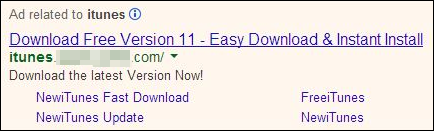
As you can see, the URL could lead one to believe it is the iTunes download site, so I thought I would check it out.
 The site I arrived at had a long list of legitimate applications with links to download them, including the one Mrs. W was interested in, iTunes.
The site I arrived at had a long list of legitimate applications with links to download them, including the one Mrs. W was interested in, iTunes.
This is where it is handy to have a virus lab hanging around. You can look into these things safely and see what the scam artists are up to with little to no risk.
I clicked the download button and was taken to a page with information on iTunes, some of which was very misleading.
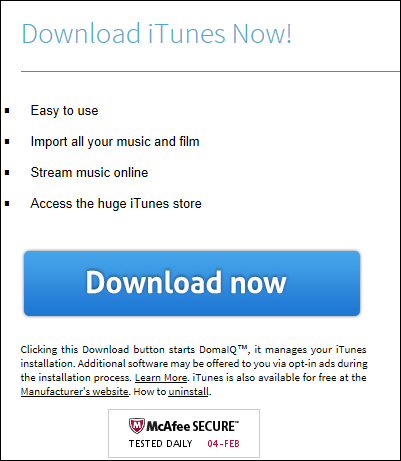
There is boilerplate legalese spread liberally around the page, but thankfully it is certified safe by our friends over at McAfee (or should I say Intel?).
They are correct; it is virus free. I wouldn’t interpret this to mean that it is harmless, though.
Everything about this feels a bit wrong. They mention you will be offered additional software via “opt-in ads.”
Strangely Internet Explorer 11’s SmartScreen filter didn’t whisper a word of warning, allowing me to run the file with minimal intervention.
After downloading, I ran the small executable which was digitally signed by Tuguu S.L., a company known for creating a pay-per-install toolbar that is widely considered to be adware or a potentially unwanted application.
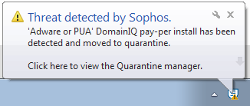 In fact, Sophos Antivirus detects this download as “‘Adware or PUA’ DomainIQ pay-per install”.
In fact, Sophos Antivirus detects this download as “‘Adware or PUA’ DomainIQ pay-per install”.
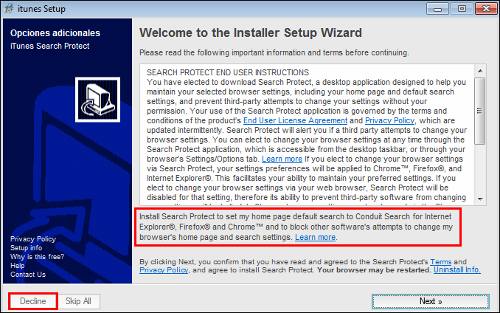
First, I was presented with a standard-looking “Welcome to the iTunes installation wizard” screen.
Next I was offered a fantastic opportunity to redirect my search engine queries to a partner and prohibit other programs from helping me undo the mess.
“Install Search Protect to set my home page default search to Conduit Search for Internet Explorer, Firefox and Chrome and to block other software’s attempts to change my browser’s home page and search settings.”
Not exactly comforting words, but most of us are trained to click the Next button until it changes to Finish.
Eventually it connects to the real Apple website and downloads iTunes in the background. In my case, it downloaded the 32-bit version, which would not even install on my 64-bit Windows 7 operating system.
It did, however, successfully hijack my search engine and home page settings in all installed browsers.
Part of the problem with trying to warn people of the dangers of these types of misleading installers is the fact the Adobe and Oracle are both engaging in similar behaviour, lending an air of legitimacy to the practice.
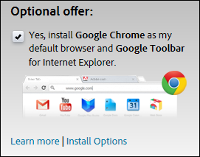 When Adobe released a critical update for Flash Player in February of 2014, it defaulted to installing Google Chrome and making it my default browser unless I opted out.
When Adobe released a critical update for Flash Player in February of 2014, it defaulted to installing Google Chrome and making it my default browser unless I opted out.
Oracle’s Java uses a similar tactic, offering to hijack your search engine to everyone’s preferred search provider, Ask.com.
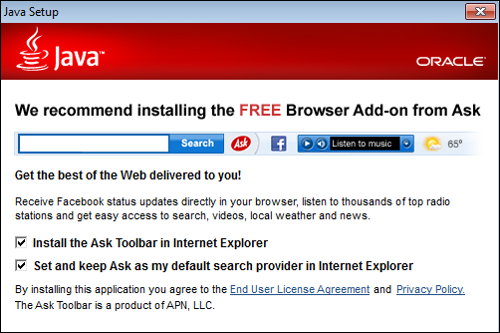
With Oracle’s $37 billion of revenue in 2013 and Adobe’s $4 billion, I am not convinced they need to resort to bundling unwanted additional packages with plugin downloads.
You need to approach software downloads with the same caution that you approach websites that may wish to phish your credentials.
Always go directly to the source. Don’t trust ads and don’t click links in emails. Instead, go directly to the manufacturer’s website.
Lastly, pay close attention to checkboxes and what you are agreeing to. Apparently even legitimate software vendors can occasionally betray your confidence.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/tVQD8gSGqg4/