Mozilla to take action against WoSign’s woeful cryptographic blunders
A month ago, we wrote about a serious cryptographic blunder by a company that really ought to have known better.
That company was WoSign, a Chinese certificate authority, or CA.
As we explained back in August 2016, a CA’s primary job is to vouch for security certificates on your behalf.
Imagine, for example, that you want a digital certificate you can use on your website to assert your identity, or a certificate you can use to sign your software to stop crooks making imposter copies and passing them off as yours.
You can create and sign your own certificates, which is a start, but no one’s browser or operating system will trust them by default, so your users will see security warnings like this one when they visit your website:
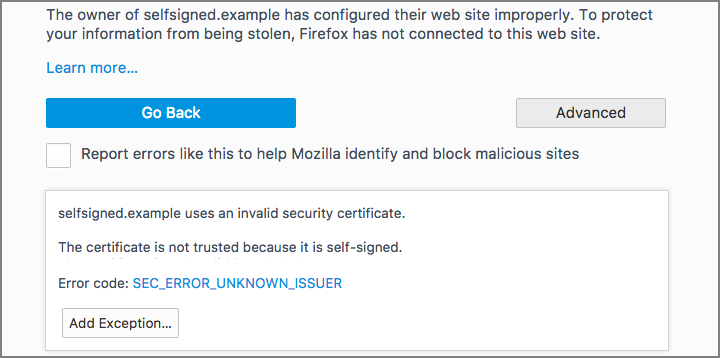
But if you create a certificate and a trusted CA signs it for you – a CA that is already on the list of trusted root authorities in your browser or your operating system – then you will automatically be trusted, too.
This chain of trust is a key component of TLS, the system that puts the padlock in your browser.
WoSign, it turned out, wasn’t very careful about how it vouched for its customers’ websites.
A user found this out when he applied for a certificate vouching that he was authorised to run a specific subdomain of the University of Central Florida, namely the medical faculty’s site med.ucf.edu.
To his surprise, he also ended up with a certificate vouching that he owned the University’s main website, at www.ucf.edu, even though that server was outside his bailiwick.
Even more alarmingly, he applied for a certificate for a subdomain he owned on the well-known public code hosting service Github, and ended up with a certificate for all of github.com and github.io, too. (He also got www.github.io, just to make matters worse.)
This all came to light in a series of discussions in Mozilla’s security policy discussion forum last month.
Commenters on Naked Security were almost universally in favour of kicking WoSign out of the privileged club of trusted CA without further delay:
Bryan: A CA should absolutely be excommunicated if they can’t can’t rapidly right their wrongs and document quite publicly that it’s being done.
Blake: If Mozilla maintains WoSign in their default trusted CA list, that’s a statement that Mozilla believes WoSign is trustworthy. Personally, I have doubts about any organization that makes repeated mistakes, and doesn’t own up to them, being included in this small circle.
Bbusschots: How can anyone have any faith in the CA system if breaches of the rule don’t have consequences? This CA literally put the entire internet at risk, and it looks to me like they simply do not understand the mangnitude of their failings.
Tony Cross: The key word here is ‘trust’. WoSign have clearly demonstrated that they can’t be trusted. That’s the bottom line.
Mozilla has now published a lengthy overview of WoSign’s failings, which go beyond just giving a random person the key to impersonate all of Github, and it makes depressing reading.
Amongst other things, it seems that WoSign also:
- Backdated certificates to beat a deadline banning the use of the now-deprecated SHA1 hashing algorithm.
- Acquired another CA called StartCom without reporting the change of ownership, as required by Mozilla.
- Denied the change in ownership when questioned.
Unsurprisingly, Mozilla’s slow-but-steady conclusion mirrors the off-the-cuff opinions stated by Naked Security readers a month ago:
Mozilla’s CA team has lost confidence in the ability of WoSign/StartCom to faithfully and competently discharge the functions of a CA.
What next?
You can probably guess what happens now, at least for users of Mozilla products based on Mozilla’s own list of trusted CAs, such as the Firefox browser and the Thunderbird email client.
WoSign gets kicked out of the trusted CA’s club, right?
Wrong.
Mozilla is still taking the softly-softly approach:
Therefore we propose that, starting on a date to be determined in the near future, Mozilla products will no longer trust newly-issued certificates issued by the [WoSign or StartCom] CA brands.
In other words, any certificates already issued will continue to be trusted, and even those that the company issues in the future will still be trusted until a future date to be set at a future date.
What do you think?
Does the CA ecosystem need a softly-softly approach that minimises disruption, or the occasional short, sharp shock that sets the strictest standards?
Follow @NakedSecurity
Follow @duckblog
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/71623mU6s4Y/