National Crime Agency website DDoSed by Lizard Squad

Intransigent sort-of hacker collective Lizard Squad is back.
Apparently.
Last week, the UK’s National Crime Agency (NCA) announced the arrest of six youngsters, aged 15 to 18, for alleged DDoS cybercrimes.
DDoS is short for Distributed Denial of Service, and it’s a type of cyberattack in which a crook gets anywhere from hundreds to hundreds of thousands of computers to send simultaneous but purposeless traffic to a victim’s server.
Usually, DDoSes are kicked off using bots, or zombie malware, where infected computers randomly scattered around the are surreptitiously sent instructions to “visit” a victim’s website.
💡 Learn more: Understanding zombie malware ►
That makes DDoSes hard to protect against.
Firstly, DDoS traffic generally originates from a wide variety of regular computers.
So there are no obvious culprits to block with a firewall rule.
Secondly, DDoS traffic generally relies on perfectly normal-looking requests, such as “please send me your home page and all that’s on it,” just like your browser would.
So blindly blocking DDoS requests by URL would cut off your real users as well.
→ DDoSes are sufficiently prevalent, and the need to refer to them so common, that the abbreviation “DDoS” has become a word in its own right. In case you are wondering, it is usually said aloud as the acronym “dee-doss” rather than the initialism “dee-dee oh-ess.” Sadly, you will be widely understood whichever pronunciation you choose.
Visiting a website that’s under DDoS attack is a bit like being at the railway station ticket office at 10:10 and suddenly realising that the ten people in front of you in the queue are all waiting to make laborious enquiries about next month’s timetable changes, while you’re trying to buy a ticket on today’s 10:15 to Abingdon-on-Thames [*].
Anyway, the teenagers who were arrested are alleged to have used an online crimeware-as-a-service tool called LizardStresser, operated by none other than the Lizard Squad.
Instead of building your own botnet, writing your own malware, and orchestrating your own attack, you could simply buy time on LizardStresser, which would then deal with clogging up the website or websites of your choice to a clog-level of your choice.
Loosely put, when you use “cybercrime deskilling” services of this sort, the more you’re prepared to pay, the more time-wasters the service operators will send to the station to stand in the queue in front of your victims to ask pointless but otherwise unexceptionable questions so that they’ll miss their trains.
Surprise, surprise, therefore, when supposed representatives of Lizard Squad, tweeting as @LizardLands, announced late last week:
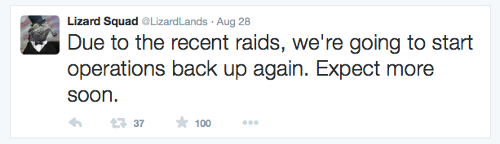
Due to the recent raids, we’re going to start operations back up again. Expect more soon.
And this morning, according to @LizardLands and Sky News, it happened:
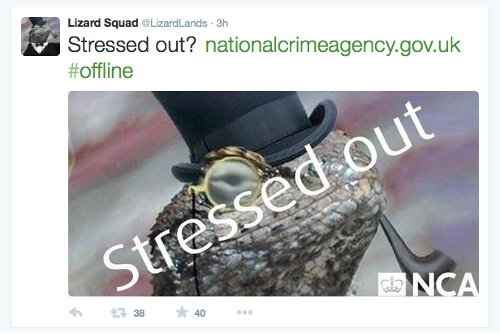
Stressed out? http://www.nationalcrimeagency.gov.uk/ #offline
(Note: the tweet above may seem to imply that the image is a screenshot of an “as hacked” NCA website, but it is merely an image with the NCA logo added.)
Sky, at any rate, reports that it was unable to access the NCA site for a while, and quoted the NCA as saying that its site was an “attractive target” and that “attacks on it are a fact of life”.
That’s not a cop-out by the NCA.
As you can probably imagine from our description of DDoSes above, you need about as much skill to mount a DDoS as you do to hurl a brick through someone’s window.
Fortunately, in the case of a DDoS, you don’t generally end up with the network equivalent of a broken window, but with what amounts to a shop that had to close early.
That means that DDoS is not a crime that inevitably leaves you exposed to follow-up crimes, such as data breaches, intellectual property theft or privacy intrusion.
So you can accept as fair and true the NCA’s statement to Sky that this DDoS was not a security breach, and didn’t affect its operational capability.
Lizard Squad’s operational security, however, has been found lacking in the past, with numerous alleged members busted and even a breach against the abovementioned LizardStresser service.
Taunting the NCA like this might turn out to be a mistake, give that cybercrooks often turn out to be a lot less anonymous than they first thought.
Lizards mess with dragons at their own peril!
💡 Have your say: How much anonymity is too much? ►
[*] In truth, getting a train ticket to Abingdon would be a bit of a magic trick. The station closed in 1963 and the track was removed by the 1990s.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/RMCv8Y2umVA/