New phishing campaign uses 30-year-old Microsoft mess as bait
The ever-vigilant folk at the Internet Storm Centre (SANS) have spotted yet another campaign trying to drop the Locky ransomware using compromised Word files.
As Internet Storm Center handler Brad Duncan writes, the vector in the Word documents uses Microsoft Dynamic Data Exchange (DDE), a feature that lets Office application load data from another Office file. This is the kind of attack that last week was spotted in a phishing campaign launched at Freddie Mac.
Duncan outlines the attack approach in this flowchart:
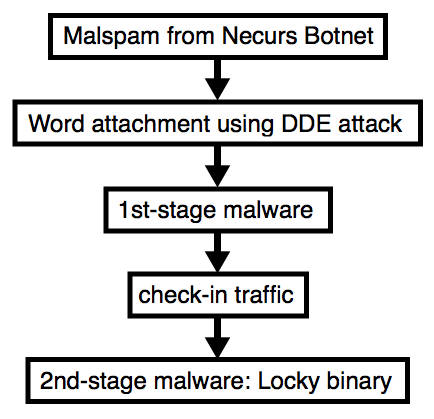
Image: Brad Duncan, SANS
The phishing messages carrying this attack come from the Necurs botnet, he writes, and as with other DDE attacks the aim is to convince users to OK through the security warnings. A fake invoice is the scammers’ preferred weapon.
If the attack cons the victim, the poisoned document fetches a downloader which in turn pulls a copy of Locky to decrypt at the target.
Once the ransomware’s launched and it’s encrypted the victim’s hard drive, Locky is deleted (a downloader is left behind), and a demand for 0.25 Bitcoin issued.
Duncan writes: “This is an interesting development, because it shows how the DDE attack technique has spread to large-scale distribution campaigns. It’s not new, and I’m not sure how effective it really is. If you know of anyone who was infected from one of these DDE-based Office documents, please tell your story in the comments.”
The Register noted last week that DDE (Dynamic Data Exchange) has been around since 1987, and it’s an increasingly-popular target for attackers.
Since users have to okay execution, Microsoft steadfastly insists DDE is a feature, not a bug. ®
Sponsored:
The Joy and Pain of Buying IT – Have Your Say
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2017/10/23/locky_spread_by_necurs_botnet_in_dde_attack/