PayPal 2FA bypass – how did *that* get past testing?
In a delightfully short and sweet technical article, UK security researcher Henry Hoggard recently reported on a PayPal authentication bug he found.
He was paid a bounty by PayPal, and the hole is now closed, so revealing it doesn’t give away any security secrets that might still be abused…
…so we thought we’d tell you the story, given that it’s Friday afternoon and all that, because it’s almost funny.
Actually, it is funny, but not the sort of joke at which you want to laugh out loud, because there’s an unfunny side to it.
The unfunny side is, “What was PayPal thinking? Who was doing the quality assurance? How did that one slip past?”
Here’s what happened.
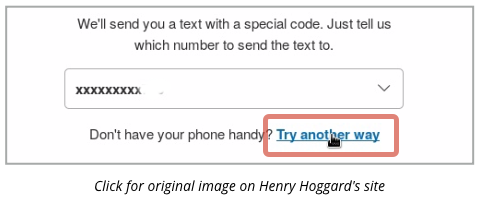
Hoggard was trying to login to PayPal using its two-factor authentication (2FA) system.
He couldn’t receive his 2FA token via mobile phone, so he decided to use PayPal’s “try another way” option to identify himself to the service.
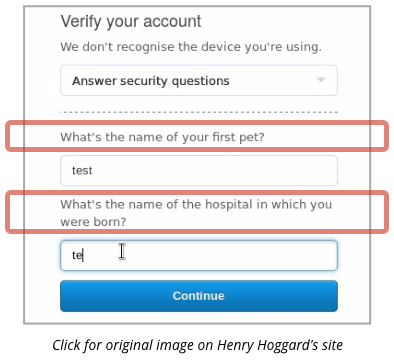
He was asked to provide the answers to two of his so-called security questions, a secondary form of authentication that some sites use on the grounds that:
- You don’t type in the answers very often, so they are less likely to get keylogged or otherwise stolen.
- You don’t always get asked the same questions, so even if you do get keylogged once, the answers probably won’t be enough next time.
By using a proxy to monitor his own network traffic, Hoggard noticed that both the questions and the submitted answers were embedded into the URL used for logging in.
Could a crook figure out how to submit correct answers?
Hoggard quickly discovered that a crook could do just that, by simply removing the questions and the answers from the URL altogether.
Lo and behold! Zero questions wrong out of zero questions asked, total errors zero, authentication approved.
It’s hard to believe that sort of attack got past testing, but apparently it did.
In other words, the client decides which questions to ask, and a test with zero questions is treated as valid.
Obviously, that’s not right: the server asked the questions in the first place, so it doesn’t need to rely on the client to repeat the questions when it replies.
Simply put: when you ask a candidate to sit an examination, you’re supposed to set the exam paper, not the candidate!
One more thing
One more thing is PayPal’s awful choice of “security” questions.
Pet’s names are truly terrible choices for any sort of password, because the answers are usually easy to guess, or can be looked up on Facebook.
And your birth hospital is an equally dreadful question, because you may not have one (if, like many people, you were born at home), you can never change it, and it’s no one else’s business, anyway.
So, we strongly recommend that you treat these so-called “security” questions like any password, and invent an answer that is unique and complex.
In fact, if you use a password manager, let it choose an answer for you.
PayPal won’t know that you never actually had a rabbit called DDOAIXSWIWHLYFTRFQRPRTQORPABGVHC or a cat that answered to xEc1lnlanrpgLBdDUX3fIj7kX2rC.
Follow @NakedSecurity
Follow @duckblog
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/aVKEStbJiAU/