PayPal SMS scams – don’t fall for them!
SMS messages, or “texts”, are old hat these days.
These days, most of us prefer services that don’t go through the mobile phone network, such as WhatsApp, WeChat, Facebook Messenger and Snapchat.
Nevertheless, SMS messages haven’t died out completely, not least because they’re a lowest common denominator that pretty much every mobile phone in the world can receive.
All you need is the recipient’s phone number.
As a result, SMS is still a popular choice for businesses that need or want to tell you something important without wondering which messaging app you prefer.
SMS messages are short and simple, with no room for “Dear Sir/Madam”, so people don’t expect to be greeted by name; there are usually few pleasantries or polite words; and there’s no need for fancy layout, icons, fonts or other typographical and artistic details.
As a result, crooks can create believable fakes, with no obvious mistakes, fairly easily.
Like these two reported by Naked Security readers recently:
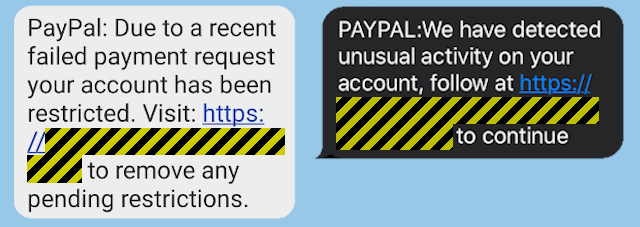
The problem with phones
Both website names used in these text messages were registered just a day or two before the messages showed up, presumably for the sole purpose of these very phishing campaigns.
As we’ve warned before, a tricky problem with any web links you receive on your mobile phone is that it’s often harder to spot that a link is not what it seems.
Most of us use our phones in portrait mode, leaving much less screen space to display long URLs, with the result that you generally see the just left hand end of the web address, and not the right hand end.
Crooks almost certainly can’t get hold of a server name that ends with, say, paypal DOT com, but can create any number of subdomains that start with paypal DOT and end with some unrelated domain.
But the suspicious-looking right-hand end of a full domain name often ends up invisible on a mobile phone because it won’t fit in the address bar.
HTTPS doesn’t guarantee truth
As you can see above, both websites use HTTPS, which denotes secure HTTP.
Remember, however, that HTTPS vouches for the security of the network communication between your browser and the website at the other end. It doesn’t vouch for the honesty or accuracy of the information that gets served up to you.
Sure, a site without HTTPS is best avoided – anyone nearby on the internet can spy on what you are doing, because there’s no encryption.
But a site with HTTPS isn’t automatically trustworthy on that account alone.
After all, crooks can have valid driving licences or other government-issued ID, but those IDs only vouch for who they are, not for their honesty or trustworthiness.
Keep it simple!
If you click through, the phishing scam is uncomplicated and, at least at first sight, believable enough.
You’re first asked to log in to your PayPal account:
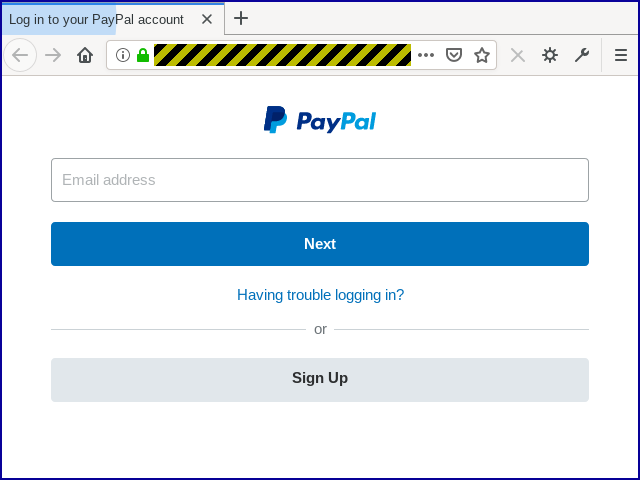
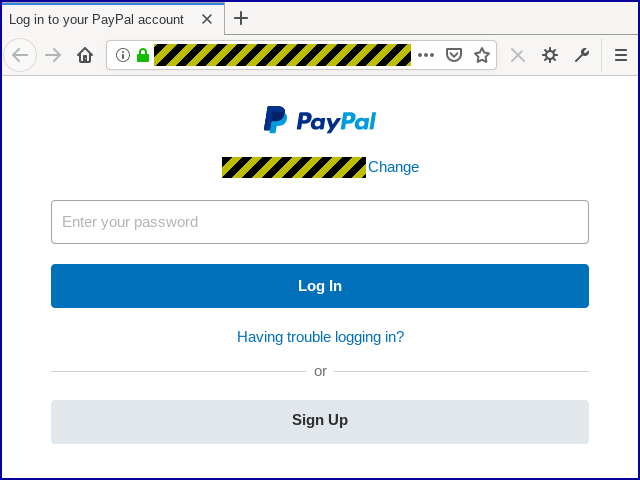
By this point, of course, the crooks are already ahead because you’ve just uploaded your password to their bogus site.
For a touch of reassurance, there’s a legitimate-looking visual delay before the crooks hit you with their next phishing page:
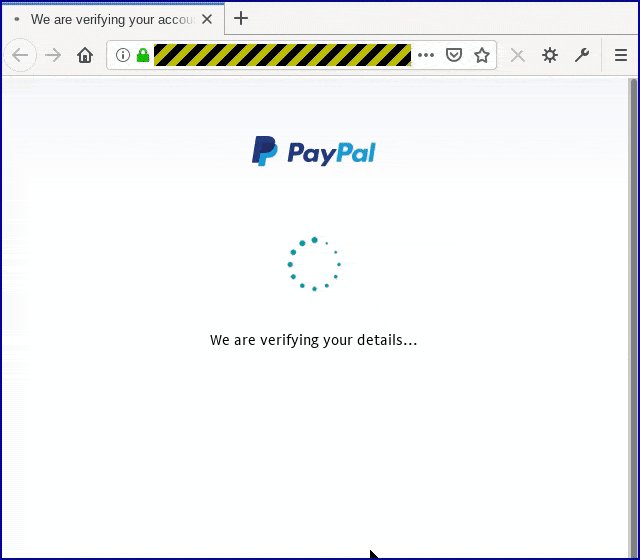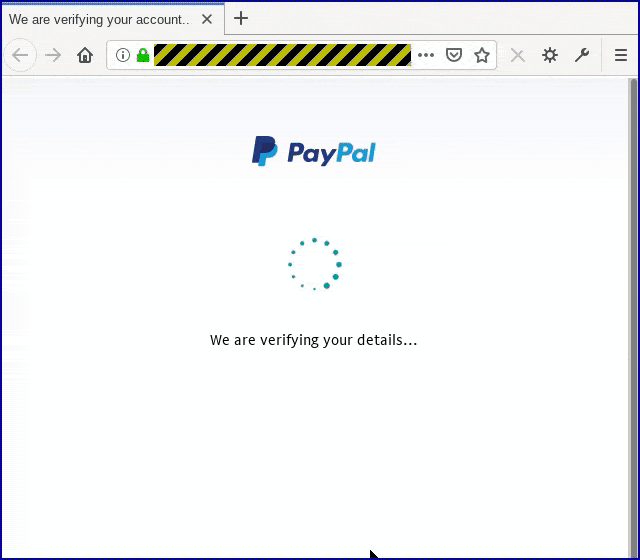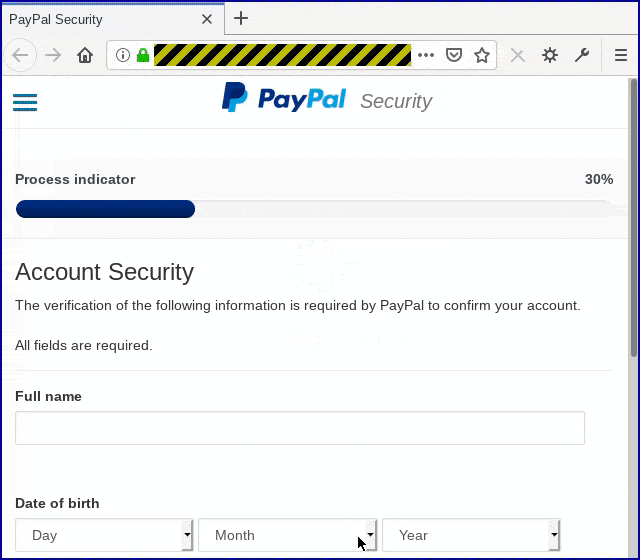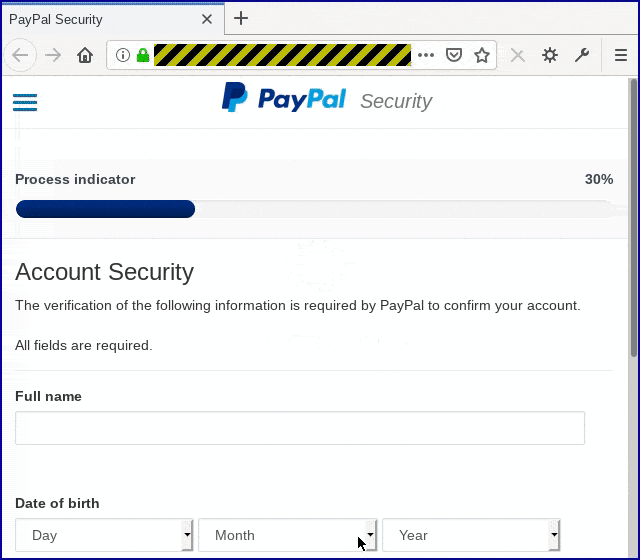
If you weren’t suspicious when the password page popped up, you should definitely be suspicious from this point on, given the amount of personal data being requested just to show you a transaction:
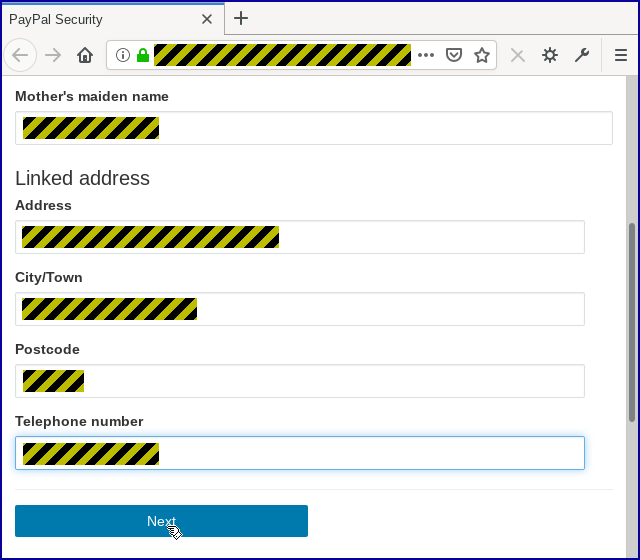
You definitely wouldn’t need to put in your credit card and bank details, as the crooks urge you to do on the next page:
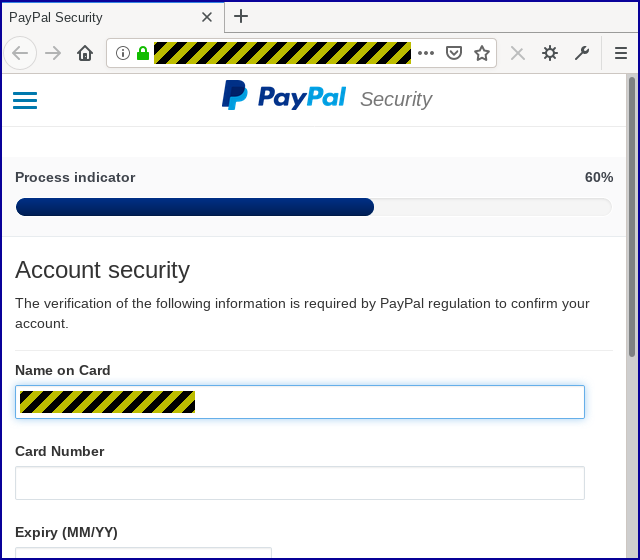
End with the truth
If you do supply the crooks with everything they’re after, the crooks bump you across to the genuine PayPal home page.
That might not be exactly where you’d expect to end up, but it does make for a softer and more believable landing than if your browser just crashed, or popped up some sort of error you’d never seen before:
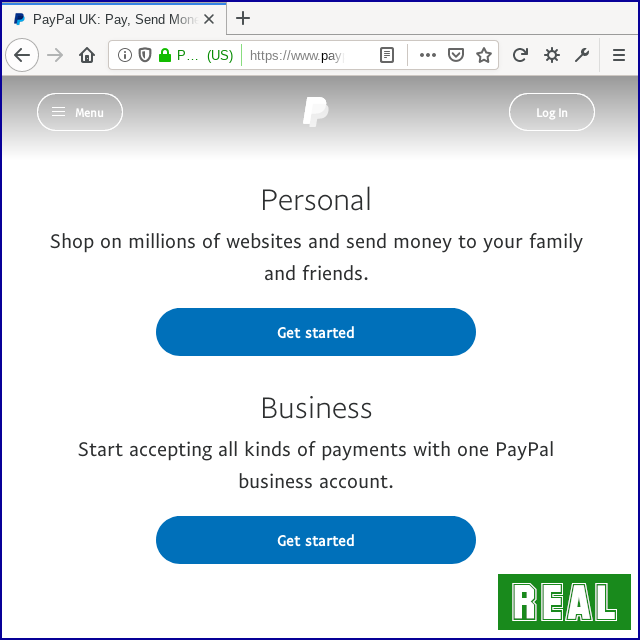
Another trick that the crooks used in this scam was to remember the IP number (the network identifier) that you just used to visit their fraudulent pages. (IP numbers don’t always pinpoint individual computers, but they usually identify households or business premises.)
If you click through to the scam again, at least within the next few hours, you won’t see the telltale signs of the scam the second time around – you’ll just end up redirected immediately to the final, real PayPal page shown above.
In other words, if you have second thoughts about what just happened, or if you ask a trusted friend or family member to investigate for you, things won’t look suspicious when you go back for a second look.
What to do?
- Avoid links in text messages. If you know you’ll be dealing with company X, such as PayPal, find out the right website and and go there yourself. Don’t rely on links texted to you, because those links can say whatever the sender wants.
- Check the URL in the address bar. Be especially careful on your mobile phone, where the address bar often doesn’t show much text from the URL you are visiting. Stop and take the time to scroll right – don’t blindly believe the text you see at the left-hand end.
- If you realise you just revealed your password to imposters, change it immediately. The crooks who run phishing sites typically try out stolen passwords immediately and automatically, so the sooner you act, the more likely you will beat them to it.
- Report compromised bank data at once. If you get as far entering any financial data before you realise it’s a scam, call your bank’s fraud reporting number at once. (Look on the back of your credit card so you get the right phone number – never reply using contact details from the original message.)
PS. Don’t forget that just typing data into a web form exposes it to crooks because they can “keylog” what you type into a webpage even if you never press the [Submit] or [Next] button.
Latest Naked Security podcast
LISTEN NOW
Click-and-drag on the soundwaves below to skip to any point in the podcast. You can also listen directly on Soundcloud.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/OuQJbO6XlzE/