Prepare to be Thunderstruck: what if @deuszu isn’t the Ashley Madison hacker?
Security researcher Brian Krebs last week named whoever is behind the Twitter account @deuszu as likely having had a hand in the Ashley Madison hack. But has Krebs named the right entity?
Attribution isn’t that easy and Krebs has gone out on a limb.
Take, for example, Krebs’ belief that a fondness for the AC/DC tune Thunderstruck links @deuszu to the Ashley Madison attack.
A screen-cap posted by Krebs (sourced from @deuszu’s Twitter account) suggests @deuszu had a web tab open, playing AC/DC’s “Thunderstruck” in 2012, and in 2015 the Ashley Madison hackers made the company’s work computers play the song “Thunderstruck.”
The image below was grabbed in August 4th 2012. Might it indicate guilt in the AshMad hacking? Or is there something else tying @deuszu, Thunderstruck, and later events?
To form a counter-argument, consider the other news grabbing global attention in late July 2012?
Iranian nuke plants rocked in midnight ‘heavy metal blast’ – a tale of something odd going in Iran emerged in late July of that year.
It’s not really too much of a stretch to think that in early August 2012, @deuszu might have been listening to Thunderstruck, based on his interest in infosec news and the level of media attention mentioning the song at the time.
Even @deuszu’s later use of the tune in defacements he Tweeted seems like simple imitation of what happened in Iran.
The claim the Impact Team hackers managed to make Ashley Madison employee’s computers play AC/DC’s Thunderstruck in 2015, and a screenshot showing @deuszu once listened to the same song in 2012, is hardly forensic proof @deuszu is responsible for the Ashley Madison hack.
Who knew what, first?
The second point that bothers me is to attribute this hack to @deuszu based on a belief that Twitter provides the best – or only – timeline for the hack.
Krebs’ assertion that Twitter account @deuszu appears “to be closely connected” to the Ashley Madison hack appears to rest on this Tweet:
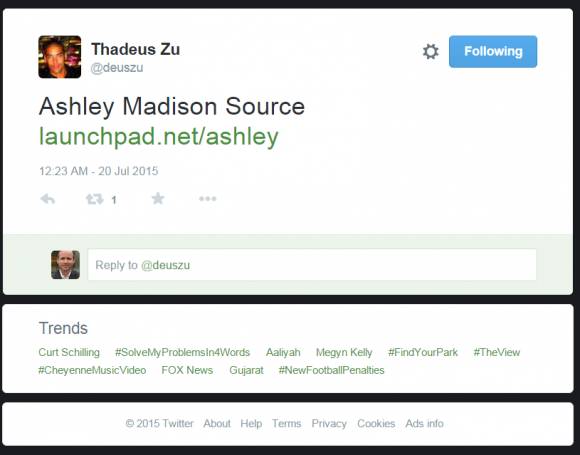
Krebs wrote that @deuszu’s tweet, on the 19th July 2015 (containing a link to hacked Ashley Madison data) “startled” him, because he “…couldn’t find any other sites online that were actually linking to that source code cache.”
Yet the news was already spreading on Full Disclosure:

Thadeus Zu may well have been the first to post about it on Twitter on July 17th (without linking to the dumps), but frankly, tweeting about a breaking story – already announced online for more than 48 hours – is a pretty crummy indication of potential guilt in perpetrating the original hack.
Impact Team publicly announced the hack on 15 July 2015 — two whole days before @deuszu first tweeted about the breach on 17 July. It’s only strange nobody tweeted about the hack sooner.
Where in the world is @deuszu?
Evidence about Zu’s location, based on his Tweet-stream, is also equivocal.
Krebs has also made a number of claims about Thadeus Zu’s potential location, based on social media open source intelligence (OSINT) from Facebook and Twitter.
“Zu’s Facebook profile wants visitors to think he lives in Hawaii,” Krebs writes, basing his claim on stock photos and a time zone posted by Zu.
Yet evidence Zu actually lives in Hawaii is scant, as Krebs notes: it’s limited to timezone information and tags from other people. It’s not hard to change timezone settings, or to misinform.
One of Zu’s Twitter accounts follows Australian news and political accounts (as Krebs notices), but it’s also worth stating that Zu is a member of a number of Facebook groups with links to Italy and Australia; and that @ThadeusZu has previously posted links mentioning Brisbane, Australia.
Krebs’ article kicked off a Twitter spat with Zu over the last few days and the researcher’s claims were widely reported.
But there’s two particular details that are just as indicative of Zu’s identity and association as Krebs’ observations:
It would be just as easy (although outrageously conspiratorial) to paint Zu as an Army psy-ops cointel-pro Twitter account, partly-human-manned, part-bot script account, scraping and scanning social media, trying to gather intel by tweeting tantalising snippets in almost gibberish tweet-speak and perpetrating small defacements on a regular basis in an attempt to appear legitimate to other hackers. An intelligence organisation-funded Twitter account, that potentially jumped the gun and tweeted a link about a hack it was tracking just a little too early, gaining international media interest.
Of course, such claims are utterly unfounded (for now), but Krebs’ theories about @deuszu and the Ashley Madison hack are little stronger. For all we know, Zu may be a dog on the internet.
Zu’s potential involvement in previous website defacements seems like a fairly low-value target for a legal prosecutor to chase.
Although linking to dumped data has landed others in jail before, based on the actual evidence at hand it seems there’s little evidence in the public realm that Zu is behind the actual Ashley Madison hack.
Of course, the Ashley Madison hack has generated huge public interest, fuelled by the US$500,000 reward offered by Avid Life Media for information leading to the prosecution of the hackers.
Of course, Zu is unlikely to mount any legal challenge, since that would expose his identity, and his numerous screen-caps over the years of various Website defacements would certainly bring unwanted attention from law enforcement.
Zu looks like an easy target – but probably the wrong one. ®
Sponsored:
Go beyond APM with real-time IT operations analytics
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2015/09/01/prepare_to_be_thunderstruck_what_if_deuszu_isnt_the_ashley_madison_hacker/