PWN2OWN Day One
 Wednesday 12 March 2014 was the first day of the PWN2OWN 2014 competition.
Wednesday 12 March 2014 was the first day of the PWN2OWN 2014 competition.
That’s an elite hacking competition that runs each year in parallel with the CanSecWest security conference in Vancouver, Canada.
The name is a sort of multi-way pun, based on the fact that hackers have a penchant for deliberate mis-spellings, perhaps as a sort of light-hearted irony.
After all, you’d expect that people who know off the tops of their heads that NTAdjustPrivilegesToken() has five input and three output parameters [*] could remember that the definite article is written “the”, not “teh.”
In teh same vein, hackers generally write “own” as “pwn,” at least in the context of owning a computer by getting access where they aren’t supposed to.
→ I didn’t write getting unauthorised access because digital breaking-and-entering can be done lawfully if the owner gives permission, as typically happens before a penetration test, or a PWN2OWN competition attempt.
Indeed, in PWN2OWN, if you PWN the software you are attacking, you OWN the hardware on which you ran the attack – literally, because the laptops supplied for competition entrants are part of the prize pool.
There’s also cash, and plenty of it: just over $1,000,000 up for grabs in this year’s event.
Entrants could choose to attack one or more of the following software configurations:
Straight browser attacks:
Attacks via Internet Explorer 11 plug-ins:
PWN2OWN Grand Prize via IE 11 plus EMET:
The Grand Prize, dubbed the Unicorn, ended up unattempted.
Challengers not only had to pwn IE11, but also to bypass Microsoft’s EMET toolkit (a sort of sandbox for IE11’s sandbox) and then get all-powerful SYSTEM-level privileges.
 It’s tempting to hope that the Unicorn went untested because it was simply too difficult – and that is, indeed, quite likely.
It’s tempting to hope that the Unicorn went untested because it was simply too difficult – and that is, indeed, quite likely.
But absence of evidence is not evidence of absence.
For all we know, a hack of that extent might simply be worth more elsewhere than the $150,000 that the sponsors were offering in prize money.
There were plenty of other attacks attempted, however.
In the past, if there were multiple entrants taking on the same target software, they attacked in a randomly-chosen order and the first to PWN was sole winner.
Other competitors didn’t even get to try out their exploits, no matter how slick they might have been.
Presumably, this was to dissuade everyone from choosing the target considered the easiest, and ignoring the tougher ones.
This year, however, co-sponsors HP and Google announced in advance that everyone would get a try at their chosen platform, and anyone who PWNed their target in the 30-minute timeslot would be judged a winner.
(In fact, last year, all PWNers got to have a try, and ended up getting paid out, too, but that was a bonus that was only announced after the competition had started.)
Last year, the Oracle Java plugin was worth the smallest prize, just $20,000, compared to $100,000 for IE 10 or Chrome, and was pwned four times in all.
This year it was also the back-marker in prize money, worth $30,000, compared to other prizes such as the $75,000 for pwning Adobe Flash, and $100,000 for IE 11.
But at the end of Day One, Java was the only target still standing.
French exploit-finding firm Vupen, which somewhat controverisally bills itself as “the leading provider of defensive and offensive cyber security”, was scheduled to attack Java at 13:00 on Wednesday, but withdrew.
Attackers obviously have to come well-prepared, as they have just 30 minutes to start and finish their break-in.
But they are also required to take on a system in its default configuration, with all current, official patches.
With March 2014’s Patch Tuesday scheduled to come out only one day before the competition, attackers were always aware that there was a lot that could go wrong for them (but right for the rest of us!) at the last minute.
Vupen won’t be going home empty handed, however.
The company chalked up successes against Adode Reader, IE 11, Adobe Flash and Mozilla Firefox, for an impressive Day One prize haul of $300,000.
Vupen was also down to attack Apple Safari on OS X on Day Two at 11:00, but that attempt has been withdrawn
Apple’s Safari, which was the only browser that survived last year’s competition (albeit by default – no-one entered to attack it), will now face a single opponent, the ambitiously-named Keen Team, at 10:00 on Thursday.
The full results of Day One were was follows:
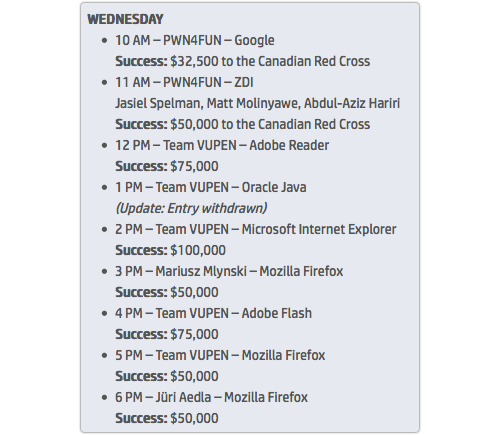
Mozilla’s Firefox had a bad day, pwned three times at a cost to the sponsors of $150,000.
Day One, by the way, started with a pair of Google-versus-HP hacks, called PWN4FUN, which raised $82,500 for the Canadian Red Cross, with the co-sponsors completing one hack each for an honourably even outcome.
Now, the race is on for the already-pwned products to produce patches (attackers must responsibly disclose how they did it as a condition of entry).
We’ll bring you the Day Two results tomorrow, when Chrome will be attacked twice, Safari once, IE 11 twice more, and Flash and Firefox once more each.
Quite a day of hacking ahead!
[*] Only kidding! Four inputs, two outputs.Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/7gpiwvi_UY4/