PWN2OWN for mobile devices – $300,000 in prizes for stealing data, eavesdropping or making covert calls
Imagine that you have a jailbreak for iOS 7 up your sleeve.
All you have to do is wait a while, until iOS 7 ships, and announce your jailbreak then.
 You’ll soon be enjoying the adulation of the whole jailbreaking scene, a writeup on Naked Security, and the prospect of a job/lawsuit (or both!) with/against Apple.
You’ll soon be enjoying the adulation of the whole jailbreaking scene, a writeup on Naked Security, and the prospect of a job/lawsuit (or both!) with/against Apple.
Or you could try for $50,000 from HP instead.
That’s just part of the prize money that’s up for grabs at the second Pwn2Own competition of the year, Mobile Pwn2Own, announced last week by HP’s Zero Day Initiative.
We covered what you might call the regular-sized Pwn2Own earlier this year, from the announcement of its $500,000 in prize money to the day by day results.
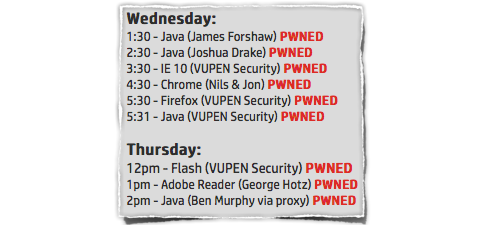
The outcome was a series of victories for the hackers, with HP ultimately paying out $480,000.
(The official rules limited the payout for a particular target to the first to pwn it, but HP ended up agreeing to pay all four of the entrants who “popped” Java, at $20k, ahem, a pop.)
The mobile competition
The Mobile Pwn2Own won’t be pitting vendor against vendor, so it isn’t a question of Android versus Windows Phone, or Safari versus Chrome, or Blackberry versus Nokia, aka Microsoft.
Instead, the prize money is divided up by attack vector, based on how you break in:
• Via physical proximity (prize: $50k)
You can use a wireless or a wired attack, using one (or, presumably, more) of Bluetooth, Wi-Fi, USB or NFC.
A successful attack “must require little or no user interaction,” so a dialog such as the one iOS 7 will soon be popping up to inhibit rogue USB connections would be a satisfactory mitigation:
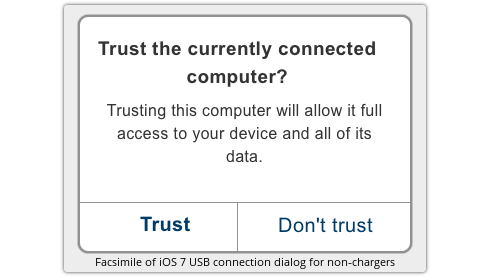
Earlier in the year, of course, researchers at showed at BlackHat how a booby-trapped iPhone charger could silently hijack your USB connection given the absence of such a pop-up warning.
• Mobile web browser (prize: $40k)
Some user interaction will no doubt be allowed here – someone has to decide to browse somewhere to get started, after all – but you won’t be allowed to assume the user will agree to or click on anything else.
There is no requirement in the rules for persistence, where the exploit remains active after the browser exits.
In any attack category, all you need to is one of the following: exfiltrate (i.e. steal and send to the outside world) information you aren’t supposed to get; silently make a long distance phone call; or eavesdrop a conversation.
→ The rules don’t say if “eavesropping a conversation” applies to cellular calls only, or even only to voice. If you are planning on eavesdropping to win a prize, you probably want to check in advance whether logging an instant messaging chat would count, or whether HP wants to see you listening in to phone calls made over the cellular voice network.
• Mobile Application/Operating System (prize: $40k)
Since each device will be in its default setup and configuration, with all available patches applied, you won’t be able to rely on third party apps that might or might not have been installed by the user, no matter how prevalent they might be.
• Messaging Services (prize: $70k)
You can attack by means of any of these: Short Message Service (SMS), Multimedia Messaging Service (MMS), or Commercial Mobile Alert System (CMAS).
The rules don’t say, but with “limited user interaction” permitted, it’s probably reasonable to assume that an attack can rely on users actually reading a booby-trapped message, but not on them following any instructions given in it.
• Baseband (prize: $100k)
Loosely put, the baseband is the part of a device that makes it a phone, or at least capable of connecting to a cellular network, so this vector of attack doesn’t apply to Wi-Fi only devices.
The value of this prize presumably reflects the comparative difficulty of coming up with a method to break in via the mobile network itself, rather than via USB cable or over the internet.
Choose your weapon
One you’ve picked your attack vector, you can choose to mount the attack using any one of an eclectic list of devices:
- Nokia Lumia 1020 running Windows Phone
- Microsoft Surface RT running Windows RT
- Samsung Galaxy S4 running Android
- Apple iPhone 5 running iOS
- Apple iPad Mini running iOS
- Google Nexus 4 running Android
- Google Nexus 7 running Android
- Google Nexus 10 running Android
- BlackBerry Z10 running BlackBerry 10
Entrants in each category go in to bat in randomly chosen order, designate the device on which they wish to mount their attack, and then have 30 minutes to pwn the chosen device via their chosen method.
The first to succeed in each category wins that category’s prize – and since there are five categories but nine devices, at least four devices will remain unowned.
What we may never know, if there’s a device (or an operating system) that no-one chooses for any attack, is whether it was avoided due to a lack of interest, or due to its recognised strength.
Pwn2Own, like many security tests, is good at telling you if a product has a security weakness, but doesn’t say much about each product’s strengths.
Oh, by the way, to enter, you need to be registered as a delegate at PacSec 2013 Conference in Tokyo, Japan, which takes place from 11-13 November 2013.
NB. Yes, the organisers have thought about the effect that demonstrating telephony-related exploits might have on the real world. Any exploit attempts that use radio waves must “be completed within the provided RF [radio frequency] isolation enclosure.”
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/O7RpUo2byBw/