RSA Conference 2015 in retrospect
 It’s the week after the week before, which means the RSA Conference 2015 in San Francisco is over.
It’s the week after the week before, which means the RSA Conference 2015 in San Francisco is over.
RSA, as it’s known, is the biggest computer security conference of the year, and it runs together with the biggest computer security trade show of the year.
We brought you some recorded-on-the-spot coverage during the event, with two podcasts straight from the Sophos booth:
(Audio player above not working? Download MP3 or listen on Soundcloud.)
(Audio player above not working? Download MP3 or listen on Soundcloud.)
By now, of course, most of the speakers, delegates and trade show attendees will already have returned home and be back to business as usual.
So we thought it would be fun to look back at a conversation we had with Grey Howe, of GreyRose LLC, an IT consultancy in Denver, Colorado.
Grey won a trip to RSA, courtesy of Sophos, through our community on Spiceworks.
He spent his week rushing between presentations, and, of course, visiting the Sophos stand, which is where we chatted to him.
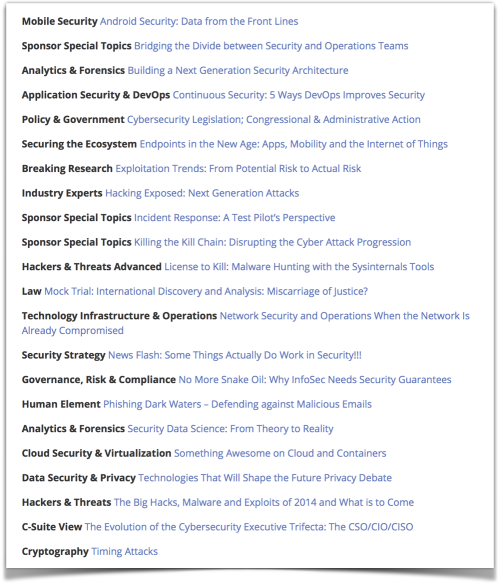
Choosing your presentations when you’re a delegate at RSA can be a daunting task, with some session slots featuring more than 20 parallel tracks.
For example, immediately after luncheon on Tuesday, 21 April 2015, you’d have faced this choice:
We asked Grey three questions, and here’s what he said.
Q. What was the most intriguing idea you heard at the conference, and why?
A. Grey chose something from one of the talks listed above, as it happens: Network Security and Operations When the Network Is Already Compromised.
The idea sounds a bit negative at first: instead of concocting a special way of working once you know your network is compromised, what if you assume it’s compromised all the time, and work as though the crooks have a pretty good idea of what you’re up to day by day?
In other words, instead of expecting the worst but preparing for the best, you expect the best, but prepare for the worst well in advance.
Of course, that doesn’t mean you need to carry out the sort of drastic actions every morning (such as resetting every password, or taking key servers offline) that you might when it was clear that an active attack was under way.
But it would mean that you’d never be stuck creating your security battle plans after the bombardment had begun.
Q. What was the weirdest idea you heard at the conference, and why?
A. Grey described a suggestion he heard – he didn’t say if the presenter was being thoroughly serious, or merely thinking aloud in jest – to make modern malware stand out more than usual.
The idea was this: a high percentage of unencrypted traffic is your friend.
That way, malware that tries to hide itself using Good Guy tricks, such as using TLS (HTTPS), will stand out like a sore thumb.
On the other hand, malware that tries to blend in will be unencrypted, so you can sniff it out conventionally.
Wow!
We’ll leave you to decide for yourselves why deliberately leaving things unencrypted, in the hope of improving the visibility of malware, is a terribly bad idea.
(That’s just a warning. We don’t think the speaker was suggesting you take that approach!)
Q. If you were King, what edict would you issue to improve security?
A. Grey went for an old-school movie answer here, back to 1989: Be excellent to each other.
In particular, don’t fall back on the excuse that what you don’t know won’t hurt you, or at least that if you don’t know it, you won’t have any compunction to do anything about it.
That’s because even if you aren’t terribly fussed about your own network, computers, users or customers…
….insecurity in your network is likely to put everyone else at risk.
This neatly echoes our own conclusion in the Chet Chat 195-and-a-half podcast above:
It seems that we’re getting to the point where […] security isn’t just an “us and them.” […] It’s about adapting your behaviour in a way that helps you, and helps everyone else at the same time, which is […] the best sort of altruism, isn’t it?
So there you have it: two motifs for security in what’s left of 2015:
• Practise the best sort of altruism.
• Be excellent to each other.
After all, if we don’t look out for one another, the crooks certainly aren’t going to do it for us!
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/hTiRHxOXdMs/