SEA attempts to hack Facebook and other MarkMonitor domain customers
 If you find a good tactic and it works you stick with it, right? That certainly seems to be the case for the Syrian Electronic Army (SEA).
If you find a good tactic and it works you stick with it, right? That certainly seems to be the case for the Syrian Electronic Army (SEA).
Early in 2013 we watched them phish major media organizations in succession.
More recently they have moved on to more sophisticated techniques, mixing together social engineering, phishing, email hijacking and domain hijacking.
Today, it was Facebook’s turn. It appears the SEA were able to gain access to an administrative panel at DNS provider MarkMonitor.
MarkMonitor prides itself in providing brand protection services, including DNS hosting.
Despite the blemish from today’s SEA shenanigans, it can still stand reasonably tall because it was able to stop the attack while it was still in progress.
They weren’t able to totally prevent the incident, however.
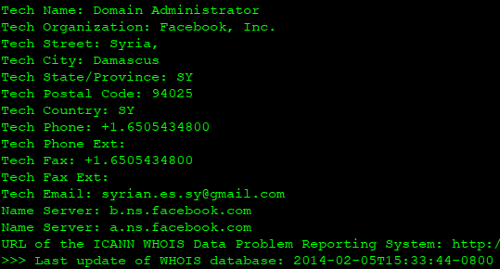
The SEA began by altering the contact details in Facebook’s WHOIS records to allow them to authorize a transfer to an account that would allow them to make further changes.
You can see the records were altered at 2014-02-05T23:33:44 UTC. Here in Vancouver that was on Wednesday at around 3:30 pm.
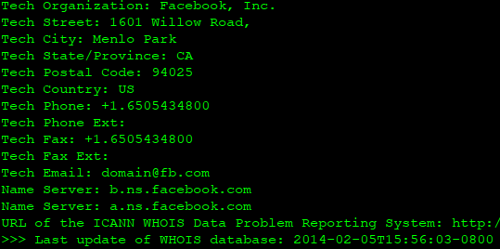
More important to note is that the name servers still point at the legitimate nameservers for Facebook.com.
I was watching this in real-time and there appeared to be a struggle for control around 23:49 UTC, with MarkMonitor winning the war at 23:56 UTC.
The SEA Twitter account also claimed to have been able to potentially alter domain records belonging to Yahoo!, Google and Amazon.
All of these companies appear to use MarkMonitor for their DNS services.
According to The Next Web, MarkMonitor would neither confirm nor deny whether Facebook is in fact a customer of its services.
Pro tip to the PR people at MarkMonitor: Don’t refuse to confirm things that are obviously true if you don’t wish to make a statement.
Say something like, “We can’t comment on things that involve an ongoing investigation by law enforcement.” Far classier.
The real challenge in these situations is that the design and protocols of the Internet were not designed to defend against malfeasance.
 To a degree we are like the little Dutch boy in Hans Brinker attempting to save ourselves by plugging holes in the dike.
To a degree we are like the little Dutch boy in Hans Brinker attempting to save ourselves by plugging holes in the dike.
We must bootstrap the Internet into modern times by taking things like DNSSEC seriously.
Stealing someone’s password or convincing an innocent customer service representative you are someone else should not be sufficient to take over someone’s online identity.
Stay vigilant, folks, and look into what your organization’s DNS provider offers in the way of protection.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/EUL_4G96vSo/