Sending a "Heartbleed" password reset email? Please don’t include a login link!
 With all the buzz about resetting your passwords caused by the “Heartbleed” bug, you can imagine what cybercrooks are thinking.
With all the buzz about resetting your passwords caused by the “Heartbleed” bug, you can imagine what cybercrooks are thinking.
TIME TO GO PHISHING!
Fortunately, many people these days know to be careful of password reset emails, at least those that helpfully provide a link that takes you to what looks like a login screen.
But it’s easy to make a mistake.
If you were thinking, “Hey, maybe I should change my example.com password, just in case,” and then an email arrives claiming to be from example.com that takes you to a login screen that looks just like example.com…
…you could be forgiven for just following habit and trying to login.
Of course, if you aren’t actually on example.com, you’ve just given away your login details to a cybercrook.
(Now you really do need to change your password, on the real site, and pretty jolly quickly!)
The flipside of all of this is as follows: when you need to send a genuine password reset warning to your customers, please don’t put links to your login page in the email itself.
It’s much more convenient if you do give an easily-clickable link, and there is no technical or legal reason not to do so.
But from a behavioural point of view, it’s so much better if you don’t, because you aren’t softening up your customers up to click on the sort of links that scammers love.
Simply put, it’s a bad look.
If no legitimate sites ever put login links in their email correspondence, then deciding whether login links are good or bad becomes trivial: they’re bad, and that’s the end of it.
So we were a little disappointed, if not surprised, to receive a “Will you look at this?” message from Naked Security reader Paul, copying us in on a password reset email from popular Internet of Things website IFTTT.
IFTTT stands for “if this, then that,” and it seems to be a catchphrase for popularising simple computer programming concepts amongst non-programmers who own electronically tweakable devices – light bulbs, for example – that have traditionally been controllable only by someone in the room at the time.
Instead of saying to yourself, “I am entering my house; I’ll turn on the light in the passage,” you pre-program your intelligent light bulb controller with “IF my car enters the garage AND it is night THEN turn on the hallway light.
In a world where your car, your garage and even the individual light bulbs in your house are online, you’d think that following security best practice would be more important than ever.
And you’d be right, making it a pity that IFTTT, of all online communities, sent Paul one of these:
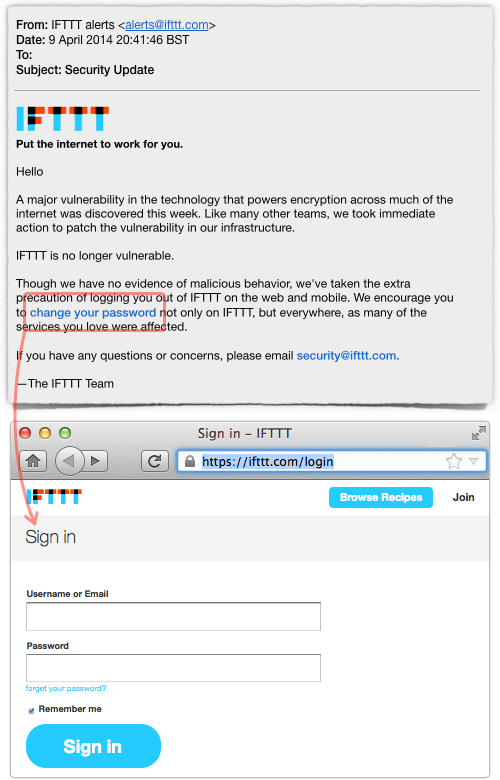
We admit that all the signs are there to help you realise this is legitimate, from the URL you see when you hover over the link in the email to the HTTPS certificate of the login screen to which the link takes you.
So this isn’t an egregious error, or even, if the truth be told, a terribly dangerous one.
But we’d like to urge any of you who are thinking of sending out “heartbleed” password reset emails: please avoid those login links.
Help us to help everyone get geared up to avoid phishing attacks.
Image of Gone Fishing sign courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/eVpWyJdxkR8/