SharePoint Online scam – sadly, phishing’s not dead
Most of us can recognise most spam when we see it – emails we didn’t ask for from companies we’ve never heard of selling us products we aren’t interested in at price points we simply couldn’t care less about.
Having said that, a lot of spam isn’t simply unwanted email – it’s dangerous, too, because it contains not only links or attachments you don’t want but also content that deliberately tries to put you in harm’s way.
One of the most prevalent types of outright scammy spam is phishing, for which the simplest definition we’ve come up with is this:
Phishing is the word used when a cybercriminal sends you some sort of electronic message to trick you into doing something insecure.
The “fishing” metaphor, of course, refers to the idea of getting you on the hook and then reeling you in.
Phishing gets its curious spelling from a 1970s crime known colloquially as phreaking. Hackers figured out how to make free calls using a variety of illegal tricks to “freak out” the telephone system, for example by playing special musical tones down the line. Freaking the phone system morphed into phreaking, and by analogy, fishing for passwords and other personal data became known as phishing.
One of the best-known flavours of phishing doesn’t bother trying to sneak malware onto your computer, but instead gets you to submit personal information from your computer.
Typically, this means tricking you into visiting a website that ultimately leads you to a login page that looks just like one you see often, where you enter your username and password to go further…
…only to realise, too late, that you just put your very own login credentials into an unknown and untrusted website.
As with spam in general, however, lots of people assume that these password-stealing phishing emails are more of an annoyance than a danger, because they’re often very obvious.
The “obvious” features people look out for in password-leeching emails include:
- Mistakes of spelling and grammar. Phishing emails often look unprofessional, unlike the genuine emails they are pretending to be.
- Incorrect or vague greetings. Phishing emails often say “Dear Sir/Madam” or “Dear Customer” because the crooks don’t actually know who you are, something a genuine email sender would know.
- Errors in regional usage. Phishing emails may use the wrong currency symbols, an unusual date format or an unexpected word that a genuine sender would get right.
- Incorrect or unlikely web links. Phishing emails generally rely on getting you to click through to a web domain that’s different from the genuine site.
Not all phishers make mistakes
But not all phishers make all these mistakes, so that if you rely heavily on the presence of obvious mistakes to make phishes obvious, you’re more likely to get caught out.
That’s because crooks don’t have to gain fluency in your language, learn your business jargon or understand your culture to come up with simple and unexceptionable phising messages.
Here’s a real-world example of keep-it-pretty-normal phishing campaign that showed up many times recently in our personal account as well as in SophosLabs spamtrap email accounts:
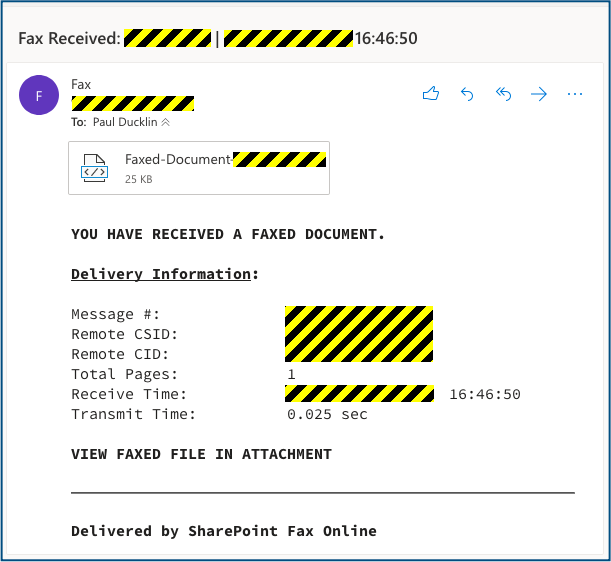
By sticking to plain-and-simple English and relying on the sort of stripped-down message templates that many automated message delivery systems use, crooks can surprisingly easily create messages that pass the regional usage test, pass the customer greeting test, and pass the spellos-and-typos text.
In this case, there’s an extra bit of trickery aimed at distracting you from the incorrect web link, too.
The dodgy link that the crooks want you to click, plus an official-looking logo, is added as an HTML attachment, rather than included inline in the email.
Opening the attachment feels innocent enough, because it’s supposedly just the document itself – presumably a mostly-harmless image file such as a JPEG or a PNG.
What you get, however, is a request to login to Sharepoint to view the image via the cloud:
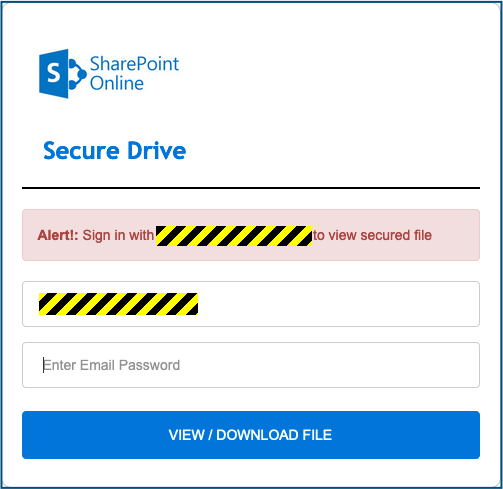
Your warning bells ought to go off loudly here, because the appearance of a login screen – what’s known in the jargon as an interstitial page, which is just a fancy pseudo-Latin way of saying “sitting between A and B” – is not precisely what was promised in the original email.
The email implied that the attachment contained the actual image, but instead it contained an indirect way of getting to the image.
Of course, the cloud has trained us to expect exactly that sort of thing – we regularly talk about “sending” and “receiving” images and documents via email even when we’re not sending the files themselves, but instead handing out links where we’ve dumped them into cloud sharing services.
Note that in this phish, there is no easy way to see the dodgy link that the crooks are using to harvest your password:
- The login form is loaded as a local HTML file that’s attached to the email, so it doesn’t have a giveaway external link you can check before you open it.
- Your browser doesn’t show you where your data will go before you click the
[VIEW/DOWNLOAD]button.
You can’t hover over the submit button in a web form to show you where your data will get sent.
Yes, that’s bad; and no, we don’t know why browsers don’t show you – it would be great if they did.
What next?
In this campaign, any password you put into the form would end up in the hands of the owners of an ordinary-sounding server name in the top-level domain .XYZ.
The good news is this case is that the crooks didn’t bother to get an HTTPS certifcate for their domain, so they had to use a web link starting http://, which should provoke a warning in your browser about the lack of encryption for submitted data.
Firefox, for example, says:
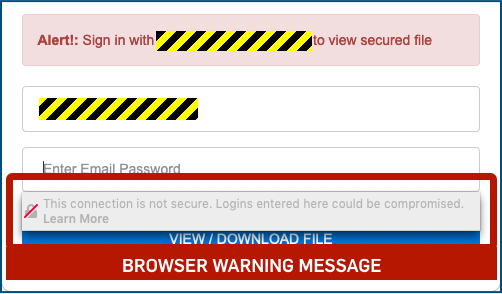
Watch our for security warnings – even if this were a legitimate email and and a genuine website, you should never put form data – especially passwords – into a non-HTTPS form, because anyone along the way could then sniff out both your password and any authentication reply that comes back.
As well as heeding warnings, it’s also worth learning how to use your favourite browser to check out the HTML that’s being displayed by the form, because that will reveal the server that your data will be sent off to.
In Firefox, for instance, if you right-click on the password field and choose Inspect Element, you will open up the HTML of that field and the FORM of which it’s a part, like this:
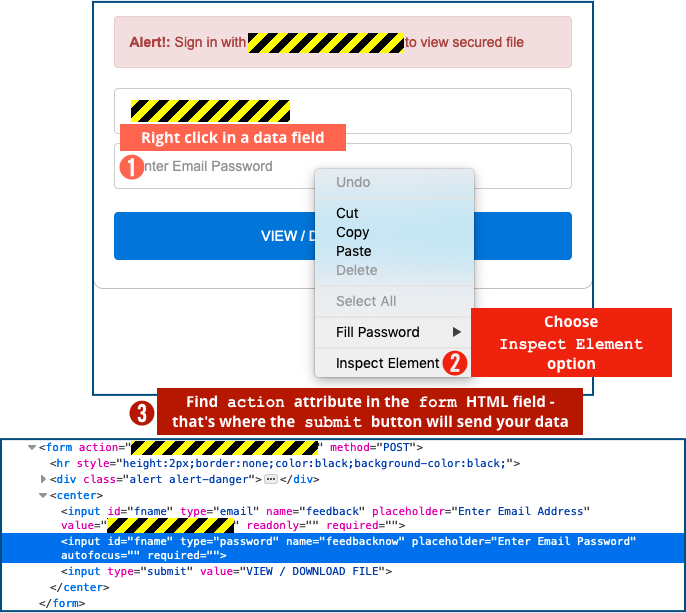
Look for the opening tag, which will look something like FORM ACTION=..., where the ACTION text specifies the URL to use when the form’s [Submit] button is clicked – that’s where your data is headed next.
In this case, the form not only has a non-HTTPS link, but also has a server name that doesn’t seem to have any obvious connection with Sharepoint Online.
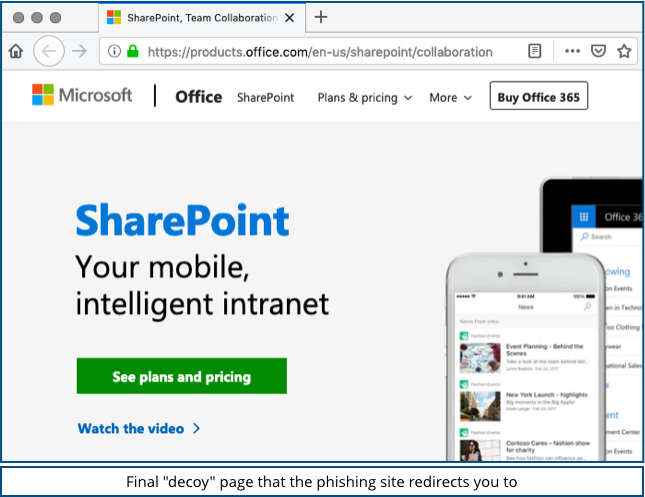
By the way, once you click [Submit], this phishing site redirects you to a genuine, if only vaguely relevant, Microsoft Sharepoint page, presumably as a rather weak decoy to convince you that you are in nearly, but not quite, in the right place:
What to do?
- Don’t enter passwords into login pages that show up after you click on a link in an email. Bookmark the official login pages of your favourite sites, or type the URLs into your browser from memory.
- Avoid opening attachments in emails from recipients you don’t know, even if you work in HR or accounts and you use attachments a lot in your job.
- Set up an “ask the experts” email address inside your organisation, e.g.
[email protected]. That gives your users a quick way to ask for advice about unexpected emails and unsolicited attachments. - If in doubt, don’t give it out. People do still send faxes, but it’s rare enough that you ought to be suspicious. Stop and think before you connect – ask for a second opinion if you aren’t sure.
- Consider using both email and web filtering, so you can block both incoming links and outbound clicks.
- Don’t ignore browser warnings about insecure sites and data input forms. Unencrypted web pages are typically the sign either of a lazy crook or of a site operator who’s not up to speed on security.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/_GauxhRMdVU/