Skype bug could expose users to malicious code attack
The latest version of Skype for Windows contains a security vulnerability that allows attackers to inject potentially dangerous code into a user’s phone session, a German security researcher has reported.
The XSS, or cross-site scripting, vulnerability in Skype 5.5.0.113 is the result of the voice-over-IP client failing to inspect user-supplied phone numbers for malicious code, researcher Levent Kayan said. As a result, attackers might be able to exploit the bug to inject commands or scripts that hijack the machine running the program.
“An attacker could for example inject HTML/JavaScript code,” Kayan wrote in an advisory published on Wednesday. “It has not been verified though, if it’s possible to hijack cookies or to attack the underlying operating system.” An attacker might also exploit the vulnerability to remotely execute malicious JavaScript files on external websites, he said.
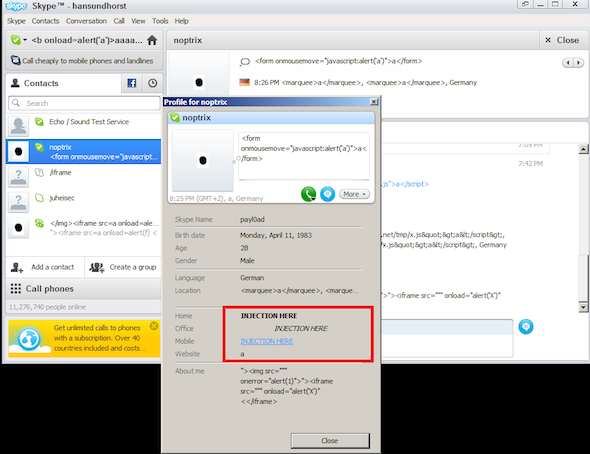
A screen shot from Kayan’s website showing the injection bug in action
The unsafe content is displayed when users view a booby-trapped profile. The malicious profile is created by inserting a JavaScript command or web address where a phone number is expected. The reported vulnerability is eerily reminiscent of an XSS bug Kayan reported in an earlier version of Skype last month. Skype representatives didn’t immediately respond to an email requesting comment on the persistent code injection vulnerability.
Such vulnerabilities open the possibility of creating self-replicating attacks if they can be used to target users contained in each victim’s contact list. As each new user is exploited, the worm spreads virally by attacking a whole new set of people. A vulnerability reported in May for Mac versions of Skype was described as wormable, though there are no reports it was ever exploited in the wild. It’s unclear if the current vulnerability is also self-replicating.
Microsoft is in the process of acquiring the popular internet-based phone service. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2011/08/22/skype_security_bug/