“Smarter, shadier, stealthier” – Security Threat Report 2014 helps you understand the enemy
 Our latest Security Threat Report is out!
Our latest Security Threat Report is out!
It’s a free download (no registration required), and we think you’re going to love it, because it paints a fascinating picture of the evolving threat from cybercrime.
Of course, the report isn’t all doom and gloom about the Bad Guys.
It includes a range of security tips, and a section on proactive protection, entitled Staying Ahead of Today’s Most Sophisticated Attacks.
The report isn’t just about Windows and Windows malware, either.
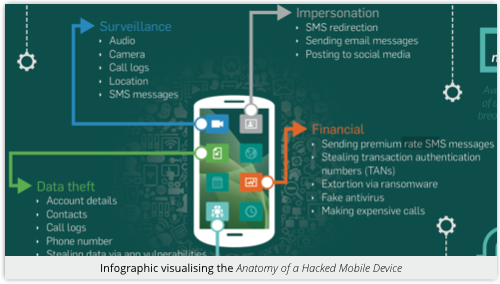
You’ll find a wealth of information about how the cybercrooks are broadening their attack horizons to the Mac, Linux and Android platforms, too.
This is important material because it necessitates that we broaden our defensive horizons in reply.
The report also looks the technology and the underground economy behind crimeware tools such as exploit kits, botnets, click fraud, ransomware, and more.
As well as being a fascinating read, the Security Threat Report 2014 will help you to understand and to protect yourself against an enemy that is becoming ever smarter, shadier and stealthier.
What we suggest is that you grab a copy of the report, open it on-screen, and then take a listen to the short podcast below, as Sophos experts Chester Wiskniewski and John Shier talk you through it.
Their passionate and well-informed commentary will give you plenty of food for thought:
![]()
(Audio player not working? Download MP3, or listen on Soundcloud.)
By the way, if your job includes promoting better security to other people, for example through talks and articles, don’t miss the Press Kit that goes along with the Threat Report.
The Press Kit includes standlone images from the report that you can use in your own presentations; infographics you can use as supporting evidence in your own articles; and a selection of white papers for further reading:
- Dont Let Data Loss Burn a Hole in Your Budget
- Five Stages of a Web Malware Attack
- Simple Security Better Security
- The Rise of Mobile Malware
- Who’s Snooping on Your Email
Enjoy the report, and don’t be shy to let us know what you think in the comments below. (You may comment anonymously.)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/fyEJfszMfe4/
