Sony Pictures breached
 Last week, the big “did they or didn’t they” story was an alleged giant-sized hack on Sony’s PlayStation Network (PSN).
Last week, the big “did they or didn’t they” story was an alleged giant-sized hack on Sony’s PlayStation Network (PSN).
Crooks published what they claimed were sample usernames and passwords from PSN and other networks, which they named as Windows Live and 2K Gaming.
As we pointed out at the time, the data certainly had a reek of deceit about it, and not just because Windows Live isn’t called that any more, and 2K Gaming has never gone by that name.
That’s the problem with hacking claims.
In a world where some crooks can avoid notice altogether as they scoop up genuine payment card numbers for weeks or months, other crooks can acquire instant notoriety by hacking into little or nothing.
The message is the medium, or something.
So it’s hard to know what to make of this week’s news about a claimed megahack at Sony Pictures Enterainment (SPE).
A hacking crew going by #GOP, supposedly short for Guardians of Peace, is suggesting it has managed to pop up a fear-and-loathing notice on computers inside SPE’s network, and has published an unstructured dump of supposedly-stolen data to “prove” the extent to which it has owned SPE:
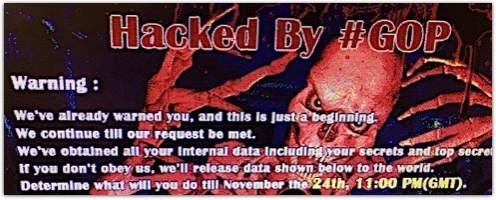
Blunt words, big claims, bold threats.
SPE, understandably, seems to have closed ranks so far.
As a result, many, if not most, reports (including this one) are based on the above image that was posted on self-proclaimed “no-limits” viral image sharing site Imgur.
The person who posted the screenshot says, simply:
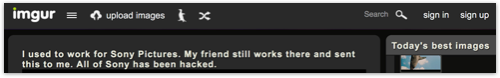
I used to work for Sony Pictures. My friend still works there and sent this to me. All of Sony has been hacked.
The image includes multiple links to a file called SPEData.zip.
Sony’s security history
Sony has been in the computer security spotlight several times before.
The company famously shot itself in the foot in 2005 when it snuck an anti-piracy rootkit onto some of its music CDs and installed it without authorisation, leading to malware that hitched a free ride on the badly-coded rootkit.
Sony infamously prosecuted well-known hacker George Hotz for revealing how to jailbreak some of its consoles so they could run Linux, a feature that Sony itself used to support.
And Sony was the victim of a series of attacks against its Sony Online Entertainment network in 2011, making it the first member of what we’ve satirically dubbed the 100 million club of companies that have suffered breaches in which that many records, or thereabouts, were purloined by crooks.
Incidentally, PSN really was breached back in 2011, along with SOE and Quriocity (now called Music Unlimited), ultimately costing Sony $15m in a legal settlement, even though Sony itself was undeniably the victim of a crime in all those hacks.
So, has Sony really been breached again, and, if so, is the breach really as dramatic as the #GOP hackers claim?
Reports suggest that at least some of SPE’s network, including email, is currently offline.
Mashable, for example, published an email auto-reply from one of SPE’s press accounts that said:
Our email system is currently experiencing a disruption.
What to do?
The usual reaction after a breach is to rush out and change your password.
But that’s because data breaches often involve password hashes, meaning that the crooks can start aggressively cracking the weaker passwords in the list offline.
Of course, if #GOP is telling the truth and has owned SPE entirely, changing your password right away might not be enough.
After all, if the crooks really are that good, they may be able to snoop the very HTTPS session in which you change your password and thus acquire your new one.
So the very act of trying to boost your security might actually make things worse. (We faced a similar dilemma after the Heartbleed bug, where we had to advise people to change their passwords only after vulnerable servers had been patched.)
As Naked Security’s own Mark Stockley commented:
There are so few details available at the moment that even if you do change your Sony passwords now, you may need to change them again, depending on what Sony eventually finds out
But, whatever you do, if you’re using a password on a site owned by Sony AND reusing that password on any other websites…
…well, you shouldn’t be re-using passwords anywhere, anyhow, so change all those passwords anyway. Right now!.
Find out why passwords matter, and how to choose good ones, in our Proper Passwords video:
→ Can’t view the video on this page? Watch directly from YouTube. Can’t hear the audio? Click on the Captions icon for closed captions.
The bottom line
Even if you dislike Sony because of its security history, I urge you to to reserve judgement in this case until the facts are known.
Wagging fingers at Sony would be poor form if, indeed, SPE staffers have just been bombarded with a message from cybercriminals threatening harm “if you don’t obey us”…
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/lKlTz-Hmb8Q/