Swiss CERT publishes reveals details of defence contractor hack
Swiss defence contractor RUAG and the country’s GovCERT have revealed the details of a 2014 network breach in which attackers got access to a stunning 23 GB of data.
RUAG’s business covers defence, aerospace (including drones), and ammunition technology, making it a very attractive target for espionage.
The breach was only discovered earlier this year, with to very little fanfare until earlier this month, when NZZ am Sonntag reported that the attackers used their access to RUAG to also gain access to the secret Swiss DRA10 special forces unit (in English via Swissinfo here).
MELANI, the Reporting and Analysis Centre for Information Assurance that operates under GovCERT, has now published its analysis of the hack.
The reason for publication, the organisation explains, is to “provide insight and protection. We decided to publish this report to give organisations the chance to check their networks for similar infections, and to show the modus operandi of the attacker group”.
The SANS Institute’s Rick Wanner notes that the attack doesn’t seem to have been particularly stealthy or advanced. Its success came instead from patience: once they had access to the RUAG network, they spent time identifying targets they were interested in.
The attackers used “a target IP list and extensive fingerprinting before and after the initial infection. After they got into the network, they moved laterally by infecting other devices and by gaining higher privileges”, the report says.
In particular, they put a lot of effort into getting access to the RUAG network’s Active Directory, “as this gave them the opportunity to control other devices, and to access the interesting data by using the appropriate permissions and group memberships”.
They deployed malware from the Turla family, which makes Russia a reasonable suspect (although the report explicitly avoids attribution).
Data was exfiltrated over port 80, which was also used for command and control to deploy new attacks.
From the report:
“Inside the infiltrated network, the attackers used named pipes for the internal communication between infected devices, which is difficult to detect. This way, they constructed a hierarchical peer-to-peer network: some of these devices took the role of a communication drone, while others acted as worker drones.
“The latter ones never actually contacted any CC servers, but instead received their tasks via named pipes from a communication drone, and also returned stolen data this way. Only communication drones ever contacted CC servers directly.”
The CC servers were carefully chosen (and according to the MELANI report, most have now been cleaned up).
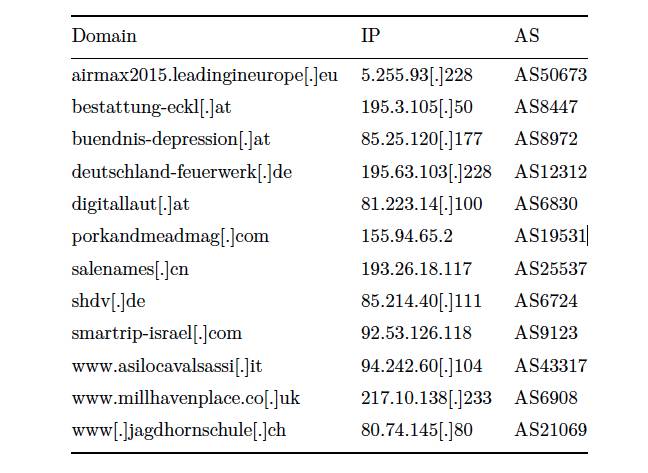
CC servers used in the RUAG attack
While none of the recommendations are groundbreaking, the report provides a more detailed breach study than is normally released after an attack. ®
Sponsored:
Cluster speeds molecular dynamics research with NVIDIA GPUs
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2016/05/24/anatomy_of_a_breach_swiss_cert_publishes_analysis_of_ruag_attack/