Syrian Electronic Army hacks Forbes, spills 1M user records – here’s what you need to know
The hacking crew SEA – short for Syrian Electronic Army – infamously tried and failed to make off with Facebook’s website last week.
That wasn’t an attempt to break into Facebook’s empire, but rather an attempt to relocate it by tricking one of Facebook’s service providers into diverting Facebook’s web traffic to imposter servers.
Fortunately for Facebook – and, no doubt, fortunately for the sales guys working the Facebook account at the service provider! – the attack did not succeed.
But he SEA got a lot further this week with business news site Forbes, breaking into the company’s network, and posting “proof that we were there” screenshots, snapped from one of Forbes’s WordPress systems:
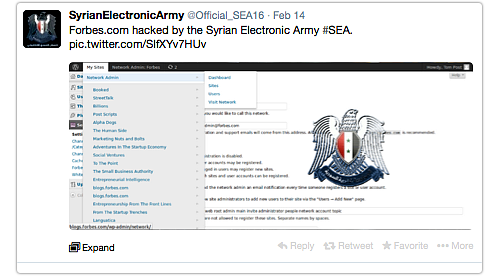
Forbes.com hacked by the Syrian Electronic Army #SEA. pic.twitter.com/SlfXYv7HUv
It turns out that the SEA didn’t just get to look around – the hackers were able to steal a massive user database containing more than 1,000,0000 records.
→ The file ultimately released by the SEA contained 1,057,819 unique usernames. Most reports give a number of 1,071,963, which is also correct, being the number of lines in the file.
The story gets an intriguing kink at this point.
The SEA first announced its intention to sell the file:
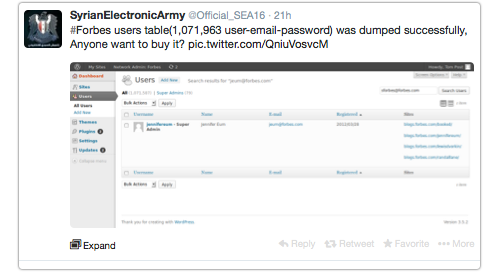
#Forbes users table(1,071,963 user-email-password) was dumped successfully, Anyone want to buy it? pic.twitter.com/QniuVosvcM
Strictly speaking, the file didn’t actually contain passwords, but only scrambled representations of them (about which more in a moment), something that may have made the data less valuable to any potential purchaser.
At any rate, the SEA then quipped:
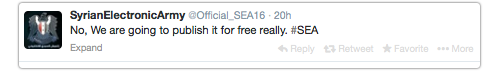
No, We are going to publish it for free really. #SEA
This was followed up with:
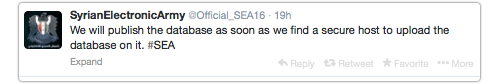
We will publish the database as soon as we find a secure host to upload the database on it. #SEA
If “secure” sounds like a curious word for a server on which you plan to offer openly to the public a bunch of data that is supposed to be private, don’t forget that the Holy Trinity of computer security embraces not just confidentiality, but also integrity and availability.
To data dumpers like the SEA, “availability” means that it should be difficult for anyone else on the internet to block access to the data that’s being leaked, in order to maximise exposure.
Shortly after that, the dump found a home where anyone who wanted could grab a copy:
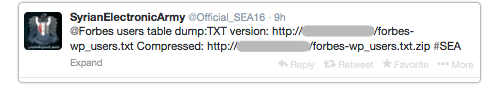
@Forbes users table dump:TXT version: http://[redacted]/forbes-wp_users.txt Compressed: http://[redacted]/forbes-wp_users.txt.zip #SEA
What was stolen
The records in the data dump look like this (data has been deliberately altered):
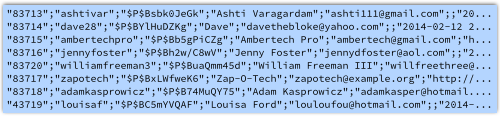
Each record seems to have the following fields:
1 = Numeric ID 2 = Username 3 = Stored password data 4 = Display name 5 = Email address 6 = Website or other URI 7 = Timestamp (one-second granularity) 8 = Unknown 9 = "0" 10 = Full name 11 = "0" 12 = "0"
The eighth field is intriguing, as it is almost always missing, except in about 1% of the records.
When it appears, it is either a 32-character hexdecimal value (data has been deliberately altered):
8249a4a6727633d03ef1f01d5a91f917 61b227e2e16d8de24ffbb56f2455aaa6 22767469dc768fb035665c96a6c1817e 869d188a08eed15bc366e41ff7c8a244 3387e857079e715117166b15f6f1b5c3
Or a 20-character encoded string using a larger character set:
yWq0FD70DFYVTmIN99Gn yzRKBpPv6ZWC4Ov0K0g8 K79ZHfc1sotssgyPGuTR N7GPE33TM1v4fy0UICna A2y0ka6nOgUmGAj711XC
We can’t tell you what that data is for (if you know, or wish to speculate, please tell us in the comments!), but as the field is blank 99% of the time, we’ll focus on the golden nugget in each record.
The trophy data
The trophy data that could get the crooks into your account, or into other accounts if you have re-used passwords, is field three, the stored password data:
$P$Bsbk0JeGkxxxxxxxxxxxxxxxxxxxxxx $P$BYlHuDZKgxxxxxxxxxxxxxxxxxxxxxx $P$Bb5gPiCZgxxxxxxxxxxxxxxxxxxxxxx $P$Bh2w/C8wVxxxxxxxxxxxxxxxxxxxxxx $P$BuaQmm45dxxxxxxxxxxxxxxxxxxxxxx
But how is the password data stored?
When Forbes announced its breach, it published the following statement on Facebook:
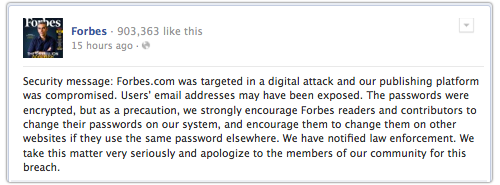
Security message: Forbes.com was targeted in a digital attack and our publishing platform was compromised. Users’ email addresses may have been exposed. The passwords were encrypted, but as a precaution, we strongly encourage Forbes readers and contributors to change their passwords on our system, and encourage them to change them on other websites if they use the same password elsewhere. We have notified law enforcement. We take this matter very seriously and apologize to the members of our community for this breach.
If you remember, we took Adobe to task, when it was breached last year, for saying that its passwords were “encrypted” when we assumed it meant “salted and hashed.”
It turned out that Adobe’s passwords were encrypted, all with the same key, and using the wrong sort of encryption mode (Electronic Code Book, which doesn’t disguise repetitions such as two users with the same password).
But this time, we can happily take Forbes to task, as the passwords were salted and hashed, not encrypted.
It’s a pity Forbes didn’t say so, and give explicit detail on how the salting-and-hashing had been done.
That would have given a useful indication of how likely it is that password crackers will be able to recover individual passwords by simply trying over and over until they hit the jackpot.
That sort of attack is called a dictionary attack (when you use a giant list of likely passwords, e.g. a dictionary), or a brute force attack (when you use an algorithm to generate passwords following a pattern such as AAAAA to ZZZZZ).
How the passwords were hashed
Fortunately, we can tell you – and, of course, Forbes, who didn’t seem to know when it issued its breach notification – how the passwords are stored.
They use what’s called PHPass Portable format, and each stored password field is deconstructed as follows:
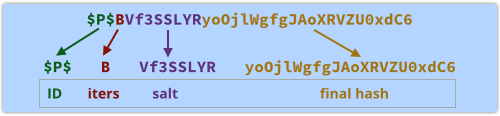
The $P$ denotes the PHPass Portable format, which uses a variable number of iterations, a 6-byte random salt, and the MD5 hash function.
B stands for 13, and means that the passwords use a loop of 213, or 8192, iterations of the MD5 hash in order to stretch out the computation time to slow down brute force attacks.
The next 8 bytes are a 64-bit encoding of the 6 random salt bytes.
The last 22 bytes are a 64-bit encoding of the final 16-byte output from the iterated hash function, which runs like this in pseudocode:
salt = six_random_bytes() hash = MD5(salt + password) for i = 1 to 8192 do hash = MD5(hash + password) end data = "$P$" + "B" + encode64(salt) + encode64(hash)
The encode64() algorithm is similar, but not exactly the same as, base64: each three bytes of input (3 x 8 bits) are transcoded into four bytes of output (4 x 6 bits).
Since six bits can produce 64 distinct values (26), each value can be represented by a single plainly-printable ASCII character: PHPass uses dot, slash, 0-9, A-Z and a-z.
Can the passwords be cracked?
You can “work backwards” from the Forbes datatbase to recover the passwords, but you need a lot of computing power, or time, or both.
Strictly, of course, you don’t work backwards, because hashes are deliberately designed to be non-reversible.
Instead, for each record, you extract the salt, and then plug the salt, combined with every password from a long list, into the algorithm above.
If at any point you get a match, then the password you just tried is the one that the user chose, and you have cracked that user’s account.
The large number of iterations here – 8193 invocations of the MD5() hash function for every password attempt for every user- is good, since it makes this attack 8000 times slower than checking a simple password hash.
And the salt means that even if two users choose the same password, the two final hashes end up completely different, so each user’s password has to be cracked separately: you can’t use a precomputed password-to-hash table.
→ That’s why [at the time of writing, 2014-02-16T00:20Z] you probably haven’t yet seen any extensive lists analysing the passwords in this breach, which you almost certainly would have if a simpler hashing system had been used.
How well did forbes.com users choose?
Despite the fact that well-chosen passwords are hard to crack here due to the 8193 iterations needed to test each password against each user, we can tell you that plenty of users in the list have made poor password choices.
It took us just two hours, using one core of a vanilla laptop, to crack approximately one-quarter of the passwords of the 500 or so Forbes employees in the database.
We somehow felt it was fairer to start with the forbes.com addresses, since it was Forbes that was breached.
Amongst other obvious choices, there was one password, one sunshine, three with changeme (why didn’t you!), and fifteen with welcome1.
Astonshingly, 73 Forbes staffers (more than one-eighth of the list) had chosen a password consisting of their company’s name, forbes, followed by zero to four digits. 1 and 123 were the most common suffixes.
One chap had gamely tried “elite” spelling, where you swap Os for zeros, Es for threes, and so on.
Warning: that’s not good enough – password cracking software knows perfectly well that f0rb3s is just another way of spelling forbes.
What to do?
- If you are a Forbes user, change your password now. (Or delete your account.)
- If you have used the same password on other accounts, change them now and DON’T DO THAT AGAIN.
- Choose a complex password so the crooks will crack other people’s passwords first.
- Read our article Serious Security – How to store your users’ passwords safely.
Forbes did the wrong thing by getting breached in the first place, and by letting the SEA make off with its password database.
And while the the 8193-iteration MD5-based hashing system described is a little short of modern best practice (try a stronger hash that takes longer to calculate, with more iterations), it’s better than Adobe’s disastrous “one key to encrypt them all” system.
So there’s your silver lining.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/vrGIF-2demU/