8 Free Tools to Be Showcased at Black Hat and DEF CON
Image Source:Adobe Stock (@kasto)
New research shows that for a growing number of enterprises now, passwords alone are not enough and they instead are combining strong passwords with two-factor authentication (2FA).
The study – released today by ThumbSignIn, market intelligence firm One World Identity and IAM provider Gluu – queried nearly 75 top IT and security managers, including C-level executives and vice presidents from various industries including finance, IT, and education. The survey analysis was also based on conversations with many of the top executives.
Vivek Lakshman, vice president of Innovation at ThumbSignIn, says 36% of the respondents depend on passwords plus 2FA, just slightly below the 40% of organizations that still employ passwords-only.
“There’s no question that passwords plus 2FA [two-factor authentication] is better than passwords-only,” says Andrew Shikiar, executive director and chief marketing officer of the FIDO Alliance. “People need to remember that this is a journey, it’s not a matter of flipping a switch and everything will be passwordless.”
ThumbSignIn’s Lakshman acknowledges that there are many challenges ahead in moving to passwordless authentication. In the study, for example, 76% of respondents say the complexity of implementation is a top-of-mind issue when they deploy biometrics or 2FA.
Interestingly, a full 100% say they are more interested in biometrics for the user experience than they are for security purposes. Only 75% are interested in biometrics for security.
“While that 100% number was surprising, we’re finding that a lot of companies are looking at biometrics as a top-line business opportunity,” says FIDO Alliance’s Shikiar. “Companies view biometrics as a better way to get people using their services and enhance the overall brand experience.”
Even with the recent Capital One hack and the ransomware events at city governments, the industry has been making some important progress. He points to the emergence of FIDO2 earlier this year, which offers browser support for passwordless authentication, notes Lakshman.
And this week’s study found that 64% of respondents consider FIDO “necessary” or a “good-to-have” standard. Another finding from the study: in the next few years, passwordless biometrics (21%) will be the second-fastest growing authentication method behind 2FA (29%).
Related Content:

Black Hat USA returns to Las Vegas with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions, and service providers in the Business Hall. Click for information on the conference and to register.
Steve Zurier has more than 30 years of journalism and publishing experience, most of the last 24 of which were spent covering networking and security technology. Steve is based in Columbia, Md. View Full Bio
Article source: https://www.darkreading.com/endpoint/more-companies-dont-rely-on-passwords-alone-anymore/d/d-id/1335398?_mc=rss_x_drr_edt_aud_dr_x_x-rss-simple
Cloud applications have enabled employees to send data across all corners of the Internet, to any number of third parties. It’s a growing challenge for security and IT admins to keep track of which corporate data is shared, who is sharing the data, and where they might be sending it.
The problem is evolving as businesses adopt a growing number of cloud products: On average, companies use 27 different cloud apps and services. Nearly half of IT and security pros surveyed say cloud services make it tougher to protect confidential or sensitive data; 57% don’t think their organization is careful about sharing sensitive information with third parties in the cloud.
Altitude Networks, a new startup from former Twitter CISO Michael Coates and former Capital One lead data scientist Amir Kavousian, today officially launched with $9 million in Series A funding to address this issue. The round was led by Felicis Ventures with participation from Slack Fund, Accomplice, and a personal investment from former Facebook CSO Alex Stamos.
Coates and Kavousian want to tackle the problem of data security in the cloud and in doing so, protect businesses from unauthorized data access, data theft, and accidental and malicious sharing to unintended recipients. Altitude’s platform monitors for personally identifiable information, payment data, and other files that may cause potential damage if shared: legal documents, internal financial data, product road maps shared with unauthorized accounts.
“I needed this as a CISO, I wanted to buy it, it didn’t exist,” says Coates, who also previously led security at Mozilla and served as chairman of OWASP. In his role at Twitter, Coates sought to find a platform that would protect data from unauthorized sharing. What he found were several cloud access security broker and data loss prevention tools, many of which promised to alert when files were publicly shared.
“It’s far deeper of a problem than is shared publicly,” he adds. Even when they’re not made public, sensitive files can still do damage if shared with the wrong people. Coates spoke with CISO peers and learned many want to prevent this risk but hadn’t found an answer: They have plenty of collaboration apps but no way to know how files move in and out of the company.
“Cloud collaboration makes it easy for an employee to make a mistake and share documents they shouldn’t,” he explains. Someone leaving a company may decide to send files to a personal account; if the account is compromised, the attacker now has strategic data. “All of these issues are happening regularly inside of companies due to the doubling down of collaboration.”
Altitude’s platform integrates into cloud environments to give businesses a view of where sensitive files are so they can remove access and protect them. By understanding the context and provenance of a file, it can determine a “risk rating” that dictates whether sharing is dangerous. It categorizes these risks so administrators can filter files that have been leaked outside the company, or specifically look at sensitive files that have leaked outside the company, Coates explains. They can also view files that were downloaded and shared.
Right now, the tool is designed to support software-as-a-service applications G Suite and Box, with plans to expand to Office 365, Slack, and Salesforce, among others.
“Part of the challenge in tackling the problem is the massive amount of collaboration and sharing that’s happening,” says Coates. Some file-sharing actions are egregious; for example, publicly sharing financial earnings. Others might be more of a gray area, such as sharing a strategic road map with a third party. Altitude’s platform lets security managers question a file and ask an employee whether they meant to perform an action, then lock the file if needed.
“When you have a security problem, what you need is context,” he explains, citing his experience in incident response and addressing malicious insiders. Admins don’t just need to know a file was dangerously shared but whether it was sensitive and who shared it. Coates says Altitude’s platform has detected when financial reports are shared with personal accounts.
Altitude Networks plans to use its funding to drive growth and customer acquisition strategies.
Related Content:

Black Hat USA returns to Las Vegas with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions, and service providers in the Business Hall. Click for information on the conference and to register.
Kelly Sheridan is the Staff Editor at Dark Reading, where she focuses on cybersecurity news and analysis. She is a business technology journalist who previously reported for InformationWeek, where she covered Microsoft, and Insurance Technology, where she covered financial … View Full Bio
In a large school district, there was a digital sign for a snack area that no one had thought about for months. Eventually, the snack area was removed, yet the sign was still plugged into the district’s network. For months, it turns out, the sign had been compromised by attackers and was communicating with 100 different countries.
The case highlights the problematic nature of the Internet of Things (IoT) and the ingenious ways bad actors are taking advantage of the fast-growing attack surface created by IoT. It also shows that security must adapt to this new reality if enterprise networks and sensitive data are to remain protected.
The challenge around IoT security will only grow. Worldwide spending on IoT is expected to hit $745 billion this year and blow past $1 trillion in 2022. For enterprises deploying IoT devices, security remains the top technical issue as those looking to compromise the devices are often sophisticated nation-states or organized crime organizations.
The myriad IoT devices come with an almost equal number of challenges:
There is a lack of visibility and security into the devices in what is an increasingly distributed enterprise IT environment. Often the devices are deployed on the interior of the network, and while some may be talking externally to a public cloud or other Internet-based systems, many communicate internally to other systems on the network.
Security deployed at the network’s perimeter will be blind to such communications unless the enterprise is watching the internal network, which many aren’t. If those devices are compromised, they become a launching pad into other parts of the network. The school district’s digital sign is proof-positive here.
The network is now the focal point for IoT security. The devices connect into the network, the network touches all data and workloads, and this is how hackers can move laterally to compromise whatever systems and data are on the network. Through the network, users and devices can be authenticated, policies and rules put in place to control access and behavior, and visibility can be increased to detect anomalies.
The top IoT issue is that you shouldn’t rely on physical security to keep things off a network. There are many places in the wired network that are wide open and there is little network access control. There’s more control and authentication on the wireless side, but even there, devices that are authenticated often get dropped into an internal VLAN and from there are uncontrolled.
Key steps that can be taken to better protect an enterprise network:
Central to the issue of IoT security moving forward is the growing need for security and networking folks to communicate. Getting this to happen is sometimes easier said than done. In some ways, the two groups are often adversarial. Network operators are happy if all the network packets are flowing quickly with high availability and low latency — even if all those packets are carrying malicious traffic. The security group would probably be happiest if nothing flowed through the network at all.
The network plays a critical role in two areas: detecting when an attack is taking place and responding to the attack by shutting down the device, limiting it, or slowing it down. There is much you can do with the network infrastructure. People will look to firewalls for solving network security problems, but don’t tend to use a firewall for every single switch port. The security capabilities must be built into the network itself.
That will mean cooperation between network and security groups. Because this is a cultural issue, it will need to start with high-level executives. That doesn’t necessarily mean both sides will report into the same structure. However, the security pros will have to determine what needs to be protected and the network folks will have to decide how to make it happen, all the way at the network edge where the devices connect.
Bringing these two groups together will be a challenge, but it’s necessary. Without it, there will be more data breaches coming from a wider variety of things rather than end-user systems. HVAC controllers, TV screens, smart fish tanks, and other IoT devices will continue to be used by hackers seeking ways into critical parts of the network. And the IoT devices won’t be getting better from a security perspective anytime soon because many of the makers of these things aren’t focusing on that.
Related Content:

Black Hat USA returns to Las Vegas with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions and service providers in the Business Hall. Click for information on the conference and to register.
Jon Green is responsible for providing technology guidance and leadership for all security solutions, including authentication and network access control, UEBA, encryption, firewall, and VPN. He also manages Aruba’s Product Security Incident Response Team (PSIRT) and Aruba … View Full Bio
Article source: https://www.darkreading.com/endpoint/why-the-network-is-central-to-iot-security/a/d-id/1335367?_mc=rss_x_drr_edt_aud_dr_x_x-rss-simple
Jamf, a company specializing in management systems for Apple products, has announced its acquisition of Digita Security, which offers Apple Mac endpoint protection for businesses.
Digita Security, founded by a team of security experts including Patrick Wardle, a well-known security researcher specializing in iOS and MacOS, provides a trio of products — Do Not Disturb, UXProtect, and Xplorer — that notify users when a third party tries to access their systems and extends the anti-malware software provided by Apple itself. Those capabilities will now be part of the mobile device management (MDM) suite for iOS and MacOS devices offered in several configurations by Jamf.
Financial details of the acquisition were not released.
Read more here.

Black Hat USA returns to Las Vegas with hands-on technical Trainings, cutting-edge Briefings, Arsenal open-source tool demonstrations, top-tier security solutions, and service providers in the Business Hall. Click for information on the conference and to register.
Dark Reading’s Quick Hits delivers a brief synopsis and summary of the significance of breaking news events. For more information from the original source of the news item, please follow the link provided in this article. View Full Bio
Thanks a whole bunch, Internet of Things (IoT): you’ve already brought us autonomous vehicles and other connected cars that can be turned into steel/glass/combustible whirling dervishes, as in, Jeep Cherokees that can be paralyzed by remote attackers 10 miles away and whose steering wheels could be spun 90 degrees while the car was zooming down the highway at 60 mph.
Crazy Tilt-a-Whirls that they were, those were one-off, proof-of-concept attacks on individual cars, pulled off by renowned automobile/security researchers Charlie Miller and Chris Valasek.
But what about if hackers pulled a coordinated, distributed attack? As in, a denial-of-service (DoS) attack where multiple cars were strategically zombified, such that they gummed up a crucial intersection?
Start thinking about it now, said physicists at Georgia Institute of Technology and Multiscale Systems Inc., an RD firm specializing in advanced materials and cyber-physical systems. Internet-connected cars could be used to gridlock whole cities, the researchers said after calculating just how many hacked, stalled vehicles it would take.
From a writeup of their research that was published in Science Daily on Monday:
In the year 2026, at rush hour, your self-driving car abruptly shuts down right where it blocks traffic. You climb out to see gridlock down every street in view, then a news alert on your watch tells you that hackers have paralyzed all Manhattan traffic by randomly stranding internet-connected cars.
According to the researchers’ simulations, all it would take to freeze traffic solid in a city like Manhattan is to strand 20% of all cars. Here’s David Yanni, a graduate research assistant working in the lab of Peter Yunker, co-leader of the study and assistant professor in Georgia Tech’s School of Physics:
Randomly stalling 20% of cars during rush hour would mean total traffic freeze. At 20 percent, the city has been broken up into small islands, where you may be able to inch around a few blocks, but no one would be able to move across town.
Those numbers are conservative, given that not all cars on the road need to be connected. If 40% of all cars on a city’s road were connected, attackers would just have to hack half of them to get a city gridlocked.
The researchers’ paper, titled Cyberphysical risks of hacked internet-connected vehicles, was published in Physical Review E yesterday.
They relied on coffee to get their results. Percolation, to be precise. The researchers developed what they call an “analytic percolation-based model to rapidly assess road conditions given the density of disabled vehicles and apply it to study the street network of Manhattan” to reveal how vulnerable the city would be to such a “cyberphysical” attack.
This is not surprising: Yunker’s done fascinating work with the spread of coffee particles, which are round and which create, as we all probably know, round coffee rings when you dribble them. Here’s a mesmerizing video of microscopic particles moving in a drop as they migrate to the outer edges to form a coffee ring as the drop dries… a video that also shows the clumps those particles form all over the droplet surface if you elongate the particles so that they look, well, like itty bitty cars, jamming up Manhattan.
The gridlock wouldn’t have to be complete in order to create serious, life-threatening scenarios. For example, hacking 10% of all cars at rush hour would enable traffic to keep crawling, but emergency vehicles couldn’t get through.
Yes, these are complicated calculations, but the percolation-based method is a reasonable start in analysing how such an attack would impact cities, say the researchers:
While a comprehensive investigation of city-scale traffic around hacked vehicles is an extremely complicated problem, we find that the statistical physics of percolation can provide an estimate of the number of vehicles that critically disrupts citywide traffic flow.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/21-9DXPF4gg/
It’s getting hard to keep track of how often Georgia’s been hit with ransomware in the past 14 months or so.
The most recent slap: attackers preyed on the Georgia Department of Public Safety (DPS), according to Government Technology Magazine. The DPS encompasses agencies including the Georgia State Patrol, Georgia Capitol Police and the Motor Carrier Compliance Division, which carries out safety inspections.
Chief Information Security Officer David Allen told the magazine that his staff noticed the attack early Friday morning after some network resources and communication systems went wonky.
Chief Technology Officer Steve Nichols said that the DPS was forced to bump all servers offline while the Georgia Technology Authority investigates the attack. That includes email servers and those that support the department’s public website and backend. Nichols said:
As soon as they saw what was happening [Friday morning] they took all the servers offline across their entire infrastructure.
As of Monday, Government Technology was reporting that Georgia’s DPS hadn’t found evidence of sensitive data being compromised in the attack. State troopers are having to resort to old-school law enforcement, though, said Nichols:
If a trooper is out on a highway writing a ticket, for example, they might be doing it with a pen and paper instead of a tablet. Or, if they’re looking up a license plate, they would radio it into a dispatcher instead of using a tablet.
As well, as the Atlanta Journal-Constitution reports, Georgia State Police, Georgia Capitol Police and Department of Motor Vehicle Safety have all had to switch to an older radio and phone system.
Pity anybody working in IT for Georgia these days: over the past year, it’s been a mad scramble of ransomware attacks and costly mop-ups for the state and its agencies.
The first attack hit the city of Atlanta in March 2018 and destroyed years of police dashcam video, as well as freezing systems. Six days after it was hit, Atlanta was still rescheduling court dates, police and other employees were still writing out reports by hand, and residents couldn’t go online to pay their water bills or parking tickets.
That attack involved SamSam ransomware – a high-profile ransomware that was typically used in targeted attacks where cybercriminals break into a victim’s network and launch ransomware manually, to cause maximum damage and disruption.
The crooks demanded what was then roughly $52,000 worth of bitcoin.
In November 2018, two Iranian men were indicted in the US for the Atlanta attack, which was only one out of a crime spree that hit 200 victims, including hospitals, municipalities, and public institutions.
Then, earlier this month, Georgia’s court systems got hit with ransomware that might have involved Ryuk, a relatively new strain of targeted ransomware that picked up where SamSam left off in August 2018.
Another attack came this month: a few weeks ago, on 17 July, the government of Henry County in Georgia – the second fastest growing county in metro Atlanta – announced it had been hit by malware. There was no ransom demanded at the time, so it might have not been a ransomware attack. Whatever it was, county officials wound up losing access to the internet and most online services. Four days earlier, on 13 July, the police department in Lawrenceville, Georgia was hit with ransomware. Hackers encrypted most of the department’s data, including body camera footage.
CISO Allen told Government Technology that paying ransom to crooks isn’t the DPS’s policy. Nor is it his policy to even read the ransom notes, he said:
In all honesty, I don’t even typically look at the files they leave behind on how to contact them. I don’t agree that it’s more cost effective to pay [the ransom] because even if you pay it and get some of your system decrypted, it doesn’t always happen in a clean fashion.
That, in fact, is an attitude shared by US mayors: a few weeks ago, the US Conference of Mayors resolved that ransomware attackers could all go suck on a lemon.
After a whole lot of good, solid “whereas” points, the nonbinding resolution for the country’s mayors was this:
NOW, THEREFORE, BE IT RESOLVED, that the United States Conference of Mayors stands united against paying ransoms in the event of an IT security breach.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/_Ny4QNCGDto/
Google’s Project Zero has unveiled details of a bug in Apple’s iMessage that lets attackers read data from an iPhone without any user interaction.
The bug is one of four revealed by Project Zero researcher Natalie Silvanovich that Apple patched last week. Named CVE-2019-8646, it is classified with high severity. It allows attackers to read data from an iPhone without any user interaction and could also allow writing to out-of-bounds memory. Silvanovich provided proof-of-concept code that leaks bytes of memory from the targeted phone and displays it on an attacker’s remote machine.
CVE-2019-8647, also a high severity bug, crashes the iPhone’s Springboard home screen manager with no user interaction. That bug, along with the high severity CVE-2019-8660, could allow arbitrary code execution. CVE-2019-8660 would be difficult to exploit in practice, though, she added.
CVE-2019-8624, also ranked moderate, allows an attacker to crash Springboard without any interaction.
There’s one bug that Silvanovich is holding back on because she doesn’t believe that Apple has patched it properly. That’s CVE-2019-8641, which affects the iPhone 5s and later, along with all iPads since the Air and all iPods since generation six. It involves an out-of-bounds read, which allows remote attackers to cause unexpected application termination or arbitrary code execution.
In the patches that it released last week, Apple said it had fixed this issue by improving its input validation. The patch didn’t work, according to Silvanovich:
@5aelo We are withholding CVE-2019-8641 until its deadline because the fix in the advisory did not resolve the vulnerability
—
Natalie Silvanovich (@natashenka) July 29, 2019
Even though that patch apparently didn’t stick, it’s still worthwhile checking to ensure that you’ve installed all the other iMessage patches (along with all the other patches that Apple dropped last week). To do that, tap the Settings icon, then select Software Update. If there’s a patch waiting to be installed, it will let you initiate it. To be safe, if you’re downloading the patch over a Wi-Fi network to save on your data plan, always use a trusted network rather than a public one.
Silvanovich discovered another bug earlier this year. Classed as moderate, CVE-2019-8573 and CVE-2019-8664 bricks the iPhone with a malformed message. It stops the phone displaying the UI and responding to input, and it survives a hard reset, rendering the phone unusable until the user reboots into recovery mode and does a restore, which deletes all their data. She disclosed that one in early July 2019 after Apple patched it in iOS 12.3.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/lRgoEr1lXx4/
Updated The Document Foundation said on Tuesday that it had recently patched* LibreOffice, its open-source office suite, to fix an issue where documents can be configured to run macros silently on opening.
The code execution vulnerability, reported by Nils Emmerich and assigned CVE-2019-9848, is the result of multiple flaws.
The first is with a feature called LibreLogo which is intended for teaching programming. You type Logo commands into a document and it draws graphics from those instructions with a cursor that looks like a turtle, as a homage to the Logo programming language of yore.
The LibreOffice implementation converts the Logo commands to Python, which is passed to the Python interpreter for execution without much in the way of safety checks. LibreLogo is an optional component, though installed by default.
The second problem is that built-in macros in LibreOffice are fully trusted — including the macro that runs LibreLogo. Even if you set macro security in LibreOffice to “Very high,” the LibreLogo macro still runs without prompting. The third, and final, problem is that LibreLogo passes arbitrary Python code in the document to the Python interpreter to execute.
The result is that it is trivial to create a document that includes a malicious Python script in its text, which is executed automatically. We created a document that will pop open the Windows Calculator, as per Emmerich’s example, assigned LibreLogo Run to the Open Document event, and attached it to an email to send to a mark. Microsoft’s Outlook helpfully made the document read-only for safety when it was received, but it still obediently ran Calc when the attachment was opened.
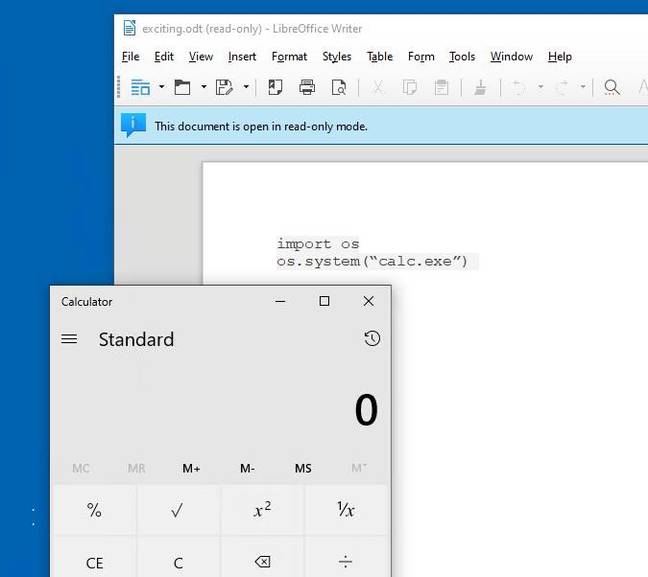
LibreOffice running Calc on Windows 10, without any prompt.
The LibreOffice team tried to fix* fixed the problem by blocking the ability to attach the LibreLogo Run macro to a document event handler. The attempted fix was in version 6.2.5 (released on 20 June 2019).

That said, if you go to the LibreOffice download page version 6.2.5 is recommended only “if you’re a technology enthusiast, early adopter or power user.” Version 6.1.6 is recommended as it is “tested for longer” and the implication is that that is the pick for more cautious users or businesses. Unfortunately it is also still vulnerable, as demonstrated in our quick test.
It was Microsoft Word that made macro viruses famous, one of the best known being Melissa in 1999. Much pain ensued, but Microsoft made many efforts to contain the problem, and in Office 2007 introduced the .docm format for Word documents that contain macros, as well as similar formats for other Office applications. There is no such distinction in ODF (Open Document Format) as used by OpenOffice and LibreOffice. Perhaps there should be.
Users of LibreOffice who set it as the default application for .ODT documents should either upgrade to version 6.2.5 or higher, or remove the LibreLogo component from their installation.®
*It appears that the supposedly fixed 6.2.5 is still vulnerable – confirmed by us. There is an updated bug report here. The fix therefore (on Windows) is to go to Control Panel – Programs and Features, hit Change on the LibreOffice entry, and untick the LibreLogo component.
Sponsored:
Balancing consumerization and corporate control
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2019/07/30/libreoffice_macro_virus/
Lancaster University has started withdrawing non-business-critical access to a breached student database – more than a week after the apparent hack took place.
Following the breach, which affected somewhere between 12,000 and 20,000 people, the northwest England uni has begun pulling staff access to its LUSI (Lancaster University Student Information) records system, which was developed in-house and first went live around five years ago.
In an email sent yesterday and seen by The Register, Heather Knight, director of students, education and academic services, wrote to staff saying: “In response to the recent cyber incident, we are taking steps to enhance the security of all University systems. We are therefore in the process of limiting users’ access to data and functionality in LUSI.”

LUSI is the student and applicant records database that was targeted. A 25-year-old man from Bradford was arrested last week on suspicion of Computer Misuse Act crimes and released on police bail.
“In the first instance,” continued Knight’s email, “we are removing all users’ access to LUSI online, except for those staff as identified as needing access for critical business reasons.”
Around a thousand accounts had access to LUSI, a number which sources tell us has been slashed to around 100.
The university website explains that LUSI services include the Course Approvals and Information Tool (CAIT), which is the key system from which at least 12,500 applicants’ personal data were siphoned just under a fortnight ago.
External web access to the LUSI portal appeared to have been disabled when The Register clicked to access it from the above linked webpage. On the weekend immediately following the hack, which is said to have taken place before Friday 19 July, sources told us the staff VPN was also shut down.
A university helpdesk page explaining LUSI states: “LUSI is developed and managed by CIS Academic and the Student Registry in Lancaster and holds data on every student that has ever studied at Lancaster University.”
While this seems alarming on the face of it, a reasonable explanation would be that the university needs to keep a record of who it issued degrees to and when. In its initial statements about the breach, Lancaster said that only applicant data for the academic years 2019 and 2020 was stolen, along with some current students’ data.
In a statement, Lancaster told The Register: “As soon as the university became aware of the breach it took steps, on a risk-based approach, to secure all university systems.”
Despite the arrest of an apparent suspect, it seems strange for the university to take more than a week to revoke unnecessary access to what appears to be the hacked system.
Duncan Brown, chief EMEA security strategist at infosec biz Forcepoint, told The Register: “Phishing, no matter how sophisticated it is, comes down to people being tricked. If you’re not able to understand the normal interactions of people and data, then when a breach occurs with its corresponding anomalous behaviour, it’s very hard to spot and react to it.
“All companies must do better in quickly identifying issues and putting together a plan to address them. Faster incident response and breach handling is a necessity to appease regulatory bodies and maintain competitive advantage, regardless of your industry sector.”
Brown added: “I think 10 days to react isn’t unreasonable, as they don’t want to suspend accounts unnecessarily. But prevention is always going to be preferred to cure.” ®
Sponsored:
Balancing consumerization and corporate control
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2019/07/31/lancaster_uni/