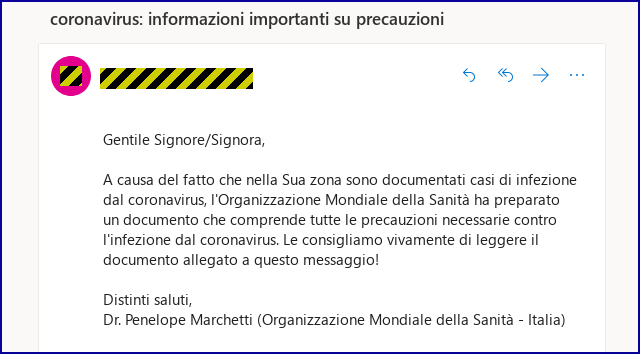
6 Steps CISOs Should Take to Secure Their OT Systems
The inevitable digitalization of an industry can create strife within companies, especially between colleagues tasked with blending often old and idiosyncratic business-critical operational technology (OT) with information technology (IT).
One crucial source of confusion: Who is responsible for the all-important cybersecurity risk mitigation of OT systems as they become part of the Industrial Internet of Things? There’s no universal answer yet. Some chief information security officers (CISOs) are drawn from OT, and some from IT.
Either way, the first question each new CISO must answer is, “What should I do on Monday morning?” My suggestion: Go back to basics.
What I’ve noticed working with industrial companies around the world is confusion among CISOs distracted by thousands of companies — new and old — offering shiny new tools to prevent and detect threats in exciting ways. As a result, there’s a good chance new CISOs could overlook the basic, fundamental steps needed to build the broadest, strongest risk mitigation.
Here are the six steps all new CISOs should take to begin protecting their OT environments in the most effective way possible:
• Step 1: Asset inventory. A company’s OT systems are its crown jewels, and the CISO’s primary role is to protect them. First step: Explore, discover, and inventory every OT element in the organization to learn exactly what you’re protecting — data, software, systems, etc. Without a complete and accurate asset inventory, the succeeding steps will fall short in minimizing cybersecurity risk.
• Step 2: Backup/test restore. The most effective way to protect OT systems from expensive to ruinous ransomware attacks, to cite just one risk, is to back up OT data and perform a test restore to make certain the backups are optimal. Backing up systems is crucial for multiple reasons, security among them.
(Tip: In case of ransomware attacks, don’t forget the European police agency Europol’s public/private No More Ransom site, which offers proven, valuable anti-ransomware tools free of charge.)
Yes, test restore can be challenging, but OT network backups are only as good as the test restore process that assures their effectiveness by protecting the network from data loss.
As we’ll see in step 5, it’s important to identify pertinent data for test restore on a continuous basis — often by asking users in the organization which data is most important for their work — but for the first backup/test restore, do it as widely and deeply as possible now to avoid data loss and other problems down the road.
• Step 3: Software vulnerability analysis. Step 1’s asset inventory will reveal all the software in the organization’s OT systems. The CISO must know the state of every software asset. Every piece of software must be subjected to vulnerability analysis. What version of the software do you have? Is it up to date? Are there more recent versions — safer and more effective — the OT system will accept and continue to thrive with?
A crucial question about the software: Does it need patching? If so, here’s a critical warning: Don’t do the automatic IT thing of reflexively patching everything, because OT patching is a complex and challenging process that rates an entire step onto itself.
• Step 4: Patching. Though automatic in IT, patching in OT is the proverbial briar patch. Sometimes patching OT software can make things worse. The soft underbelly of digitalizing the industrial economy is old OT machines and systems. Some absolutely vital systems have been on factory floors for 15 to 25 years or more, and they can’t be taken down and patched. And even if appropriate (and safe) patches are available, old OT may not have enough memory or CPU bandwidth to accept them.
Finally, many OT systems are highly orchestrated combinations of software and hardware that develop “personalities,” and when they’re patched, they come back up with unpredictable results.
What to do? I suggest a threat analysis approach that can identify vulnerabilities and minimize risk short of patching.
• Step 5: Backup/test restore — again. Backup/test restore must become an ingrained habit whenever anything in the OT or IT system changes — updates, for example. The test restore process should include a plan that identifies testing frequency and the specific mode of testing. It is also important to make certain the operating system directly correlates with the version of software being used, as well as the structure of the database.
Important advice: Repeat steps 3 to 5 regularly, forever. New vulnerabilities are often found in old software.
• Step 6: Enable centralized logging. CISOs must know not just how something is working or failing, but why it’s failing — and for that, centralized logging is a must. Centralized logging consolidates, manages, and analyzes logs to empower CISO teams to understand their environments, identify threats as early as possible, and optimize defenses.
In my experience, many OT systems have never been monitored. Given how much goes on in OT systems, consistent centralized logging is a must-have: It enables CISOs to confidently identify alarming security signals amid the potentially deafening routine noise.
If new CISOs take these six basic but essential steps — and habitually repeat those that need repeating — they can go home Monday night confident they’ve done a solid job minimizing risk for their organization’s OT.
Related Content:
- 3 Ways to Strengthen Your Cyber Defenses
- DHS’s CISA Warns of New Critical Infrastructure Ransomware Attack
- IoT Malware Campaign Infects Global Manufacturing Sites
- Online Malware and Threats: A Profile of Today’s Security Posture
Satish joined San Jose-based ABB in February 2017 as chief security officer and Group VP, architecture and analytics, ABB Ability™, responsible for the security of all products, services and cybersecurity services. Satish brings to this position a background in computer … View Full Bio
Article source: https://www.darkreading.com/risk/6-steps-cisos-should-take-to-secure-their-ot-systems--/a/d-id/1337236?_mc=rss_x_drr_edt_aud_dr_x_x-rss-simple