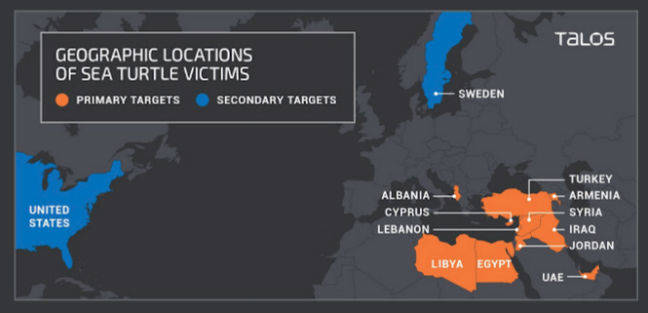
‘Sea Turtle’ group has compromised at least 40 national security organizations in 13 countries so far, Cisco Talos says.
A sophisticated state-sponsored hacking group is intercepting and redirecting Web and email traffic of targeted organizations in over a dozen countries in a brazen DNS hijacking campaign that has heightened fears over vulnerabilities in the Internet’s core infrastructure.
Since 2017, the threat group has compromised at least 40 organizations in 13 countries concentrated in the Middle East and North Africa, researchers from Cisco Talos said Wednesday.
In each case, the attackers gained access to, and changed DNS (Domain Name System) records of, the victim organizations so their Internet traffic was routed through attacker-controlled servers. From there, it was inspected and manipulated before being sent to the legitimate destination.
Most of the victims of the “Sea Turtle” campaign – as Cisco Talos is calling it – are national security-related and include ministries of foreign affairs, intelligence agencies, and military organizations.
The Sea Turtle group has also successfully targeted numerous third-party entities such as DNS registrars, Internet service providers, and telecommunication companies that provide access to its primary targets. Among this secondary set of victims is, for the very first time, a DNS registry service—an entity that manages Top Level Domains (TLD) such as .com domains.
The primary motive for the Sea Turtle campaign appears to be cyber espionage. “We assess with high confidence that this activity is being carried out by an advanced, state-sponsored actor that seeks to obtain persistent access to sensitive networks and systems,” the security vendor said in a report.
Craig Williams, director of outreach at Talos, says the manner in which the attackers have been updating the DNS records make it appear as if the owner is simply pointing their domain at another server. This would typically appear to be normal activity.
“The takeaway for the enterprise is to ensure you have your domains locked down with a registry lock and have multifactor authentication on wherever possible,” Williams says.
“This is also a great reminder that everyone needs to turn on automatic updates where possible, and if that isn’t possible, ensure there are extra defensive layers in place,” he says.
Mounting Worries
Concerns over DNS-level attacks have been growing in recent months.
In January, the US Department of Homeland Security issued an emergency directive directing administrators of all .gov and other agency-managed domains to audit their public DNS records to ensure the records had not been manipulated. The directive also required .gov domains to change DNS account passwords and implement multi-factor authentication. The directive was prompted by what the DHS described as a series of incidents of DNS infrastructure-tampering involving multiple executive branch agencies.
In a separate advisory also in January, the DHS warned of attackers changing DNS records at many organizations by using credentials stolen from enterprise administrators with legitimate access to those records. In these incidents, the attackers were altering DNS records like Name Server (NS) records, DNS A (Address) records, and MX or Mail Exchanger records.
That particular DHS advisory stemmed from warnings by several vendors including Cisco Talos and FireEye of DNS redirection attacks. The Talos warning had to do with a campaign targeting organizations in the Middle East, where attackers were using a malware dubbed DNSpionage to redirect a targeted website’s traffic.
FireEye’s warning pertained to a likely Iran-based threat actor carrying out a massive DNS traffic redirection campaign once again focused on Middle East targets.
According to Talos researchers, the Sea Turtle campaign is different from and more severe than DNSpionage and other previous DNS hijacking campaigns.
Typical attacks have begun with Sea Turtle actors gaining initial access to a targeted entity either by exploiting known remote-code execution vulnerabilities, or via spear-phishing emails. Once on a network, the group’s tactic is to expand its access until it can grab credentials for accessing the breached organization’s DNS records at the registrar managing them.
Sea Turtle actors then use the stolen credentials to modify the DNS name server record and point users to a man-in-the-middle server under the attacker’s control for capturing credentials and other information. The MitM server is usually set up to spoof a legitimate service – like a VPN, for instance.
To make the malicious server appear legitimate, Sea Turtle actors have been using a technique called certificate impersonation, where the attackers obtain a valid, signed digital certificate from another certificate provider for the same domain. “For example, if a DigiCert certificate protected a website, the threat actors would obtain a certificate for the same domain but from another provider,” Talos said.
The attackers have also been stealing the breached organization’s SSL certificate and using it on their own servers to carry out MitM attacks. In one instance, Cisco Talos discovered one of the company’s own VPN applications being used in MitM attacks.
Dangerous Turn
In addition to accessing enterprise DNS records using stolen credentials, Sea Turtle actors have also been directly targeting DNS registrars and registries as well. One example is NetNod, a Swedish DNS service provider. In another incident, Sea Turtle actors gained access to registrars that manage top-level domains for Armenia.
Such attacks are of considerably more concern than DNS modification attacks involving a single organization’s credentials. “Access to a registrar can have catastrophic consequences since the attacker may be able to modify where domains point,” Williams says.
DNS hijacking attacks are certainly not new. Threat actors have been previously known to modify DNS records and redirect traffic for a variety of reasons. The concern is whether such attacks are going to increase, and the damage that could result from a compromise of a major DNS registry or registrar.
“My experience indicates that compromising network admin credentials by some means such as phishing and using those to log in to the DNS provider or registrar” remains the most common and straightforward method for attackers, says Emily Hacker, security researcher at DomainTools. The approach only allows the attacker to manipulate the records for the company whose network admin credentials were phished, she says.
“Alternatively—and less commonly—an attacker could get the admin credentials for a registrar, registry, or hosting provider, which would then allow them to manipulate records for any and all DNS records managed by that particular service” Hacker says.
Related Content:

Join Dark Reading LIVE for two cybersecurity summits at Interop 2019. Learn from the industry’s most knowledgeable IT security experts. Check out the Interop agenda here.
Jai Vijayan is a seasoned technology reporter with over 20 years of experience in IT trade journalism. He was most recently a Senior Editor at Computerworld, where he covered information security and data privacy issues for the publication. Over the course of his 20-year … View Full Bio
Article source: https://www.darkreading.com/attacks-breaches/nation-state-hacker-group-hijacking-dns-to-redirect-email-web-traffic/d/d-id/1334462?_mc=rss_x_drr_edt_aud_dr_x_x-rss-simple