Trello exposed! Search turns up huge trove of private data
Hands up who’s used the increasingly popular online collaboration platform Trello?
Trello is great for organising to-do lists and for coordinating team tasks.
But it has its downsides too. While the default for Trello boards is set to ‘private’, many users set them to ‘public’ which means that anyone can see what’s posted there.
Not only that, search engines such as Google index public Trello boards, making it simple for anyone to uncover the boards’ contents using a specialised type of search called a ‘dork’.
And it’s surprising how much sensitive data there is.
Our global cybersecurity operations director at Sophos, Craig Jones, has been keeping an eye on this for a couple of years, first tweeting about it in 2018.
One of the worst Trello boards I came across, a HR onboarding Trello board, it’s been reported and removed now. It… twitter.com/i/web/status/9…
—
Craig Jones (@albanwr) April 17, 2018
When news broke last week about office space company Regus exposing the performance ratings of hundreds of its staff via a public Trello board, Craig thought he’d take another look at what’s out there.
An enthusiastic Trello user himself, Craig quickly found a trove of highly sensitive data sprayed out by sizeable numbers of public Trello boards.
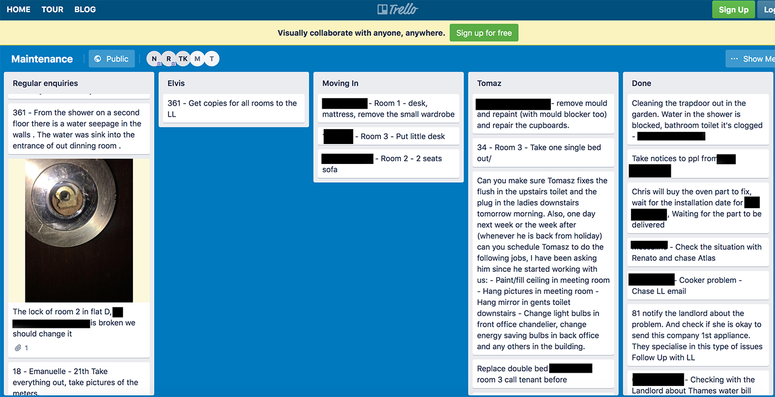
He found a board from a housing company detailing the fixes needed in each accommodation, including broken door locks:
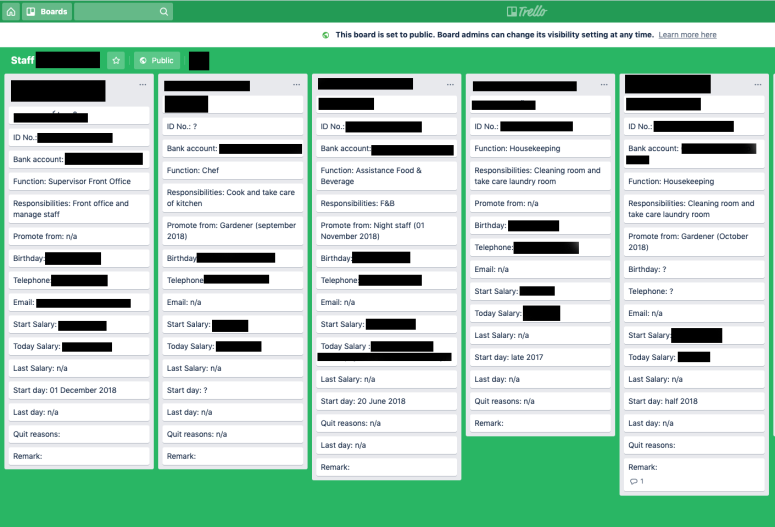
Craig also discovered a staff board for what appears to be some sort of facilities company that listed names, emails, dates of birth, ID numbers, bank account information, and more:
And then there’s an HR board that details a specific job offer to someone, including their salary, bonus and contractual obligations:
There’s more.
He found a board relating to an Australian pub which included details of customer fraud, bucketloads of gmail and social media passwords, and API keys, passwords and credentials belonging to a global IT household name.
Craig has contacted the companies where he can, to inform them their data is publicly accessible. Many have taken down the boards already.
Why do people set sensitive boards to public?
One would assume, in most cases, this is not deliberate. The design of Trello has changed over the years so it might be related in part to a past issue. It’s also possible that some are made public by one individual for a legitimate reason, the security implications of which are lost on other users of the same board.
Some boards are set up, made public, and eventually forgotten (although not by Google). It’s the latest version of the whole shadow IT problem where people use tools they don’t fully understand how to use securely.
Whose fault is it?
Sure, users need to bear some responsibility over keeping their data private. But Craig also believes search engines aren’t helping here.
For me, any benefit in indexing Trello boards is far outweighed by the risk of making it possible to access inadvertently exposed data. While we should all take responsibility for keeping our Trello boards private, I’d love to see Google and others stop the indexing of them in the first place.
What to do
If you are a Trello user, go and check the status of your boards and set anything with sensitive data in it to “private”.
If you know of any exposed data – perhaps data relating to you or a company you’ve worked at – there are two routes to getting it taken down.
One is to contact the admin who set up the board. In many cases, that won’t be possible, so a second option is to contact Trello, asking for the board to be made private.
But even after doing that, content remains cached on search engines for a period of time which is why it’s also necessary to ask Google to remove the content from search, or send a cache flushing request (which will cause Google to re-index it, hopefully receiving a 404 from Trello).
Latest Naked Security podcast
LISTEN NOW
Click-and-drag on the soundwaves below to skip to any point in the podcast.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/xSnZVFqX8_4/
 Check out
Check out  Check out
Check out 
