I’m the queen of Gibraltar and will never get a traffic ticket… just two of the things anyone could have written into country’s laws thanks to unsanitised SQL input vuln
Exclusive A SQL injection vulnerability on the Government of Gibraltar’s website paved the way for any old Joe to rewrite official web versions of the British Overseas Territory’s laws.
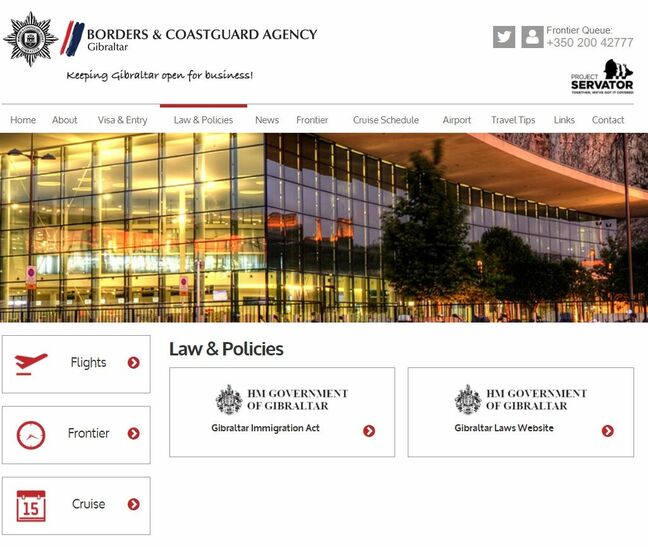
Security researcher Ax Sharma spotted the vuln while poring over the Gibraltar government’s visa rules, which he accessed from the Gibraltar Borders and Coastguard Agency website.
A malicious person using the information exposed by the government website could have deleted and uploaded PDF files to the official online repository of Gibraltar’s laws.
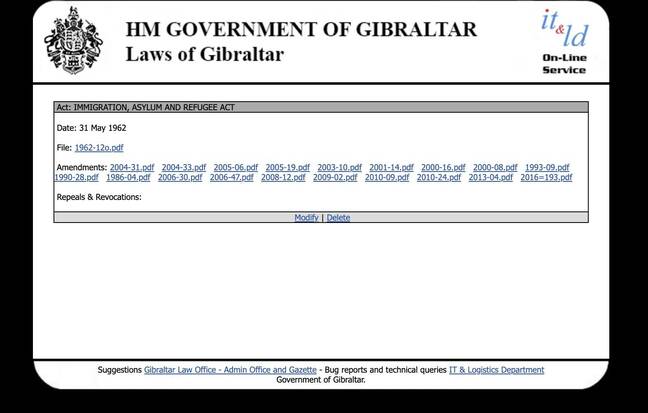
See the “modify” and “delete” links at the bottom of the page? All you needed to make those work were the site login details – and protections around those were trivial to bypass
Such people, using a freely downloadable software suite, could have abused the vulnerability to alter online versions of laws. In the digital era, laws published on government websites are treated by the wider world as official and binding even though their master versions tend to be hard copies stored in parliaments.
Although the Gibraltar Government has pulled the affected webpages offline, the incident will be a timely reminder to sysadmins that basic SQL hygiene and security practices remains as important as ever.
Gibraltar’s border agency website
Until last Friday, the link on the left (in the above picture) to the Immigration Act led to another page with a search form. That form did not sanitise user inputs to prevent the execution of code – and a single ' character input as a search term (an error-based injection) returned an error page confirming that fact, as well as links titled “modify/delete” presented on public-facing webpages for each individual law.
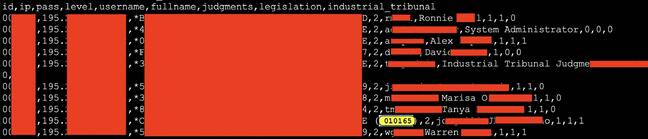
Using open-source penetrating testing tool sqlmap, Sharma was able to view all the tables and database information powering the law-hosting site. One such table, named giblaws_giblaws.user immediately caught his eye.
He told El Reg: “The table contained names of staff members, usernames and password digests, etc,” adding: “sqlmap’s in-built digest-cracking tool easily cracked one of the passwords in 1 second!”
A screenshot of the Gibraltar Government’s laws website user database, captured by Ax Sharma
That password, said the security researcher, was six numeric digits: “perhaps a date of birth”. Using those details, it would have been a trivial exercise to log in and use the account’s privileges to edit the website’s contents.
Although one would hope the Gibraltar Government maintains access and change controls as well as site content monitoring that would have allowed it to instantly spot such tomfoolery, El Reg can only speculate.
A Gibraltar government spokesman thanked Sharma for “pointing out the vulnerabilities” and said: “This matter has now been dealt with and the major vulnerabilities have been mitigated. However, within the next couple of days, this section of the website will, in any event, be relocated to an entirely new website.”
Old URLs previously leading to pages of laws currently go to 404 “not found” pages. The spokesman continued: “It should also be noted that the Government of Gibraltar website is hosted outside our corporate network and therefore the earlier vulnerabilities posed no risk to the security of the government’s communication systems.”
It is worth noting that running sqlmap on someone else’s machine without their permission could constitute an offence under the UK’s Computer Misuse Act 1990.
Strangely, the spokesman did not comment on the possibility of anyone being able to edit laws at their leisure. Political custom is that such things normally involve politicians, brown envelopes and considerable amounts of time and effort.
Sharma’s detailed findings are set out on his Medium blog. ®
Article source: https://go.theregister.co.uk/feed/www.theregister.co.uk/2020/01/07/gibraltar_sql_vuln_allowed_law_editing/
 Check out
Check out  Check out
Check out  Check out
Check out 

 Check out
Check out