When cybercrooks first got into phishing in a big way, they went straight to where they figured the money was: your bank account.
A few years ago, we used to see a daily slew of bogus emails warning us of banking problems at financial institutions we’d never even heard of, let alone done business with, so the bulk of phishing attacks stood out from a mile away.
Back then, phishing was a real nuisance, but even a little bit of caution went an enormously long way.
That’s the era that gave rise to the advice to look for bad spelling, poor grammar, incorrect wording and weird-looking web sites.
Make no mistake, that advice is still valid. The crooks still frequently make mistakes that give them away, so make sure you take advantage of their blunders to catch them out. It’s bad enough to get phished at all, but to realise afterwards that you failed to notice that you’d “logged into” into the Firrst Bank of Texass or the Royall Candanian Biulding Sociteye by mistake – well, that would just add insult to injury.
These days, you’re almost certainly still seeing phishing attacks that are after your banking passwords, but we’re ready to wager that you get just as many, and probably more, phoney emails that are after passwords for other types of account.
Email accounts are super-useful to crooks these days, for the rather obvious reason that your email address is the place that many of your other online services use for their “account recovery” functions.
A crook who can get at your emails before you do can use the [Reset password] button on your online accounts and click on the “choose new password” links that come back via email…
…without you ever noticing that a password reset was requested.
Social media passwords are also valuable to crooks, because the innards of your social media accounts typically give away much more about you than the crooks could find out with regular searches.
Worse still, a crook who’s inside your social media account can use it to trick your friends and family, too, so you’re not just putting yourelf at risk by losing control of the account.
Indeed, we now see more phishing attacks that are going after email and social media passwords than we do attacks against online banking accounts.
Here’s a not-so-good one from this week that was after webmail passwords:
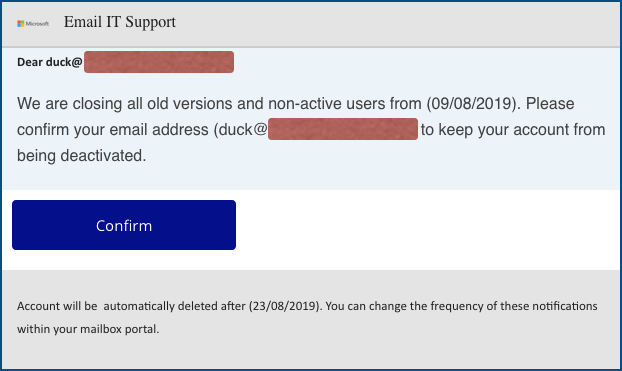
This message did indeed mention an account that’s not used much any more, so the crooks got lucky with the timing of the message.
But the ripped-off Microsoft logo is messed up and the text “we are closing all old verions” doesn’t really make sense, so your bogosity detectors should be going off by now.
The [Confirm] button is a bit sneaky – the crooks obviously wanted to avoid saying anything about “logging on” in their email, because many recipients these days know that’s a red flag.
Emails with login links are almost always bogus, especially for mainstream webmail accounts, and years of publicity about the risks of clicking through when emails demand you to “login now” have made us nervous of the L-word.
(It’s easy enough to memorise your webmail site name – for Microsoft mail, outlook.com will do the trick; for Google you just put in gmail.com; and so on.)
Of course, the [Confirm] button doesn’t do quite what it says, because you do end up at a login page anyway, and that’s where this phish shows its carelessness:
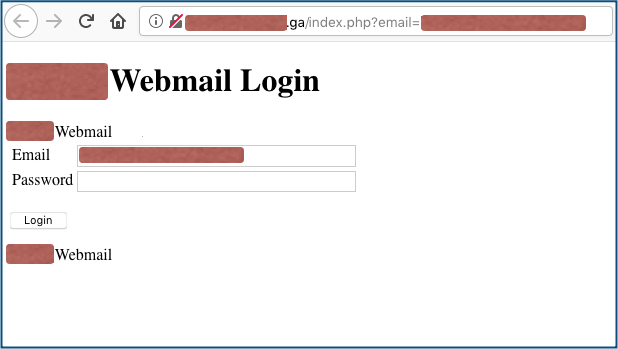
There’s no HTTPS (note the missing padlock); the domain name looks (and is) bogus; the login page doesn’t look like any webmail service I’ve ever used; and the whole thing is clearly fake.
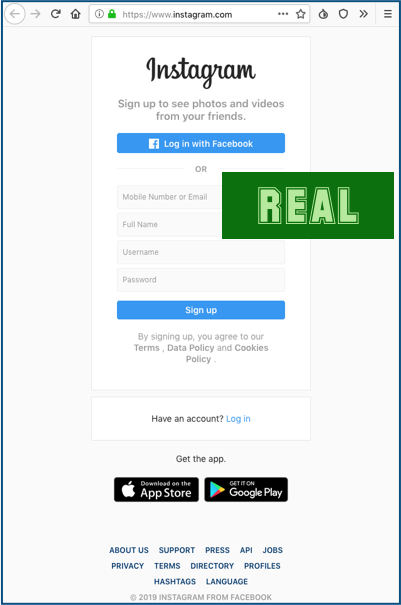
But here’s another attack we received this week that was much more believable, this time going for Instagram accounts:
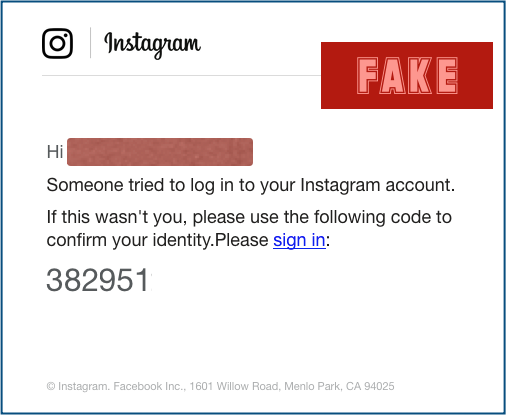
We dont like to admit it, but the crooks thought this one through.
Apart from a few punctuation errors and the missing space before the word ‘Please’, this message is clean, clear and low-key enough not to raise instant alarm bells.
The use of what looks like a 2FA code is a neat touch: the implication is that you aren’t going to need to use a password, but instead simply to confirm that the email reached you.
And two-factor authentication codes kind of ooze cybersecurity – because, well, because 2FA.
If you click through, you ought to spot the phishiness from the domain name alone – we’ve redacted the exact text here, but it’s a .CF (Centrafrique) domain that nearly spells “login”, but doesn’t quite:
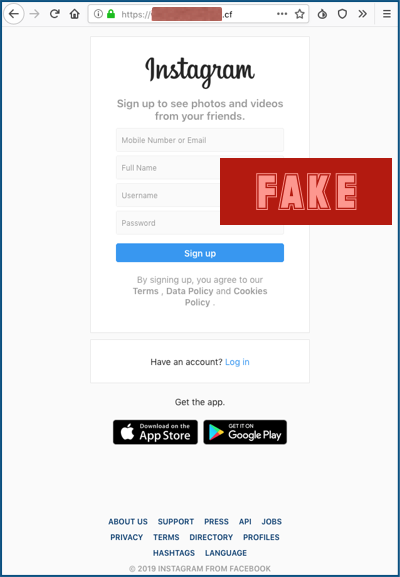
If we had to guess, we’d suggest that the crooks did’t get quite as believable a name as they wanted because they went for a free domain name. (CF is one of many developing economies that gives away some domains for nothing in the hope of attracting users and selling well-known words and what it thinks are cool-sounding domain names for $500 or more.)
Nevertheless, the phishing page itself is a perfectly believable facsimile of the real thing, and comes complete with a valid HTTPS certificate.
Remember that web certificates keep your connection to the site secure and stop the replies being snooped on or tampered with, and they vouch for the fact that the person who acquired the certificate really was able to login to the website and modify it.
But they don’t vouch for the actual content of the web pages, or for the files that are stored on the site and served up by it.
In other words, a site without a padlock definitely isn’t to be trusted, in the same way that typos and grammatical errors should turn you away; but a site can’t automatically be trusted just because it has a padlock and was advertised with emails that were spelled correctly.
The real Instagram login page is pretty close, so you can’t rely on visual mistakes in the password screen itself:
What to do?
The phishing page looks OK, and it has an HTTPS padlock just as you’d expect, so how are you supposed to spot phishes of this sort?
The good news is that, despite our grudging admission above that the crooks had come up with a phish that’s well above average in believablility, there are nevertheless some telltale signs that give it away.
Watch out for any and all of these tricks whenever you receive an email that claims to be a security warning.
- Sign-in link in email. Easy solution: never use them! If you need to sign in to Instagram, you don’t need a link to find it. Use the app on your phone or a bookmark you set up yourself from your browser. Yes, it’s slightly more work. No, it’s not difficult.
- Unexpected domain name. Make sure you know where your browser has taken you. If the address bar is too short to see the full URL, copy and paste the text out of it to make sure. If it looks wrong, assume it is wrong and ignore it, or take a second opinion from someone you trust. Yes, it’s slightly more work. No, it’s not difficult.
- Unreasonable request. If you are worried that someone else has been logging into your account, use that account’s official way of checking your login activity. Don’t rely on web links that could have come from anywhere. Annoyingly, each social media app does this a bit differently, but once you know where to look you’ll never be tricked by an email like this again. Yes, it’s slightly more work. No, it’s not difficult.
To view your login activity on Instagram. Go to your Profile page, tap the hamburger menu (three-line icon) in the top right, then the Settings option at the bottom of the screen. From there, go to Security and then Login activity
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/JksWcX1iM6g/