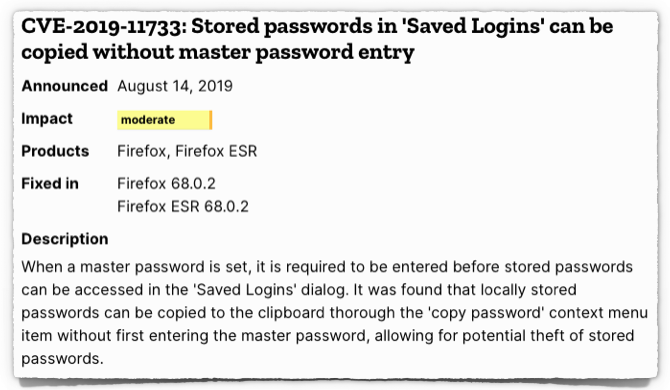
Behind the Scenes at ICS Village
Independent researchers and critical infrastructure owners came together in a small village at the Ballys Convention Center last week to share their knowledge and test their skills. In a conversation with Bryson Bort, founder and CEO of Scythe and co-founder of the ICS Village, Dark Reading heard how the federal government hopes to leverage the combination of skills that were on display at DEF CON and why rapid changes in infrastructure control are having a big impact on industrial control system (ICS) security.
“Thirty years ago, power only went one way,” Bort said. “Now, with renewables, we have a two-way street of power.” Controlling this two-way flow requires that computers manage the edge of the electrical grid, he pointed out, adding that electric automobiles make the control more complicated and more dangerous.
“Electric car infrastructure is driving a completely different problem where we’re now talking voltages that you don’t see in residential,” he said. “These are really high voltages. I think Porsche’s Taycan is coming out next year, and they’re going for, like, 800 volts.”
Bort said changes in requirements were part of why he ended up at the Department of Homeland Security talking about bringing the knowledge and skills held by DEF CON attendees to government agencies and critical infrastructure owners. “We’re trying to bring those parties together to to change the old perspective of, ‘Hey, it’s just a bunch of dirty hackers who are trying to break things for bad reasons,'” Bort said.
As a result of those conversations, the ICS Village is in the early stages of planning dedicated events at conferences next year to join independent researchers, critical infrastructure owners, and government specialists. The idea is that the assembled teams will do real research under guidelines for ethical disclosures to the benefit of the industry, Bort says.
Asked whether protecting critical infrastructure and manufacturing capabilities from enemy nation-states is the goal of the ICS Village, Bort demurred. “What we’ve seen so far is that there are no real direct attacks on our infrastructure,” he said. “Wildlife causes far more outages and disruptions than any intentional human being has done so far.”
Still, Bort said, many “operations” are going on in and around critical infrastructure every day. He described these as intelligence operations in which malicious actors get into a system, see how far they can go, and understand precisely what the defensive response is.
“I believe they are trying to establish those levers so that whenever things do rise to some tension level where we’re really talking ‘kinetic on kinetic,’ one of the other things they have in their quiver now is to pull some levers and cause some damage [to the US],” he said.
But the greatest deterrent to a proactive attack against US infrastructure can’t be found in any DEF CON village, Bort said. Should someone launch an attack, the former Army officer said, “The response that we’re going to have is not going to be wagging a finger or debating red lines. We’re going to go back and bomb you.”
Related Content:
- The Flaw in Vulnerability Management: It’s Time to Get Real
- Why Every Organization Needs an Incident Response Plan
- Why the Network Is Central to IoT Security
- What Every Security Team Should Know About Internet Threats
Curtis Franklin Jr. is Senior Editor at Dark Reading. In this role he focuses on product and technology coverage for the publication. In addition he works on audio and video programming for Dark Reading and contributes to activities at Interop ITX, Black Hat, INsecurity, and … View Full Bio
Article source: https://www.darkreading.com/iot/behind-the-scenes-at-ics-village/d/d-id/1335540?_mc=rss_x_drr_edt_aud_dr_x_x-rss-simple