The featured image above comes from @Doctor_Tran’s Twitter feed.
Here is a fascinating story – a morality tale, even.
What follows is quite long, we admit, but we think you’ll find it interesting, informative and intriguing in equal measure.
We’re dealing with a cybercriminal who forged his relationship with the underworld right back in childhood; a technically brilliant manouevre that happened by luck rather than by design; a sudden raft of unwanted attention; the lure of the celebrity spotlight; a VIP trip to Sin City; a dramatic arrest on the cusp of escape; a tidal wave of poor judgment from an unexpected source; two years on bail in the City of Angels; some strange but ultimately accurate premonitions by the antihero in our story…
…and an outcome that few people ever expected, even though many hoped against hope that it might happen.
Like any really good story, it’s more exciting if you start in the middle, so that’s exactly where we’ll jump into it.
The WannaCry era
Think back two years, to May 2017.
That was when the WannaCry malware appeared – and with something like 400,000 distinct new samples a day turning up at SophosLabs, it takes something really unusual or calamitous to make any one of them into a headline hogging story in its own right.
Well, WannaCry was both of those things.
WannaCry was unusual because it was a true virus, or more precisely, a computer worm, capable of spreading from network to network of its own accord, without anyone needing to click, download, import or approve anything.
And it was calamitous because it was ransomware – that fist-in-the-face flavour of malware that scrambles all your precious data files with a randomly chosen encryption key and then almost casually offers to sell the key back to you.
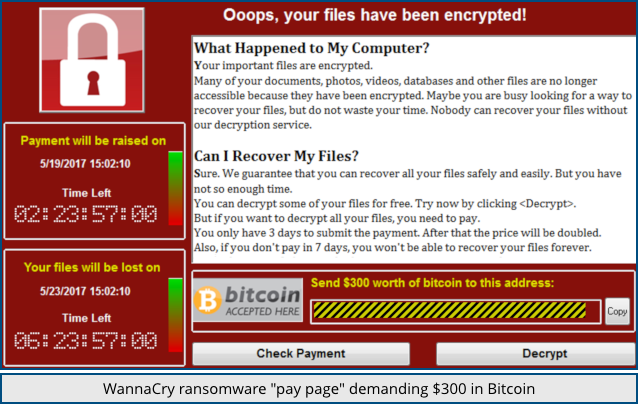
WannaCry asked for the Bitcoin equivalent of about $300 per computer, which may sound cheap by the standards of more recent targeted malware attacks in which the crooks often ask for $8000 to “save” one computer or $50,000 for your whole network.
But remember that WannaCry was a worm, too, and before it scrambled your computer it made a determined effort to infect as many other computers round and about as it could.
We’re assuming that the crooks chose $300 as a price point that many people might actually be willing and able to pay, and hoped to have literally millions of concurrent victims to extort.
Fortunately, the outbreak didn’t work out quite how the crooks had hoped.
SophosLabs estimated that as many as 200,000 computers in 150 countries got hit in the first few days, and our initial fears were that it was going to end up much worse than that.
It didn’t.
The sinkhole
A youngster in the UK going by @MalwareTechBlog, who was working from home for an internet threat monitoring company, spotted an unusual-looking server name hidden away as a text string inside the WannaCry executable file.
He acquired the domain name himself, fired up a server answering to that name, and watched to see what happened.
Note that this wasn’t an act of insight, of inspiration or of technical brilliance – he hadn’t actually decompiled or analysed the malware to figure out what the domain was for.
Indeed, registering and “lighting up” a server name that’s listed in a malware sample without knowing precisely what effect that will have is always a calculated risk.
You could end up being on the receiving end of masses of stolen, confidential exfiltrated data that you shouldn’t really be collecting; you might inadvertently activate a logic bomb in the malware that makes it even more destructive; and so forth.
Nevertheless, registering malware-related domain names is what @MalwareTechBlog and the company he worked for were accustomed to do.
As unscientific and reckless as this might sound, the process of snapping up or taking over malware domains, known by the jargon name of sinkholing, often works out well.
After all, one common purpose for hidden domain names in malware is to provide the crooks with an off-the-radar contact point “for later”, by means of which they can exert what’s known as Command and Control (usually abbreviated to CnC or C2).
If you register their off-the-radar domains before they do, you may be able to stop stolen data getting into their hands, as well as preventing them from using those domains as control servers to keep their zombie networks alive.
You also get a chance to measure how the malware is spreading and behaving, which is often useful threat intelligence, and you may even be able to use the sinkhole to push out warnings to potential victims or stop them suffering further damage.
Set the emergency brake
Time is of the essence, so @MalwareTechBlog did the right thing, for the right reasons…
…but just how right, our soon-to-be-hero was yet to find out.
It turned out that the domain he registered, activated and sinkholed was used by WannaCry as a sort of “emergency brake”.
When the virus loaded up, it tried to contact the mysteriously named server, and only continued with its file-scrambling ransomware attack if the server was not active.
Bingo!
A significant majority of the computers in the world – any of them that had a working internet connection – suddenly acquired what amounted to immunity from WannaCry.
As an aside, this is the exact opposite of a failsafe, so never code safety valves into your own software that work this way. Most countries have the rather obvious rule that if a set of traffic lights is blacked out, i.e. none of the lights are working, then you are to treat it as a red, never as a green, and software protections ought to work that way round.
So, the magic sinkhole gave potential WannaCry victims time to find and remove the malware (and, we hope, to apply the patch that Microsoft had already provided a month before).
Our reluctant hero
At first, no one knew much about @MalwareTechBlog, except that he was apparently a quiet and unassuming young man somewhere in England, working from home for a somewhat mysterious cybersecurity company with no given address, but apparently registered in the US.
@MalwareTechBlog shunned the limelight, didn’t want his name to be publicised, and politely declined to be lauded and feted for what was, after all, merely his good fortune in clipping WannaCry’s wings while doing his normal day job.
To many people, that was quite a surprise.
After all, researchers in the cybersecurity scene often go out of their way to attract PR attention for what seem like feats of derring-do: fighting off government hackers! finding new bugs with impressive names! hacking planes! taking control of cars on the freeway!
But here was a guy who didn’t seem impressed by the cybersecurity rock star bandwagon, even though he could have climbed aboard, and to many of us that that made him yet more deserving of respect and recognition.
Sin City calling!
Of course, this being the era of search engines and social media, it wasn’t long before @MalwareTechBlog was outed as a likeable youth called Marcus Hutchins…
…and after that it wasn’t long before he’d been invited to the hugely popular Black Hat and DEF CON events, held annually in Las Vegas, USA.
Who wouldn’t go, especially if they were going as a valued guest and a celebrity who’d received their fame rather than chased after it themselves?
Hutchins couldn’t regain his anonymity, so his decision to attend was hardly surprising, but it was one he was soon to regret.
What he knew, but the rest of us didn’t, is that there were other reasons than modesty for him to have stayed out of the public eye until that point.
Although he was now uncontroversially considered one of the “good guys”, he hadn’t got there by a conventional route.
As a youth and at the very start of his adulthood, he’d been part of the cybercriminal underground – simply put, he’d accepted money from illicit sources for writing malware.
So he had to take a gamble about accepting the trip.

What was the chance of his shabby past emerging during the few days he was on US soil, leaving him vulnerable to arrest by the US authorities, who have a reputation for playing hardball with cybercriminals?
Even if something did leak out due to a careless word during one of Black Hat’s or DEF CON’s legendary parties, surely he’d be back in the UK by the time the story broke, and long before the cops had time to put enough evidence together to get an arrest warrant?
And what better destination to roll the dice than Las Vegas?
Sadly for Hutchins, if that was the way he figured it, he crapped out as soon as he touched down in US territory at McCarran International Airport in Clark County, Nevada.
Person of interest
The US authorities, it seems, were already interested in Hutchins, based on evidence they had collected of cybercrimes they suspected he’d committed both as a minor and after he’d turned 18.
No matter that he wasn’t a kingpin, that he hadn’t made very much money, if any at all, and that he was operating only on the fringes of cybercrookery.
They cops surely weren’t going to miss the opportunity to nab him, and they didn’t.
They got their warrant; they knew when he was set to return home; and so they arrested him at the airport, just when he probably figured he’d rolled a seven and won his bet.
At this point, a surprising number of people in the cybersecurity scene jumped to the conclusion that the FBI was over-reaching, that the charges must be bogus and that Hutchins was clearly not a crook.
We saw an efflux of scorn and hatred against American law enforcement, with numerous “experts” assuring us that they and any number of others could vouch for Hutchins, and that he was being falsely accused simply because he seemed to know something about WannaCry that no one else did.
Hutchins, as a stranger in serious trouble in a strange land, must have been happy to have so many visible and vocal supporters, but the blind prejudice of some of the “support” he received must also have caused him some concern.
In truth, most of the people leaping to declare his innocence didn’t really know him at all, and were in no position to vouch for him in any meaningful way other than to say, “We first heard of him only recently, but we quite like him. He’s easy-going, helpful and works hard.”
Those are great character references to have, but they don’t speak to guilt or innocence.
Well-known investigative journalist Brian Krebs admitted at the time that he too wanted to believe in @MalwareTechBlog’s innocence, but figured that he’d better dig into Hutchins’s background a bit before forming an opinion.
After three weeks of “joining the dots”, Krebs published a piece in which he said:
At first, I did not believe the charges against Hutchins would hold up under scrutiny. But as I began to dig deeper into the history tied to dozens of hacker forum pseudonyms, email addresses and domains he apparently used over the past decade, a very different picture began to emerge.
Out on bail
For almost the next two years, Hutchins was permitted to remain on bail in Los Angeles, California, and indeed to continue working to defray the cost of staying in the country for his trial.
As Hutchins himself wryly quipped at the time, it was like he’d landed a much-sought-after work permit, but one with the strings of Damocles attached.
Then, in April 2019, Hutchins reached a deal with the prosecutors, and pleaded guilty to two criminal charges; the other charges that he faced were dropped as part of the deal.
His sentencing was set for July 2019, and many of us hoped that he would be treated leniently, given his apparently improved behaviour as a gainfully employed adult.
At the time, we offered the opinion that:
We’re not expecting Hutchins to get away with a suspended jail term or a fine followed immediately by deportation to the UK, however effective such a sentence might sound. After all, the US courts may want to establish a clear disincentive for other youngsters who are toying with the idea of a “career” that involves attacking the online lives of innocent victims with malware.
So we’re guessing that he’ll go to prison to serve some sort of custodial sentence, although we can’t see him getting a full five-year stretch, and given his guilty plea and his public admission of wrongdoing, we hope he doesn’t.
In the past few weeks, we started to think that Hutchins and his legal team might have known ahead of time how his sentencing would turn out, because he started talking wistfully about “going home soon”, as though he was expecting to be deported immediately.
Indeed, that’s sort of how it ended.
Hutchins was sentenced to “time served”, meaning that he has, technically, received and served a prison sentence, with the time he spent in custody before getting out on bail considered to be sufficient incarceration.
He was also sentenced to a year of supervised release, meaning that although he’s free from prison, he’s not legally free in every sense.
But he can leave the US, and presumably will have to do so soon.
After all, he no longer has the “work permit” that he was afforded by being out on bail, and it’s unlikely he’ll ever get a US work permit in the future – or even a visitor’s visa – given that he’s a convicted felon.
Here’s what Hutchins himself said:
Sure, he’d be a fool indeed to say anything negative at this point, so cynics will probably dismiss this tweet with the words, “But he would say that.”
Nevertheless, he did say it, and we’re willing to assume he really meant it.
Was justice done?
We think he got off lightly; we think that for years to come he’ll benefit from the rock star status he initially sought to avoid; and we suspect that he will, perhaps unfairly, now enjoy very much better career prospects than cybersecurity researchers of equivalent ability who have scrupulously done the right thing all their lives…
…but we also recognise that he’s spent the last two years on bail in the US, facing serious criminal charges and an uncertain future that might very well have included a spell in a US prison.
A commenter on an earlier article we wrote about Hutchins demanded:
Please stop glorifying what he did and treating him as a hero. He is a criminal and deserves jail time.
At the time we replied by saying:
Do we think he’s a gifted and excellent cybersecurity researcher? No. He doesn’t yet have the knowledge or experience. (If you look at his recent posts about learning to code, we think he agrees with that.) Do we think he’s a prolific and unreconstructed cybercrook who will inevitably be a recidivist? No. We don’t have any science for that and we can’t prove it – but on the balance of probabilities we think he was a small-time player drawn into the malware scene as a kid and that he’d be nuts to try to get back into that game when he gets out.
So we’re going to finish by saying, “Yes. We think justice was done.”
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/2E-U5fgwrNI/