 Last month, a panel of presidential advisors recommended that the National Security Agency’s (NSA’s) massive data trawling carry on, but that the data be kept in private hands for “queries and data mining” only by court order.
Last month, a panel of presidential advisors recommended that the National Security Agency’s (NSA’s) massive data trawling carry on, but that the data be kept in private hands for “queries and data mining” only by court order.
On Friday, US President Barack Obama gave a speech at the Department of Justice in which he called for just that: an end to the NSA’s maintenance of a database containing US persons’ phone records.
From his speech:
I believe critics are right to point out that without proper safeguards, this type of [telephone metadata bulk collection] program could be used to yield more information about our private lives and open the door to more intrusive bulk collection programs in the future. They’re also right to point out that although the telephone bulk collection program was subject to oversight by the Foreign Intelligence Surveillance Court (FISC) and has been reauthorized repeatedly by Congress, it has never been subject to vigorous public debate.
I believe we need a new approach. I am therefore ordering a transition that will end the Section 215 bulk metadata program as it currently exists and establish a mechanism that preserves the capabilities we need without the government holding this bulk metadata.
In other words, the bulk collection of phone metadata will continue, but the hands on the reins of that data will change, as the president’s panel recommended.
As pointed out by American Civil Liberties Union (ACLU) Staff Attorney Alex Abdo in an annotated version of the speech, the president only addressed changes to the bulk collection of telephone data while ignoring bulk collection of financial records, email metadata, or location information, among other data types.
And whose hands will take over?
Obama didn’t specify.
Saying the transition “will not be simple”, he left the details up to Attorney General Eric H. Holder Jr. and Director of National Intelligence James R. Clapper.
The intelligence review group had recommended that the current approach be replaced by one in which the telephone service providers or a third party retain the bulk records, with government accessing information as needed.
The president gave Holder and Clapper until 28 March to come up with somebody to whom the intelligence database buck may be passed and a new way to pass it.
So that’s one deadline.
But as the Washington Post noted, there’s another date, June 2015, that many in the administration are more worried about still.
That’s when Section 215 of the Patriot Act – the law that authorizes the bulk collection of Americans’ phone records – is set to expire.
Administration officials requesting anonymity told the newspaper that there’s little chance that the authority granted by that law will be renewed, given the ferocious backlash triggered by whistleblower Edward Snowden’s revelations.
The Washington Post quotes one official who wasn’t authorized to discuss the matter:
Congress’s deadline hangs over all of this.
But the authority granted by Section 215 certainly won’t die without a load of squealing.
Defenders of the data collection program issued a statement that played up Obama’s remarks about the importance of the program in supposedly thwarting terrorist plots.
From the joint statement from the chairmen of the House and Senate intelligence committees, Sen. Dianne Feinstein (D-Calif.) and Rep. Mike Rogers (R-Mich.):
The president underscored the importance of using telephone metadata to rapidly identify possible terrorist plots, a gap that existed on September 11, 2001, and which has been closed through the NSA’s collection of telephone metadata under Section 215 of the USA PATRIOT Act. As the president said, this is a capability that is ‘critical’ and must be ‘preserved’.
In Friday’s speech, Obama also said that the government will have to obtain a court order for each phone number it wants to query in its records database.
Also, the number of steps a given phone call is away from a terrorist organisation in order for it to be snoop-able is shrinking.
Before, intelligence analysts could review calls that were three steps away. Now, they’ll only be able to query calls that are two steps removed.
The ACLU’s Abdo notes that this is an “important narrowing” of the government’s phone-records program:
The so-called ‘three hop’ queries [intelligence analysts have] been using since 2006 likely swept up many thousands — or even millions — of innocent Americans. Two hops might not be the right answer, either, but it is certainly an improvement.
But it’s one seemingly unremarkable passage that Abdo singles out as the “single most significant passage of the speech.”
The passage from Obama’s speech:
During the review process, some suggested that we may also be able to preserve the capabilities we need through a combination of existing authorities, better information sharing and recent technological advances, but more work needs to be done to determine exactly how this system might work.
And Abdo’s interpretation of why this part matters more than anything:
If President Obama wants to end bulk collection – both by the government and through forced data retention by the companies – then individualized surveillance using existing authorities is the answer.The problem with bulk collection is that it puts the search before the suspicion.
Other parts of the president’s speech pertained to spying on foreign leaders.
In spite of the fact that every other country is spying on each other and they all know it, Obama said, and some countries privately thank the US for the benefits they get from its snooping, he said, the country will no longer eavesdrop on dozens of foreign leaders and governments that are friends or allies.
That move will, the administration is likely praying, appease a cadre of very indignant and much spied-upon foreign leaders such as German Chancellor Angela Merkel.
The president’s policy directive included a number of other facets, including getting input from a newly established panel of advocates from outside government to provide an independent voice in significant cases before the FISC.
Here’s the transcript of the full directive.
All in all, civil liberties groups were unimpressed by Obama’s directive.
Anthony D. Romero, the executive director of the ACLU, said in a statement that increased transparency for the FISC, improved checks and balances at the FISA (Foreign Intelligence Surveillance Act) court through the creation of a panel of advocates, and increased privacy protections for non-US citizens abroad are all “necessary and welcome reforms.”
But the continuance of the bulk data collection and retention is “troubling”, he said, and called on it to come to an end:
The president’s decision not to end bulk collection and retention of all Americans’ data remains highly troubling. The president outlined a process to study the issue further and appears open to alternatives. But the president should end – not mend – the government’s collection and retention of all law-abiding Americans’ data. When the government collects and stores every American’s phone call data, it is engaging in a textbook example of an ‘unreasonable search’ that violates the Constitution. The president’s own review panel recommended that bulk data collection be ended, and the president should accept that recommendation in its entirety.
Image of Obama courtesy of Filip Fuxa / Shutterstock.com
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/Kw5TMlQ_PiA/
 A routine visit to the home of a registered sex offender in the UK has led law enforcement to bust an international organised crime group centered in the Philippines that arranged, and profited from, children being sexually abused live on webcam.
A routine visit to the home of a registered sex offender in the UK has led law enforcement to bust an international organised crime group centered in the Philippines that arranged, and profited from, children being sexually abused live on webcam. Starbucks got into and out of privacy trouble over the past week.
Starbucks got into and out of privacy trouble over the past week.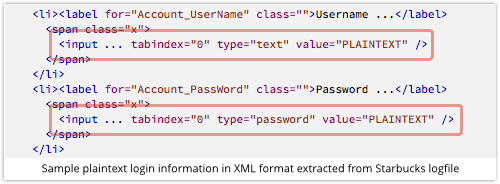
 Last month, a panel of presidential advisors
Last month, a panel of presidential advisors  Security and privacy problems seem to have grown bigger and badder over the last year, with ever larger
Security and privacy problems seem to have grown bigger and badder over the last year, with ever larger