With security expertise continuing to be in short supply, managed and cloud services will play a greater role in securing companies in 2014.
Benefiting from the knowledge of managed security service providers–or the built-in expertise in existing cloud security services–can help non-technical companies build the infrastructure needed to stay secure. For more security-savvy companies, service providers can take over the day-to-day security drudge work, and allow internal security teams to focus on bigger security issues that may be affecting the company, says Neil MacDonald, a vice president and fellow at business-intelligence firm Gartner.
“If I’m an organization with limited resources, I would rather free up my security team’s time to focus on more advanced threats rather than the more routine things like log monitoring, firewall management and vulnerability management,” he says.
Whether a company pursues a managed security service, a cloud security service, or some hybrid with their existing capabilities, depends largely on their own expertise and whether the organization already uses the cloud for existing business processes, says Rob Ayoub, research director for NSS Labs, a security consultancy.
“A lot of it depends on how they are using the cloud,” he says. “Are they using the cloud as an extension of their existing infrastructure? Or are they using the cloud and consuming services from the cloud as a way to expand their security capabilities or maybe because they do not have the in-house expertise.”
Whichever may be the case for your company, the following services could be in your future this year.
1. Cloud asset control
Most companies do not know how much they rely on the cloud, frequently underestimating the number of cloud services being used by employees. From its own customer data, for example, cloud-management provider Skyhigh Networks has found that the average firm uses approximately 550 cloud services.
In the past few years, a number of startups–such as CloudPassage, Netskope and Skyhigh Networks–have focused on the problem of taming the wild and varied adoption of cloud services. These cloud-application visibility services allow companies to discover what services they are using, the risk those services pose and then manage the threat, says Jim Reavis, co-founder and CEO of the Cloud Security Alliance.
“These types of services give you a pretty good visibility into what cloud services are in use, and allow companies to take the next step and implement controls,” he says.
2. Log management to incident detection
Many companies already use a service provider to collect and manage logs, archiving the data for compliance purposes. With an increasing focus on network and business visibility, companies need to turn those logs into information on what is happening in the network.
The category actually covers a spectrum of services, from log management to security information and event management (SIEM) systems to Big Data analytics. Once companies have their log monitoring in the cloud, there is no reason not to look at analyzing the data, says Gartner’s MacDonald.
“They can essentially tell you if you have been compromised,” he says. “That can be intensely interesting, especially if you are a smaller organization and you don’t have the resources to build a security operations center.”
[Companies need cloud providers to delineate responsibilities for the security of data, provide better security information, and encrypt data everywhere. See 5 Ways Cloud Services Can Soothe Security Fears In 2014.]
Eventually, a focus on detection will turn into a focus on response and shutting down attackers, making incident-response services–such as what may come from FireEye’s purchase of Mandiant–likely to significantly grow over the next few years
3. Identity Management
As companies rely on an increasing number of cloud providers, managing access to those services has become more complex. Identity and access management in the cloud makes a lot of sense for firms who use a large number of cloud services, says CSA’s Reavis.
“There is a real risk that employees duplicate their identities out on the Internet, and that raises the risk of a lateral attack, where a breach at one provider allows attacker to breach the employee’s other accounts,” he says.
4. Encryption
The revelations that the U.S. National Security Agency is collecting massive amounts of data from the Internet has caused more companies to pay attention to how their data is secured in the cloud. While locking down data at rest with encryption is a good idea, especially when it is outside the firewall, many companies had been relying on the security of their storage providers to protect the data.
While a number of cloud services focus on encrypting data in cloud services, CipherCloud and Voltage Security, the market is still nascent. That will likely change this year, as cloud services focusing on encryption and access-management grow, says NSS Labs’ Ayoub.
“I think identity and encryption are the two areas where were we will see a lot of adoption this year,” says Ayoub. “We need to focus on protecting who’s accessing the data, and we need to focus on protecting the data.”
5. Security testing in the cloud
Many companies have to focus on securing their software, not just their networks, whether the software is internally developed or comes from third parties. Outsourced application testing or application-testing in the cloud are able to find the most common bugs, can help train developers, and hold third-party software firms to a standard security assessment.
“Application security testing is more difficult work, but it is becoming better understood,” he says. “By using one of these vendors to test their applications or require that their supply-chain partners to test their applications, they can enhance their security.”
A number of companies offer application testing and assessment services in the cloud, including Cenzic, Cigital, Veracode, and Whitehat Security.
Have a comment on this story? Please click “Add Your Comment” below. If you’d like to contact Dark Reading’s editors directly, send us a message.
Article source: http://www.darkreading.com/services/5-security-services-to-consider-in-2014/240165414
 As we reported recently, Facebook has been asking its users whether they think it is trustworthy (whatever that means), but it’s not actually sharing the results.
As we reported recently, Facebook has been asking its users whether they think it is trustworthy (whatever that means), but it’s not actually sharing the results.  Last week a cluster of surveys were released, showing some contrasting views of the main sources of IT security risk, and some revealing overlaps.
Last week a cluster of surveys were released, showing some contrasting views of the main sources of IT security risk, and some revealing overlaps.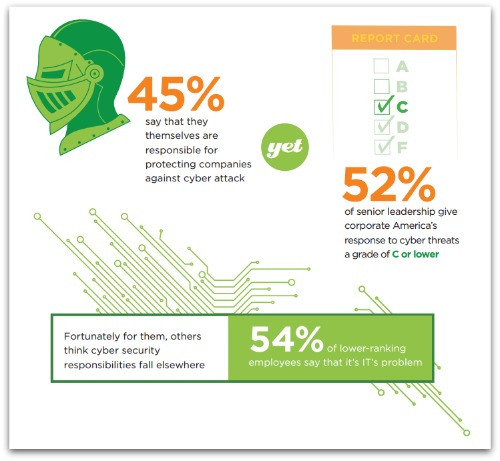
 Even after multiple breaches all over the place, which you’d think would put most people in similar positions on their guard, it’s still possible to fool people into handing their login details over.
Even after multiple breaches all over the place, which you’d think would put most people in similar positions on their guard, it’s still possible to fool people into handing their login details over.
 Google just
Google just  As we reported recently, Facebook has been asking its users whether they think it
As we reported recently, Facebook has been asking its users whether they think it