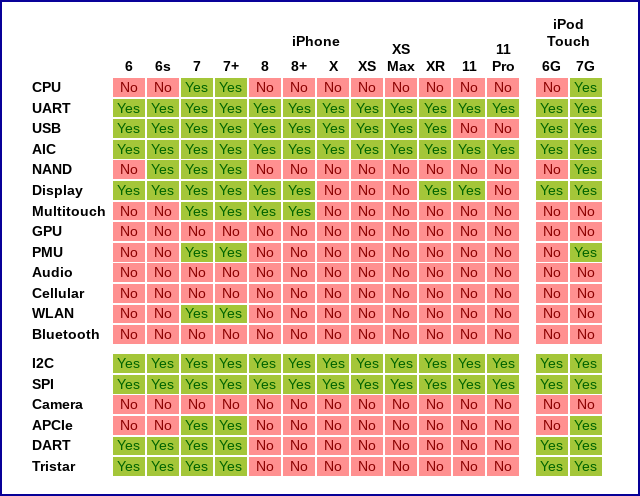
The former Supreme Allied Commander of NATO gives Dark Reading his take on the greatest cyberthreats our nation and its businesses face today.
By any standard James Stavridis has had a remarkable career, beginning with graduation from the U.S. Naval Academy (with a degree in electrical engineering), rising through the ranks of officers to commander of the U.S. Southern Command and U.S. European command to his final position as Supreme Allied Commander Europe.
During his career, Stavridis earned a Ph.D in Law and Diplomacy. After retiring from the Navy, he became dean of The Fletcher School at Tufts University and began a publishing career.
Stavridis serves on the boards of a number of organizations and is a frequent speaker on international politics and technology, most recently at the RSA Conference. Following the conference, Dark Reading’s Curtis Franklin had a chance to talk with the Admiral by phone for a conversation that touched on the cyber security issues that are at the top of his mind for both governments and the enterprise. It’s no surprise that Stavridis has thought quite a bit about cyber threats to the U.S. What may be more surprising is his take on what the government’s role should be when it comes to helping companies defend themselves against some of the same threat actors that bedevil national security agencies.
What follows is an edited transcript of their conversation.
Dark Reading: As you survey the cybersecurity landscape, what concerns you the most?
James Stavridis: In cyber, we see the greatest mismatch between level of threat and level of preparations. In the physical world, we had a lot of threats. You know, Russia. Afghanistan, Libya, the Balkans, piracy — lots of threats, but we were pretty well-prepared to deal with most of them. Unfortunately, in cyber, there was a real gap, and I think continues to be a real gap. I see a lot of concern in the geopolitical space. And I see a lot of concern in the national electoral space. Those are my two areas of real concern and focus right now.
Dark Reading: When it comes to nation-state adversaries, are they something that only our defense department should be concerned with, or should all commercial organizations be concerned?
Stavridis: It is the latter. I often say this about cybersecurity, that we’re still on the beach at Kittyhawk. We’re still figuring out how this is going to work. To shift metaphors to the oceans, it’s as though we’re out at sea, we’re in a bunch of boats, but we haven’t really put in place buoys and navigational aids, and we haven’t really defined who’s going to protect us.
So if if I’m a commercial ship at sea, I know the U.S. Navy is going to come and defend me if I’m an American ship and I’m under attack. And in fact, we actively discourage merchant ships from mounting their own defenses. The defense requirements, I think, ought to be vested in the state.
But in the world of cyber, realistically, if you’re a commercial entity, particularly a target-rich kind of environment like financials or critical infrastructure, say electric grid, the government so far has not really stepped up to that task of broadly protecting you.
Yeah, you can get some help from the NSA and some help from the FBI and some help from the CIA. But broadly speaking, you are going to have to have some mechanisms, at least on the detection and on the defensive side.
I’ll give you a practical example. The eight largest banks in the United States got together and created something called the Financial Systemic Analysis Resilience Center (FSARC). They hired an absolutely terrific cybersecurity expert [to be president and CEO], a guy named Scott DePasquale, [formerly partner at New York based venture capital fund Braemar Energy Ventures]. And they’re hiring people from FBI, CIA, DOJ, DHS. And they are building, effectively, a community of defensive measures and information sharing, just like the title says, analysis and resiliency. We as citizens ought to be encouraging the government to do more of this. In the meantime, I think that many of these commercial entities are going to have to find ways to defend themselves better.
Dark Reading: There are industries where there is some concern about how the government will view sharing information between potential competitors in an industry, whether this creates some sort of anti-competitive environment. Is this the kind of area where we need to continue to evolve the way that regulators look at the activity, or are we on top of this?Stavridis: We are not on top of it. It needs encouragement, and I think this has to be driven within the industries themselves. They need to understand that they are stronger together, in that if they try and stand as lonely citadels protecting themselves, they will lose. This is a team sport.
And I think the government also has a significant role to play. I’ll give you an example. The Congress two years ago finally passed the Cybersecurity Information Sharing Act, which takes a baby step in exactly the direction you just outlined. It formalizes the idea that companies should share information to best protect themselves. And let me give you an example.
You probably fly around frequently. You probably flew to [the RSA Conference], so you willingly put yourself in a metal tube, went up 35,000 feet flying three [to five] hundred miles an hour. Holy cow.
That doesn’t sound very safe, does it? And yet, that’s one of the safest things you can do. That’s safer than walking across the street, and it’s a lot safer than driving in your car on the freeway. We all know that. And that’s why we don’t have a shred of discomfort getting in that metal tube and flying around at high speed.
Why is that? It’s because the airline industry is an example of what the cyber security industry should be doing, what what financial should be doing, what the electric grid company should be doing, what the water utilities should be doing. They should share information.
What happens when a plane crashes? Everybody descends on it. It’s totally transparent. If the left aileron on a 777 was out of place, inexplicably, what would happen? The whole fleet would be grounded globally until we figured out what happened. All that information is transparent and it’s shared. What happens in the cyber side of things, too often, is when companies are attacked, their instinct is to hide the ball.
Why is that? Because their share price will fall. And there’s no incentives built into the system to be open, the incentives go in the other direction, whereas in the airline industry, the massive incentive is that if people lose confidence in flying in those planes, the whole industry is toast. So I think that the cyber side of industry needs to look more like the airline industry.
(continued on next page)
Curtis Franklin Jr. is Senior Editor at Dark Reading. In this role he focuses on product and technology coverage for the publication. In addition he works on audio and video programming for Dark Reading and contributes to activities at Interop ITX, Black Hat, INsecurity, and … View Full Bio
Article source: https://www.darkreading.com/edge/theedge/out-at-sea-with-no-way-to-navigate-admiral-james-stavridis-talks-cybersecurity/b/d-id/1337253?_mc=rss_x_drr_edt_aud_dr_x_x-rss-simple
 Check out The Edge, Dark Reading’s new section for features, threat data, and in-depth perspectives. Today’s featured story: “The Perfect Travel Security Policy for a Globe-Trotting Laptop.”
Check out The Edge, Dark Reading’s new section for features, threat data, and in-depth perspectives. Today’s featured story: “The Perfect Travel Security Policy for a Globe-Trotting Laptop.”
 Check out
Check out