Top 5 IT Risk Management Resolutions For 2014
As IT risk management and security professionals steel themselves for another year of high-profile breaches, increasingly sophisticated attacks and continued regulatory scrutiny on their controls, now may be the perfect time to re-examine risk management priorities. While every organization is unique, risk management pundits believe there are certain common initiatives that could stand more attention among many enterprises. The following five resolutions—listed in no particular order–are among the top ways that risk managers can take their practices to the next level in 2014.
Resolution #1: Improving Third-Party Risk Management
As news of more breaches and security incidents caused by third-parties make the news, enterprises and regulatory bodies alike are sharpening their focus on risks posed by vendors and partners entrusted with their data. According Andrew Wild, CSO of Qualys, he expects third-party risk management to be a key area of focus for IT risk professionals this year.
“The growing reliance upon third parties requires a mature third party risk management program to ensure risks are properly identified, assessed and managed,” Wild says, pointing to new regulatory requirements such as the guidance issued for banking institutions by the U.S. Office of the Comptroller of the Currency. “However, even organizations with no regulatory or compliance program requirements for third party risk management face increased scrutiny from customers about third party risk management.”
Resolution #2: Tune Risk Management For Greater Flexibility And Response
Targeted and stealthy attacks will continue to press security practitioners to change their methods to deal with them.
“The damage generated by those targeted attacks will be significant enough to drive further migration from static border protection and access control-based security programs, to dynamic programs that analyze new threats and risks on a daily basis and drive upgrades, updates and system changes,” says Rich Dakin, chief security strategist for Coalfire.
This, of course, means that risk analysis needs to advance way beyond simple yearly risk assessments if risk managers are to make meaningful calculations that can drive decisions about IT infrastructure and processes. Not only should organizations be seeking better ways to feed real-time information into risk assessments, but they also should be seeking ways to more quickly adjust existing technology according to those assessments rather than simply trying to buy their way out of newly identified risks.
“Businesses often assume they need new controls to address subsequent risks, but often times they can adjust existing controls to address new risks,” says Gerrit Lansing, director of consulting services for CyberArk Software.
Resolution #3: Use More Data To Assess Risks
Part of that push to a more evolved risk assessment involves better incorporation of data into the process. As important as questionnaires and the like may be to understanding processes and practices, data mined from security technologies and IT infrastructure are equally important to validate that the assumptions made when answering questions are truly valid.
“Many organizations do not utilize the facts and data that are present in their environment,” says Amad Fida, CEO of Brinqa. “They miss the opportunity to analyze and correlate those responses with security data from their systems and controls they have in place.”
[Are you getting the most out of your security data? See 8 Effective Data Visualization Methods For Security Teams.]
Resolution #4: Collaborate With Business Users For More Pervasive Risk Management
The security elite have long preached the need for better alignment between IT security practices and the business. That starts first with increased collaboration in the risk-management process between risk managers and business users both inside and outside the organization, says Yo Delmar, vice president for MetricStream.
“Essentially risk, compliance, and security functions will have inputs from the first line of defense business users, suppliers, franchisees, and so on,” Delmar says, explaining that means providing a risk management platform that supports widespread useage for these users. “Risk management will increasingly be tied with performance management and will be available at the ‘point’ of action for business users. For example, if a company is working with high risk vendors, it will not be enough to just do an assessment of the vendor regularly, but rather systematically tie performance indicators and negotiations for renewals to that vendor risk assessment directly.”
Resolution #5: Balance Preventative Controls With Detective Controls
More organizations should resolve themselves to improve the balance between preventative and detective controls, Wild says.
“In the past, many companies almost exclusively relied on preventative controls, which is not 100% effective,” he explains. “Because of this, the use of detective controls to ensure security incidents that aren’t prevented can be discovered, contained and remediated.”
At the end of the day, this balance should be driven by a solid risk management-based security framework.
Have a comment on this story? Please click “Add Your Comment” below. If you’d like to contact Dark Reading’s editors directly, send us a message.
Article source: http://www.darkreading.com/risk/top-5-it-risk-management-resolutions-for/240165296
 The control centre of a nuclear power plant really doesn’t sound like the sort of place you’d want to see a malware infection.
The control centre of a nuclear power plant really doesn’t sound like the sort of place you’d want to see a malware infection. In any business setting, software should only be running if it is approved and maintained by IT staff, who should keep a close eye on any updates to make sure they don’t include any connecting-repeatedly-to-somewhere-they-shouldn’t components. This applies to all machines, however non-mission-critical they may be.
In any business setting, software should only be running if it is approved and maintained by IT staff, who should keep a close eye on any updates to make sure they don’t include any connecting-repeatedly-to-somewhere-they-shouldn’t components. This applies to all machines, however non-mission-critical they may be. Oh, the humanity: it was revealed on Monday that
Oh, the humanity: it was revealed on Monday that  Botnets, short for robot networks, are more than just malware: they’re the money making machinery of modern cybercriminals.
Botnets, short for robot networks, are more than just malware: they’re the money making machinery of modern cybercriminals.


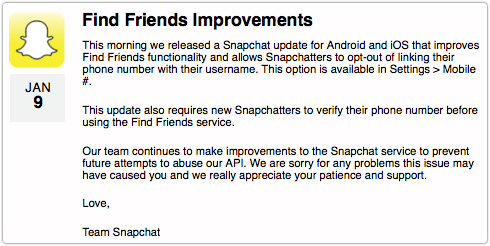
 Team Snapchat, as it calls itself, has finally used
Team Snapchat, as it calls itself, has finally used