A security researcher has discovered a pair of zero-day vulnerabilities in a popular family of Siemens industrial control system switches that could allow an attacker to take over the network devices without a password.
Eireann Leverett, senior security consultant for IOActive, next week at the S4 ICS/SCADA conference in Miami will release his proof-of-concept code for users of the SCALANCE X-200 Switch family to test the flaws in their industrial control systems (ICS) environments. The researcher found the bugs a few months ago and reported them to Siemens, which last fall issued patches for the flaws, within three months of being notified.
Whether ICS/SCADA customers will actually apply the patches or just how quickly they will do so is the big question. The aftermath of Stuxnet has pressured some major ICS vendors like Siemens to regularly respond to vulnerability discoveries in their products with patches and updates to their software. But their customers, utilities and other process control operators, don’t routinely apply those patches: overall, only 10- to 20 percent of organizations do so, mainly because they face the risk of a power or plant operation disruption caused by a newly patched system.
Leverett says releasing his PoC code is all about giving Siemens customers a chance to test just what the newly discovered vulnerabilities could do. Many vulnerability and patch reports don’t include enough specifics on the potential implications of the flaws, he says. “My personal goal is to make sure asset owners have a chance to say, ‘how bad is it? What can I do with it?”
“If I give them the code … then their Python guy can run it” and see first-hand that you don’t need a password to update the firmware, for example.
The Siemens switch zero-day vulnerabilities are in the Web server interface to the devices. The researcher says the first of the two zero-day flaws he found in the Siemens SCALANCE X-200 switch was a basic one: a poorly constructed session ID setup, which would allow an attacker to hijack an administrative session on the switch without credentials. The session ID basically exposes the client’s IP address so an attacker could then hijack the admin’s Web-based session while managing the switch. “But you don’t log onto these switches very often – maybe once a year – so in that sense, it’s a weak vulnerability,” he says.
The more critical zero-day Leverett found in the switch was the second one, which would let an attacker take over the admin operations of the switch – no authentication required. The attacker could then download any network configuration information, or upload a malware-ridden firmware update, for example, Leverett says. “The device assumes if you know the URL, you must have authentication. But it never asks you to authenticate” for it, he says.
“Once I realized that you can change the firmware on the device, it was game over,” he says. “You could have access to all traffic to the switch and exfiltrate data, figure out” other features of the network and “sniff” other credentials and upload malware-laden firmware, he says.
The SCALANCE switches are small, with eight Ethernet ports, and most likely run in small process control environments or in hardened outdoor networks, he says. “I don’t have a good sense in how often they are used in critical infrastructure” environments, he says. Even so, both flaws are simple to exploit, he says.
Siemens issued updates to the SCALANCE X-200 switch firmware, to V5.0.1 and V5.1.2, which fixes the Web session hijacking bug and the Web server authentication flaw.
The vendor provided the security advisories it had issued for its customers in October when asked for an interview for this article.
“Siemens has been very helpful and produced the patches in a timeline that a couple of years ago would have felt impossible,” Leverett says. “I’m going to use that to challenge the rest of the industry” to quickly respond and fix bugs, he says.
[ICS/SCADA expert Ralph Langner published a report looking at how Stuxnet shifted from super-stealthy to simpler, and dispels common misconceptions about the infamous Stuxnet attack on Iran’s nuclear facility — including the belief that only a nation-state could pull off a similar attack in the future. See Stuxnet’s Earlier Version Much More Powerful And Dangerous, New Analysis Finds.]
Leverett says one purpose of his presentation at S4 next week is to urge ICS vendors to come clean with more specifics on flaws so their customers can better understand the risks, and thus be more compelled to apply the patches.
“You find these vulnerabilities in ICS equipment all the time,” Leverett says. “My talk [at S4] will be about how well vendors are informing end users about the security of their products, and how could we do that better … We should be able to give them a more clear, unified response from all of us.”
Siemens’ advisory says this about the critical flaw: “An issue in the web server’s authentication of the affected products might allow attackers to perform administrative operations over the network without authentication.”
Leverett says he understands that Siemens doesn’t want to reveal too much in the advisory to prevent the flaw from being exploited, but more detail in the advisory would be helpful. “Siemens did a really good job,” he says. “But it would be better if Siemens … [said] you can be unauthenticated and post to this device and upload new firmware, so you’ve got to patch,” he says.
Have a comment on this story? Please click “Add Your Comment” below. If you’d like to contact Dark Reading’s editors directly, send us a message.
Article source: http://www.darkreading.com/vulnerability/zero-day-flaws-found-patched-in-siemens/240165252
 Last week I saw a post by Computerworld journalist Gregg Keizer about the
Last week I saw a post by Computerworld journalist Gregg Keizer about the 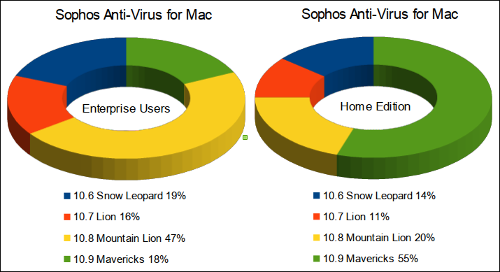
 Last week I saw a post by Computerworld journalist Gregg Keizer about the
Last week I saw a post by Computerworld journalist Gregg Keizer about the