 A study released last week by privacy campaigners Big Brother Watch (BBW) claims that as many as 1.28 million schoolchildren in the UK may have had their fingerprints taken by their school authorities last year.
A study released last week by privacy campaigners Big Brother Watch (BBW) claims that as many as 1.28 million schoolchildren in the UK may have had their fingerprints taken by their school authorities last year.
It also estimates that over 30% of schools didn’t get permission for taking fingerprints, before new regulations came into force in late 2013 which meant parental consent had to be gained.
The report’s findings have been picked up by national media and seem to be having the desired effect of drawing attention to the use of biometrics in UK schools, with the expected hand-wringing about the gradual erosion of privacy.
The use of biometrics in schools is not a new thing. Mainly relying on fingerprint reading, biometric systems have been used to record attendance, charge for catering and manage library use since at least 2001 in the UK, with early instances recorded in the late nineties in the US.
There were similar stories back then too, with civil rights campaigners highlighting the numbers being fingerprinted and the lack of proper consent.
The issue has popped up repeatedly since, with another pressure group, the now-defunct LeaveThemKidsAlone, claiming a figure of 2 million fingerprinted children in 2009.
The BBW study seems to have a rather more credible scientific basis, but still relies on a fair amount of extrapolation to reach the 1.28 million figure. Using Freedom of Information requests, they surveyed over 2,500 schools, but received responses from only 1,255. Of these, 499 admitted to using biometrics, affecting over 500,000 pupils.
These figures were then extended to cover all UK schools assuming the same ratios, to give a potential figure of 866,000 affected children for the 2012-2013 school year.
As the report was released a third of the way through the following school year, the report’s authors assume an increase in biometric use from 25% to 30% of schools, and this combined with annual overall growth figures for schools produces the 1.28 million estimate.
While many of these assumptions and extrapolations seem reasonable, they do leave the report open to accusations of hype.
The numbers themselves and even their accuracy are perhaps not so important though. Even the most pedantic of quibblers would find it difficult to deny that biometric use in schools has been growing steadily over the last decade or so, and looks likely to become the norm within the next few years.
But just because it is becoming more popular, does it mean it’s a good thing?
For the schools it certainly seems to have benefits. Everyone needs to cut costs these days, and biometric systems are apparently more efficient and cheaper to operate than old-fashioned methods based on cash, ID cards or pen-and-paper records.
But under new consent rules which came into force in September 2013, schools will have to give pupils the option to refuse to take part in biometric schemes, and even if they are up for it, written parental consent will be required for all under-18s.
According to the BBW figures measured prior to the introduction of the new rules, 31% of schools were not obtaining any kind of consent before enrolling pupils in their biometric systems.
So less high-tech techniques will have to remain available to cater to the refuseniks, which will doubtless take a chunk out of those savings.
Alongside the cost issue, some schools have pointed out the social value of the schemes, as they mean children receiving state support for meals etc. are not explicitly marked out from their peers, although it seems likely there would be other ways of achieving this.
The other side of the argument is dominated by the privacy and civil liberties angle. BBW argues that if we start indoctrinating our kids to the idea that their identity should be open to tracking and monitoring at all times, we risk reducing our society to an Orwellian nightmare of supervision and control.
Going to school should not mean kids are taught they have no privacy, especially at a time when we are sharing more data about ourselves than ever before. Fingerprinting them and tracking what they do might save some admin work but the risk is pupils think it is normal to be tracked like this all the time. Schools need to be transparent about what data is being collected and how it is used.
It won’t be long, it seems, before we’re all being identified by the barcodes tattooed on our foreheads at birth.
The use of automated systems to identify people doing different things also opens up opportunities to cross-match that data to provide deep tracking of our activities and behaviours, the sort of stuff that both advertisers and government snoops adore.
At the moment all data held by schools should be kept strictly private and destroyed when pupils leave, but given the history of schools getting into bed with fast food chains and controversial religions, many fear that selling on data to the Facebooks and Googles of the future may only be a few more credit crunches away.
The other potential issue is the security of data, which is pretty likely to be at risk from time to time, given the record of educational establishments when it comes to keeping data private and reliable.
 In some cases it’s even the kids themselves who bypass security.
In some cases it’s even the kids themselves who bypass security.
Biometrics remains a fairly new field, with the process of defining standard techniques still under way and even expensive implementations of fingerprinting fairly easily subverted. So even if these methods should be used, there are questions over whether they can be used accurately and reliably, yet.
Given all these concerns, it seems there are some strong reasons to worry about the trend of schools adopting biometrics, above and beyond the instinctive antipathy many of us have for identity tracking.
Despite this gut reaction, I can see value in simplifying authentication in schools, as in all settings. But it’s something that needs to be done with care, precision and, above all, openness. We need to know exactly what’s being tracked, how and why, what data is stored, who it’s shared with and how it’s secured, and much more besides.
Any time the way we operate our societies changes significantly, we need to analyse and debate all aspects of the change to ensure we’re going the right way. With incremental advancements in technology, there’s a danger those changes will happen slowly over time, without us noticing what might be happening.
So it’s good to see BBW and their ilk calling us on our possible ignorance to what’s been going on around us for the last decade.
Perhaps eventually people will start to take notice, and start really thinking about what privacy risks are worth taking in the name of cut costs and improved efficiency.
Images of fingerprints and hand courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/CUavlT8uoBs/
 Here’s a brief reminder of how cybercriminals use real security disasters to cause follow-up disasters of their own.
Here’s a brief reminder of how cybercriminals use real security disasters to cause follow-up disasters of their own.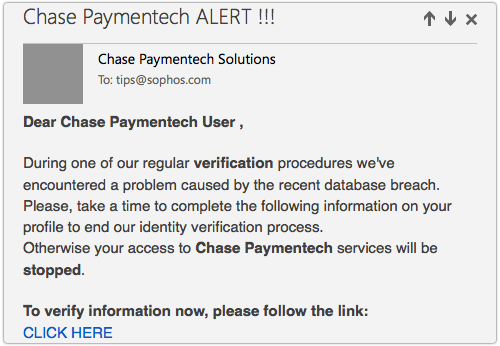
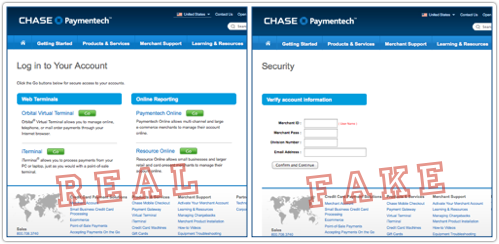
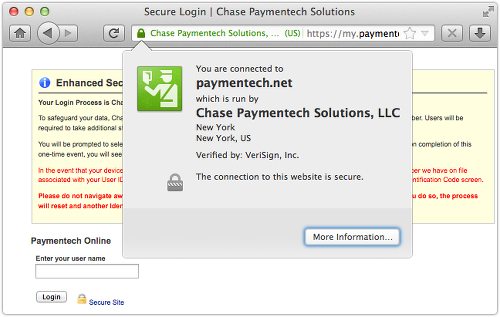
 It’s the first calendar quarter of the year.
It’s the first calendar quarter of the year.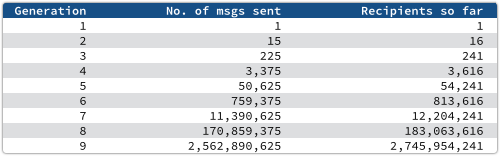
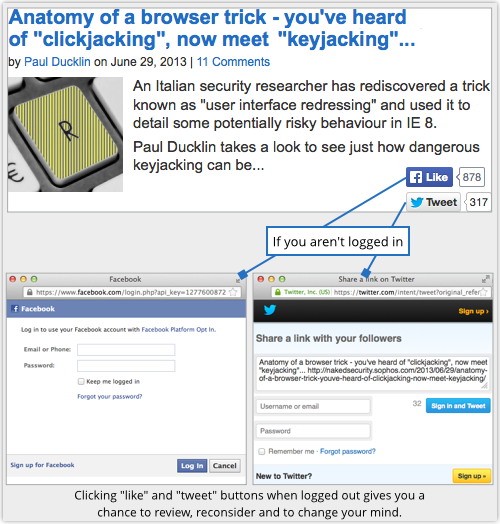
 A
A  In some cases it’s even
In some cases it’s even