Watch out! Facebook is NOT closing in March
 It’s the first calendar quarter of the year.
It’s the first calendar quarter of the year.
With February and March on the visible horizon, we’re seeing the annual reappearance of “Facebook is closing” hoaxes.
The hoaxes look something like this:
Dear Facebook members, Facebook is supposed to be closing down March 15th because it is becoming very overpopulated. There have been many members complaining that Facebook is becoming very slow. Records show that there are many active Facebook members and also many new members. We will be sending this message around to see if members are active or not. If you are active please send to 15 other users using copy+paste to show that you are still active. Those who do not send this message within 2 weeks will be deleted without hesitation to make more space. Send this message to all of your friends to show that you are still active and you will not be deleted. Founder of Facebook. Remember to send this to 15 other people so your account wont be deleted.
It certainly sounds unlikely, doesn’t it?
Facebook closing down because it has too many members?
Facebook trying to reduce traffic by kicking off members who do nothing (and who thus produce no traffic), yet keeping members who participate in a chain letter that produces only a giant flurry of wasted traffic?
Mark Zuckerberg, who was born, bred and educated as an Anglophone American, writing in such stilted English?
And the reason it sounds unlikely is because it is unlikely, and it’s unlikely because it’s a pile of garbage.
Invitations to participate in chain letters should always be avoided, because getting involved is almost like joining in a DDoS attack: you’re generating loads of wasteful traffic, and actively urging others to do the same.
The problem with chain letters is that if they succeed, their distribution grows exponentially, at least for a while.
To see why, let’s do the arithmetic.
We’ll assume perfect propagation, where each recipient sends the message to 15 brand new recipients. (That’s admittedly very unlikely, but we’re looking at the principle here.)
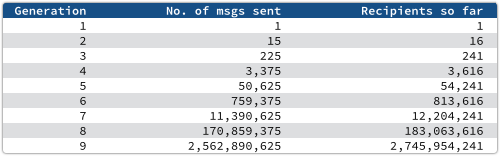
In other words, by participating you become part of the problem, not part of the solution.
Other popular “Facebook closure” memes in previous years have warned you about Facebook closing from 29-31 February, a hoax that is rather more obvious (at least in non-leap years, when February has only 28 days), but still seems to attract plenty of interest.
Frictionlessness
One of the problems with modern social networking is the concept of frictionlessness, which is a measure of how easy it is to interact with the system.
This is one of the reasons that Facebook and other online services like Twitter are happy for you to be logged in all the time: the buttons they provide for liking, sharing, retweeting, endorsing, approving, and so on, work with a single click if you are logged in.
If you make a habit of logging out of Facebook, Twitter and other services when you are not actively engaged with them, you will add a tiny bit of hassle to your digital life.
But you will stop yourself being sucked into hoaxes, scams, bait-and-switches, and much more, if you are logged out more than you are logged in.
That’s because an ill-considered or an unexpected click on a social networking button will bring up a “You need to login” dialog whenever you are logged out.
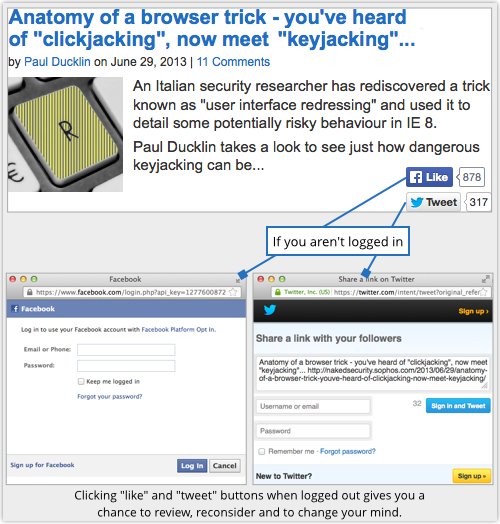
This gives you a second chance to consider if you really intended the action you just performed, as well as keeping you safe from malicious behaviour such as clickjacking.
Clickjacking is visual trickery that makes you think you are clicking on something of your own choice, but behind the scenes you are clicking – and thus endorsing – something else entirely, such as a Like.
Stray clicks, fallacious likes and bogus tweets are all easy to propagate when you stay logged in to social networking services as a matter of routine.
Further information
If you’re in any doubt as to how this can contribute to the problem, sucking in yet more victims, take a look at this Bait-And-Switch video, where we look at how fake Tweets can put other people in harm’s way:
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/BbQOLwrDwv4/

