Snapchat praises itself over giant phone number carelessness
 On New Year’s Day we wrote about a giant phone number leak from controversial photosharing site Snapchat.
On New Year’s Day we wrote about a giant phone number leak from controversial photosharing site Snapchat.
Here’s what happened.
Snapchat implemented a search service so that you could put in a friend’s name and phone number, and find out their Snapchat handle.
Assuming, of course, that they had a Snapchat login, and that they had felt it prudent to tell Snapchat their phone number in the first place.
With hindsight, we now know that it was not at all prudent to entrust phone numbers to Snapchat, because the company did two things that were contradictory from a security point of view:
- It created an easy-to-use web interface by which anyone with a Snapchat account could perform phone number lookups in bulk. (A single request could apparently contain tens of thousands of numbers to check at the same time.)
- It “prevented” overuse – or abuse – of this interface by publishing terms and conditions that told you not to use it without permission.
But with several open source projects available that showed how to use the Snapchat web programming interface, it was really only a matter of time before someone decided to risk being kicked off Snapchat by going after those badly-shielded phone numbers.
Matters weren’t helped when a self-appointed security collective calling itself Gibson Security published details on Christmas Eve of the web requests you’d need to send in order to extract phone numbers in bulk from Snapchat’s servers.
Rather than simply fixing the problem quietly and quickly in the background – as one imagines a company like Google or Facebook would have done – and then apologising, Snapchat took the curious approach of officially declaring this process of mining phone numbers to be “theoretical.”
As The Register’s John Leyden wryly remarked, throwing terms and conditions at a technical problem, and the word “theoretical” at a vulnerability announcement, is the proverbial red rag to a bull.
And so it was that on New Year’s Day we found ourselves announcing that someone had “theoretically” recovered 4,600,000 usernames and phone numbers from Snapchat and published the whole lot online. (The last two digits of each phone number were removed in a sop to decency.)
With the ball back in Snapchat’s court, we honestly expected that Snapchat would:
- Apologise.
- Fix the problem.
- Convince us all that the fix really did work this time.
After all, part of the reason Snapchat wanted us to treat the risk as merely “theoretical” was that the company claimed to have fixed the problem already, saying over the holiday break that:
Over the past year we’ve implemented various safeguards to make [bulk phone number recovery] more difficult to do. We recently added additional counter-measures and continue to make improvements to combat spam and abuse.
Well, Snapchat has now officially responded to the breach, and this time it has:
- Praised itself.
- Offered no apology at all.
- Said it really is fixing things now, honest.
Indeed, it seems that on the issues of privacy and trust, things could scarely be better, with the company stating that:
The Snapchat community is a place where friends feel comfortable expressing themselves and we’re dedicated to preventing abuse.
That’s because:
We’re also improving rate limiting and other restrictions to address future attempts to abuse our service.
Apparently, Snapchat founders Evan Spiegel and Bobby Murphy – two Stanford guys who love building cool things, as their own website proclaims – aren’t quite as good at actually building things that work safely and reliably.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/3aHymfpZTHc/

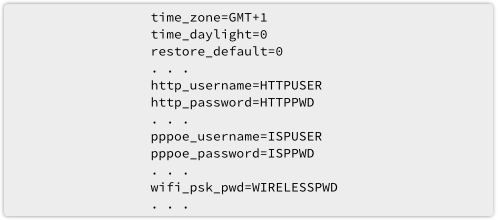
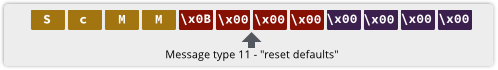
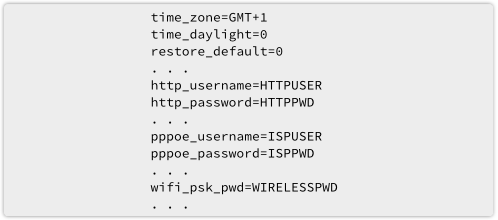
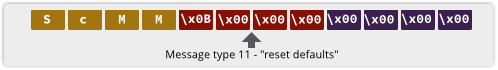
 For many home users, the router-slash-firewall at the edge of their network plays an vital security role.
For many home users, the router-slash-firewall at the edge of their network plays an vital security role. 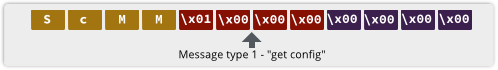
 Do you think Facebook is trustworthy?
Do you think Facebook is trustworthy?