Attack dismissed as "theoretical" by Snapchat used to plunder 4.6 million phone numbers
 Controversial photosharing site Snapchat is back in the news again, opening the New Year as the victim of a data breach that it really ought to have predicted, and probably should have headed off at the pass.
Controversial photosharing site Snapchat is back in the news again, opening the New Year as the victim of a data breach that it really ought to have predicted, and probably should have headed off at the pass.
Here’s the story so far.
Last week, we wrote about a vulnerability reported in Snapchat’s find_friends interface.
That’s a feature that is supposed to let you locate your friends on Snapchat, assuming you know their name and phone number.
Services of that sort are always moderately risky from a privacy point of view, because when they succeed (e.g. when you find that the user John Smith does indeed match up with 555-555-5555) they effectively verify an individual’s phone number.
However, the risk is usually managed by some sort of rate limit, restricting how many lookups you can do each minute, or hour, or day, so that you have to have some idea of John Smith’s phone number to start with.
Remove the rate limit, of course, and you could simply try to match John Smith against every number with a particular prefix – starting, say, at 555-555-0000 and carrying on until you reach 555-555-9999 or hit the jackpot.
According to the hackers who published last week’s vulnerability, Snapchat had left off the rate limit, making it feasible to try every number from 555-555-0000 to 555-555-9999 in about two minutes from a single computer with a decent internet connection.
→ Bring a modestly-sized botnet into the equation – 1000 infected PCs on home-user ADSL lines, for instance – and you could almost certainly churn through a whole North American area code (e.g. 604-xxx-xxxx, the code for Vancouver and the surrounding parts of British Columbia) in well under an hour.
Snapchat’s response to the find_friends vulnerability report was lukewarm:
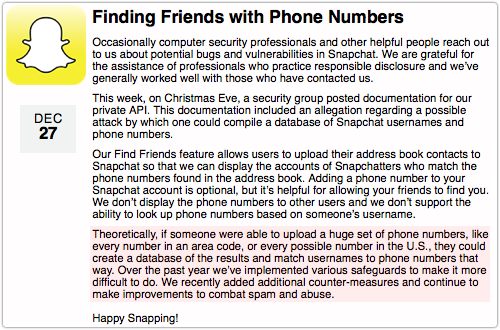
Theoretically, if someone were able to upload a huge set of phone numbers, like every number in an area code, or every possible number in the U.S., they could create a database of the results and match usernames to phone numbers that way. Over the past year we’ve implemented various safeguards to make it more difficult to do. We recently added additional counter-measures and continue to make improvements to combat spam and abuse.
The paragraph above doesn’t dismiss the problem entirely, which is a good thing, but the word “theoretically” certainly came back to haunt Snapchat.
Apparently, unknown hackers took matters from the theoretical to the practical by extracting a database of about 4,600,000 Snapchat usernames and phone numbers, and dumping the list online.
In a small concession to decency, the hackers thoughtfully chopped off the last two digits of every phone number, which took some of the edge off the breach.
But they openly offered to disclose those chopped-off digits, provided that you asked nicely:
This information was acquired through the recently patched Snapchat exploit and is being shared with the public to raise awareness on the issue. The company was too reluctant at patching the exploit until they knew it was too late and companies that we trust with our information should be more careful when dealing with it.For now, we have censored the last two digits of the phone numbers in order to minimize spam and abuse. Feel free to contact us to ask for the uncensored database. Under certain circumstances, we may agree to release it.
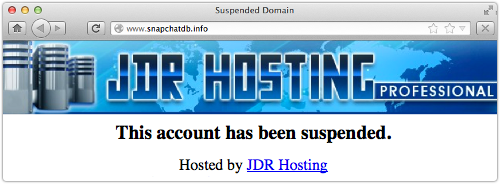
The dumped data was published on a server at snapchatdb.info, though that domain has now been taken off the air, producing an “account suspended” message from the hosting provider if you try to go there.
Snapchat has never been much of a darling to computer security practitioners, not least because its business was loosely founded on the bogus promise of “safe sexting.”
The idea was that you could send sexy photos of yourself to other people; they could view the pics for a few seconds (ooooh!) but then that would be that: the images would simply disappear, never to be seen again (aaaah).
Risque without risk was the basic idea.
Except that if you took a photo of your phone while the risky image was on screen, or took a screenshot, or dumped your phone’s graphics RAM, or used basic forensic data recovery techniques to retrieve the “deleted” files after viewing them, or fetched the image through a session-logging web proxy…
…then you’d quickly have realised that Snapchat’s promises of “disappearing images” were fanciful.
It certainly looks as though Snapchat’s protection of its users’ phone numbers has been a bit fanciful, too.
We’d be willing to bet that there are some coders at Snapchat working flat out on API (application programming interface) rate limiting, even as you read this article!
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/RrjJ-sDFtDU/
 Earlier this year Twitter rolled out an improved two-factor solution seemingly in response to previous attacks by the SEA.
Earlier this year Twitter rolled out an improved two-factor solution seemingly in response to previous attacks by the SEA.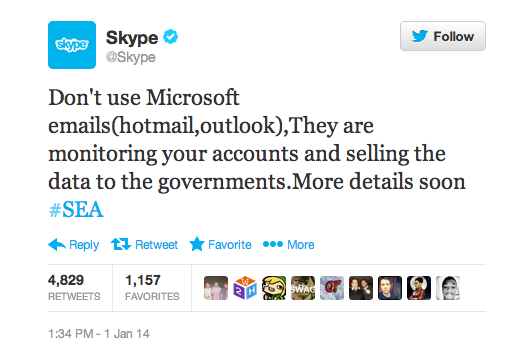
 Controversial photosharing site Snapchat is back in the news again, opening the New Year as the victim of a data breach that it really ought to have predicted, and probably should have headed off at the pass.
Controversial photosharing site Snapchat is back in the news again, opening the New Year as the victim of a data breach that it really ought to have predicted, and probably should have headed off at the pass.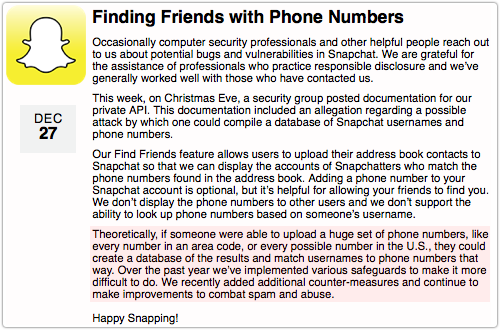
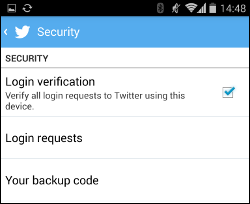 Earlier this year Twitter rolled out an improved two-factor solution seemingly in response to previous attacks by the SEA.
Earlier this year Twitter rolled out an improved two-factor solution seemingly in response to previous attacks by the SEA. You’re no doubt familiar with Pluto, the planet that got relegated.
You’re no doubt familiar with Pluto, the planet that got relegated.

 According to Michaud and Lackey, there’s an excellent product on the market that can be deployed for just this purpose.
According to Michaud and Lackey, there’s an excellent product on the market that can be deployed for just this purpose.