Bizarre Tolkien-inspired GCHQ Xmas card CAN’T BE READ by us PLEBS
The business case for a multi-tenant, cloud-based Recovery-as-a-Service solution
I have just received from the Dark Web, a samizdat copy of GCHQ’s Xmas card complete with cartoon from Chris Slane. The references (see below) provide a download of the complete Xmas card, which presumably can be printed out on cardboard in hard copy.
I think we can assume that the card is genuine as it contains the exemption notice from the FOIA regime which I came across when I sought access to an unrestricted document (“HMG IA Standard No.6: Protecting Personal Data and Managing Information Risk”).
The exemption under FOIA means that although the Xmas Card is information originated from GCHQ, posted insecurely in the ordinary post, and is clearly marked “unrestricted”, the tax payer who pays for the Card cannot get a copy under FOIA (just like the HMG No 6 standard).
The card also contains a poem which is a parody of the poem which describes all 20 Rings of Power, as found in Tolkien’s book (the Lord of the Rings). The Poem goes as follows:
The Terror Bytes of Power
Two terabytes per day to retain all Google searches
Five keeps the content from surveillance perches
Seven for Skype when one speaks to mates
Twelve stores the traffic which flows to the States
And in the darkness where the watchers are
Few laws to obey; nor rules that bar
And for privacy let the protection die
In a secret state where the shadows lie.
In the meantime, the Advocate General (the leading legal advisor to the European Court of Justice) has asked for the European legislature to re-draft the Data Retention Directive, which calls for the retention of metadata of all electronic communications to be retained for two years, as being in breach of Article 8 of the ECHR (right to a private and family life). This, of course, has been known to most of us for ages.
However, I want you to think about the Snowden revelations and then look at what the Advocate General points out, in this regard. He says that the use of telecoms data in accordance with the Data Protection Retention Directive:
- “may make it possible to create a both faithful and exhaustive map of a large portion of a person’s conduct strictly forming part of his private life, or even a complete and accurate picture of his private identity.”
- “There is, moreover, an increased risk that the retained data might be used for unlawful purposes which are potentially detrimental to privacy or, more broadly, fraudulent or even malicious”.
- “Indeed, the data are not retained by the public authorities, or even under their direct control, but by the providers of electronic communications services themselves. Nor does the Directive provide that the data must be retained in the territory of a Member State. They can therefore be accumulated at indeterminate locations in cyberspace”.
The European Union legislature:
- “should, in particular, have provided a more precise description than ‘serious crime’ as an indication of the criminal activities which are capable of justifying access of the competent national authorities to the data collected and retained”.
- “should have guided the Member States’ regulation of authorisation to access the data collected and retained, by limiting access, if not solely to judicial authorities, at least to independent authorities, or, failing that, by making any request for access subject to review by the judicial authorities or independent authorities and it should have required a case-by-case examination of requests for access in order to limit the data provided to what is strictly necessary”.
- “could have been expected to lay down the principle that Member States may provide for exceptions preventing access to retained data in certain exceptional circumstances or may prescribe more stringent requirements for access in situations in which access may infringe fundamental rights guaranteed by the Charter, as in the context of the right to medical confidentiality”.
- “should have established the principle that the authorities authorised to access the data are required, first, to erase them once their usefulness has been exhausted and, second, to notify the persons concerned of that access, at least retrospectively, after the elimination of any risk that such notification might undermine the effectiveness of the measures justifying the use of those data”.
The Advocate General has not found, “in the various views submitted to the Court of Justice defending the proportionality of the data retention period, any sufficient justification for not limiting the data retention period to be established by the Member States to less than one year” (AG emphasis).
So it looks as if the year is ending on a powerful note for those who think that privacy needs an uplift in data protection; one hopes the powers that be are listening and effective changes to the protection afforded when we use the Internet will appear in the New Year.
On that optimistic note, I say have a happy holiday and recharge your batteries for what should be an eventful year. We do live in “interesting times”.
References
My run-in on S.23 for FOIA (information originating from GCHQ)
The GCHQ Xmas Card can be downloaded from the Amberhawk Training website here (PDF).
Advocate General Press Statement here
This story originally appeared at HAWKTALK, the blog of Amberhawk Training Ltd.
Quick guide to disaster recovery in the cloud
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/12/20/bizarre_gchq_xmas_card_poem_hawktalk/
 One of the first computers I was ever allowed to use all on my own was a superannuated
One of the first computers I was ever allowed to use all on my own was a superannuated 
![Click on the image to read the original paper [PDF]...it's well worth it! Click on the image to read the original paper [PDF]...it's well worth it!](https://stewilliams.com/wp-content/plugins/rss-poster/cache/d4300_gpg-loops-500.png)
![Click on the image to read the original paper [PDF]...it's well worth it! Click on the image to read the original paper [PDF]...it's well worth it!](https://stewilliams.com/wp-content/plugins/rss-poster/cache/d4300_gpg-differents-500.png)
![Click on the image to read the original paper [PDF]...it's well worth it! Click on the image to read the original paper [PDF]...it's well worth it!](https://stewilliams.com/wp-content/plugins/rss-poster/cache/d4300_gpg-decoy-spikes-500.png)
 The White House on Wednesday released a 303-page
The White House on Wednesday released a 303-page 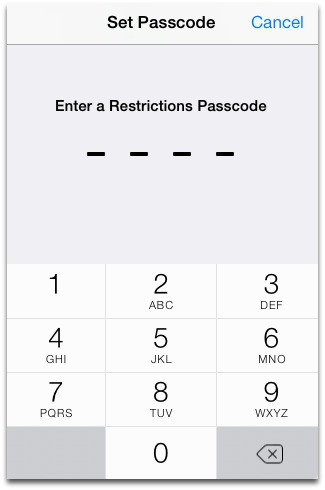
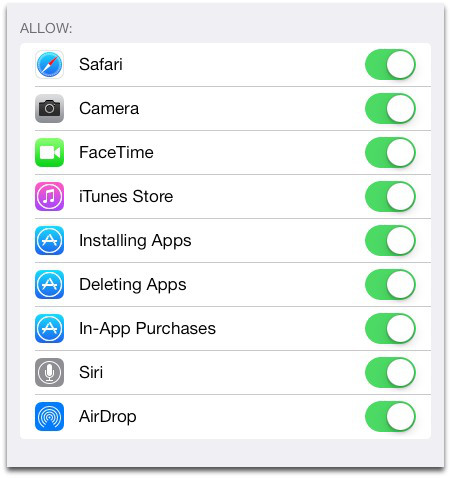
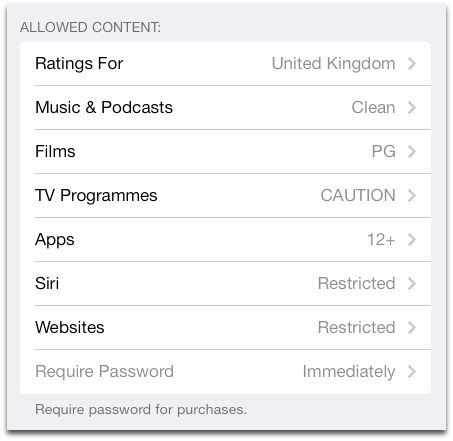
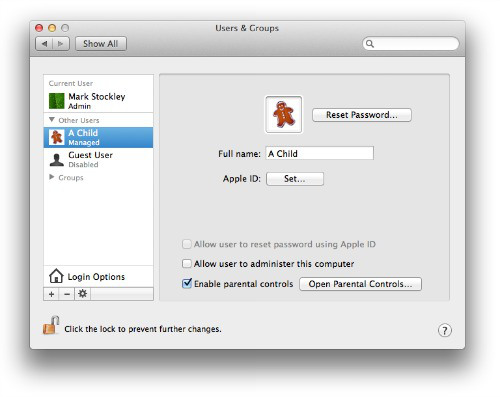
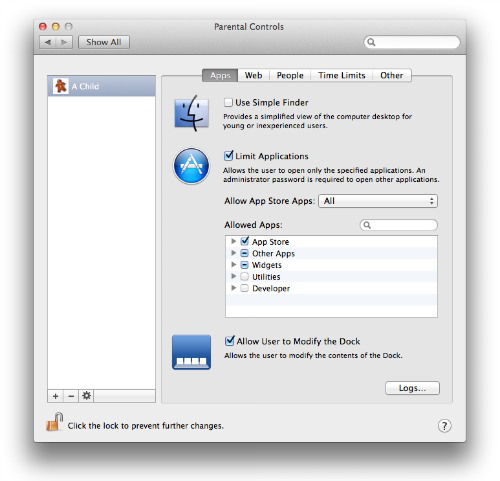
 Parents using Windows 8 can switch on Family Safety, which is a great improvement over the controls offered by
Parents using Windows 8 can switch on Family Safety, which is a great improvement over the controls offered by 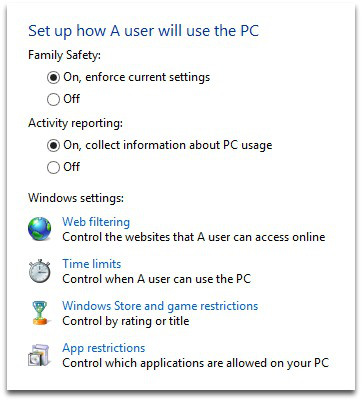

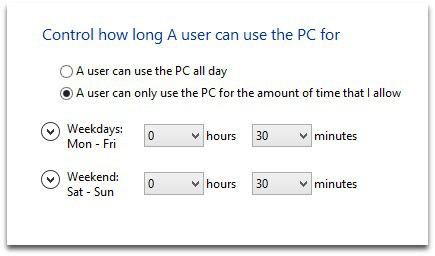
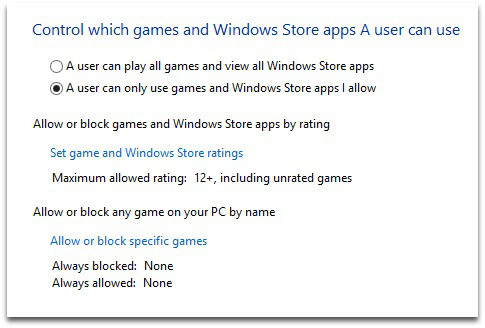
 Unfortunately, the parental controls that come with Windows 7 are fairly basic, but it’s still worth
Unfortunately, the parental controls that come with Windows 7 are fairly basic, but it’s still worth 

 When I was a young lad my parents always used to worry when I went out with my friends. “Don’t talk to strangers,” they would say, before adding, “don’t accept a lift from anyone you don’t know.”
When I was a young lad my parents always used to worry when I went out with my friends. “Don’t talk to strangers,” they would say, before adding, “don’t accept a lift from anyone you don’t know.”