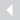Alan Turing chosen for the UK’s new £50 note – a cracking result!
In 2021, the UK’s highest-denomination banknote – or, more precisely, the biggest note in general circulation – will go plastic.
New banknotes typically mean new portraits, as when a plastic Sir Winston Churchill supplanted a paper Elizabeth Fry on the fiver in 2016, and the author Jane Austen replaced the scientist Charles Darwin on the tenner in 2017.
Like the £10, the £20 will transfer its allegiance from the sciences to the arts in 2020, with economist Adam Smith booted in favour of artist JMW Turner, after whom the prestigious Turner Prize is named.
(To be clear, there are at least two portraits on each banknote, because the reigning monarch is by tradition always on the front – it’s the people on the back who get swapped out when new notes are commissioned.)
So here’s a question for you – and don’t cheat by looking up the answer online or by peeking in your wallet…
…who’s depicted on the current £50 note, and what are they known for?
Chances are you don’t know.
Most people, at least in the UK itself, have no idea who’s commemorated on the fifty, for three main reasons: we don’t use cash that much any more; we’ve never taken much notice of the back of banknotes- everyone knows Her Majesty is on the front but the famous person on the other side is usually forgotten; and £50s are surprisingly rare in daily life anyway.
Somehow, we’re afraid of fifties, presumably on the assumption that counterfeiters favour the biggest notes because they offer the biggest return on, ahem, investment.
In fact, you regularly see signs in shop windows, especially in tourist towns, saying, “Sorry, no £50 notes accepted.” (Yes, they are allowed to do that – you can’t force a shopkeeper to take your money, just as they can’t stop you spending it somewhere friendlier instead.)
The answer is: the £50 currently has a double-bill of engineers-stroke-entrepreneurs on the back, namely Matthew Boulton and James Watt.
Boulton and Watt were business parters who helped fire up the industrial revolution in Britain and elsehere by selling and licensing their steam engines around the world.
And when the new note comes out it will stick with STEM (that’s contemporary shorthand for science, technology, engineering and mathematics) because Alan Turing has been picked as the new face of the £50.
Our hero
We’ve written about Alan Turing many times on Naked Security – he’s quite a hero of ours for lots of good reasons that anyone interested in computer science will know.
He’s probably best remembered for his codebreaking work at Bletchley Park during World War 2, where Turing and many other brilliant minds worked in dreadful conditions so that the Allies could crack the Nazis’ encrypted messages and thereby acquire a critical operational advantage in the fight to depose Hitler and his abominable regime.
Bletchley was cramped, crowded, leaky, insanitary – and, for the women who ran the first-ever electronic digital computers that were installed there towards the end of the war, downright dangerous.
Apparently, the operators were instructed to wear Wellington boots on duty so that they wouldn’t be electrocuted as they tended to the Colossus computers while splashing about in standing water that had got in through the roof.
Physical and intellectual endurance
Turing’s physical and intellectual endurance during the war was astonishing – he carried on making cryptanalytical breakthroughs in the midst of such shortages of everything, including food and sleep and time, that most of us would simply have run out of steam and achieved nothing.
But in our view, the most amazing indication of his brilliance, both practical and theoretical, was his pre-war work in which he figured out various vital limits to “what digital computers can do“…
… before digital computers even existed.
Turing was gay in an era when that was proscribed by law in Britain.
This ultimately led to his prosecution and conviction in court, to his formal ostracism by the Establishment – who had, of course, conveniently ignored the law when his wartime contribution was so desperately needed – and, tragically, to his ultimate suicide.
In a way, therefore, it almost seems inappropriate to commemorate Turing now on the very Bank of England note that many people shun for reasons they can’t really explain, based on fears of being ripped off that they can’t really justify.
On the other hand, the £50 is the biggest English banknote in circulation, in both size and value, so perhaps it is a fitting tribute for Turing after all – one that will remind us of the huge value of mathematicians and scientists who can blend theory and practice in ways that advance the world as a whole.
As the Bank of England’s website proclaims, “Think science and celebrate Alan Turing.”
IN CASE YOU WERE WONDERING…
YOU MIGHT ALSO LIKE…
Featured image of Turing cropped from Bank of England 50-pound-note-nominations web page.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/JlDopIyx8sQ/