Researcher offers quick fix for Samsung remote wipe vuln
Although Samsung has yet to issue patches for most of the phones affected by a recently discovered remote-wipe vulnerability, a German security researcher has released an app that he says can block the exploit.
As El Reg reported on Tuesday, a flaw in Samsung’s dialing software causes its phones to execute some tel protocol URIs (universal resource identifiers) without the user even pressing the Dial button. At worst, this allows a remote attacker to send the Unstructured Supplementary Service Data (USSD) code that resets the phone to its factory state, wiping all the data in the process.
On Wednesday, Samsung issued a firmware fix that resolved the issue in the Galaxy S III, its flagship Android handset. But no other phones have yet received a similar patch, and it’s not clear just how many mobiles may be affected.
For those whose phones may still be vulnerable, security researcher Collin Mulliner has issued an app that he says slaps a quick fix over the problem. Called TelStop, it works by publishing a URI handler for the tel protocol. The result is that whenever a tel URI is activated, the Android OS asks the users whether to open it using the phone app or TelStop.
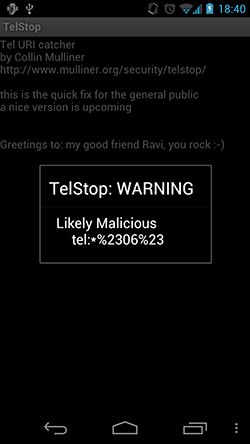
Block that call!
“If you suddenly see the application selector that includes Phone and TelStop you know something just invoked a TEL URI,” Mulliner explains on his website. “If you didn’t click a TEL link or tried to dial a number it is likely to be an attack.”
TelStop also attempts to interpret the contents of tel URIs to offer the user some guidance as to whether they might be malicious. Links that just contain digits are probably legitimate phone numbers, but ones that contain special characters such as asterisks or per cent signs trigger an additional warning.
On his Twitter feed, Mulliner describes the current version of TelStop as a “quick and dirty fix,” and says a more user-friendly version is in the works (although the current version does block the exploit).
Owners of Samsung phones can download the latest version of TelStop either directly from Mulliner’s website or from the Google Play store. Mulliner recommends the latter method, since users who install it from Google Play will be automatically notified of future updates. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2012/09/26/samsung_remote_wipe_app_fix/