Bromium, the security startup launched a year ago by the techies behind the open source Xen server virtualization hypervisor, are lifting the veil a bit on the software that they are cooking up, while at the same time announcing a big new bag of cash to pay for the ongoing development of what the company is calling a microvisor.
Ian Pratt and Simon Crosby, colleagues from Cambridge University who created (and somewhat begrudgingly commercialized) the Xen hypervisor, which Citrix Systems bought in September 2007 for $500m, are behind the stealthy startup. They tapped Gaurav Banga, who was previously CTO and senior vice president of engineering at computer BIOS maker Phoenix Technologies, to be their CEO.
Banga knows a thing or two about virtualization, having created the Unified Extensible Firmware Interface (UEFI) for modern system BIOSes and also HyperSpace, a baby Linux environment that Hewlett-Packard acquired for its PCs in June 2010.
Bromium came out of stealth mode last June, and at the time Crosby and Pratt didn’t say much about what they were up to, except that they would be using virtualization in some manner to secure PCs and servers in a different way and that they had secured $9.2m in Series A funding from Andreessen Horowitz, Ignition Partners, and Lightspeed Venture Partners.
The original plan was to have some sort of products in the field by the end of 2011, but that didn’t work out, and Crosby was absolutely unapologetic about it when talking to El Reg, considering the monumental complex job of securing a PC from the outside world. Bromium’s investors don’t seem to mind that this might take a little time, and Highland Capital Partners is leading a $26.5m Series B round, with Intel Capital participating for the first time and Andreessen Horowitz and Ignition Partners kicking in some more dough, too.
The bar that Bromium has set for itself, as it turns out, is quite high, and hence the patience. Which is also reasonable given the daunting task that the company has: creating a completely new security paradigm for PCs without adding a new management console and without changing the user experience at all.
“You have to trust something, so we will start with the hardware,” says Crosby, who walked El Reg through the basic architecture of the Bromium security model and its microvisor approach.
The hardware is analogous to the emperor in what is known as the Byzantine general’s problem, which is how can you know who to trust in the army when you want to attack a city? Your army (by analogy a PC operating system and application stack) could be infiltrated with traitors (malware) who want to delay or thwart your plans, and if you are such a general (the operating system kernel in charge) you have to assume there are such traitors and still carry out your orders from the emperor – and without revealing your plans in full to anyone in the army.
The problem with a PC software stack is exactly the same as with a Roman army: there’s so much stuff to keep track of. In the case of a PC, there are approximately 100 million lines of code in the software stack, and by definition, that means there are always vulnerabilities and that you can never plug them all. That’s a big problem, and ironically, Bromium’s answer is this: Don’t try.
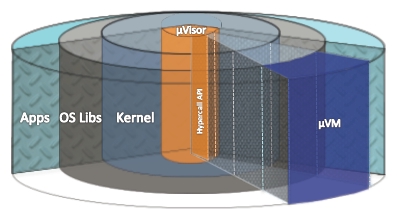
The Bromium microvisor: task-based virtualization
Rather, Bromium is creating a security methodology that invokes the principle of least privileges, which isolates all applications and operating system functions on a PC from each other and that never, ever lets a process see something that it doesn’t need to see.
For instance, when you load Facebook, what the instance of the Chrome browser can see of your disk drive is precisely one file: the cookie that Facebook installs, and not one bit or byte more. That cookie and the Facebook session are loaded up into a virtual container called a microVM, which is different from a hypervisor guest in that it is centered on a specific task, not on abstracting a whole virtual PC environment that an OS can run in.
Here’s another example: when you load an Excel spreadsheet, the only thing that Excel is allowed to see is that spreadsheet, and because a microVM security layer is wrapped around it, it simply is not allowed to reach into the TCP/IP stack and start sending packets out to heaven knows where on the internet. No program is allowed to start a session on your webcam if it has not been granted explicit permission to do so, and so on.
The Bromium microvisor is not a heavy-weight virtualization layer, but a lightweight one that is twisting features that Intel has woven into its recent Core and Xeon processors, such as VT and in the case of business-class PCs, vPro extensions to the Core chips and related chipsets, in a new way to secure tasks running on PCs instead of helping hypervisors run better and more efficiently.
The similar AMD-V and IOMMU extensions to the Fusion and Opteron processors that are analogous to VT and VT-d are also supported with the Bromium microvisor, so a PC based on either chip will be able to protect against outside threats. But to get the full protection, which will be able to thwart attempts to hack a PC from the machine’s actual keyboard, you need the Trusted Execution Environment (TXT) features etched into the vPro-enabled Core processors as well as in the latest two generations of Xeon processors.
Since Bromium is aiming its initial products at enterprises, not consumers, and not focusing yet on servers, supporting vPro-enabled PCs is a good place to start, says Crosby. “Supporting AMD processors as well as Intel chips is not hard,” explains Crosby. “But the guys who are all wound up about PC security are all on vPro machines already.”
A Bromium microvisor on a Windows-based PC can create and destroy hundreds of these microVMs in a second as tasks are started and finished, and it has an infinitesimally small effect on performance.
Nothing is ever perfectly secure, of course, and Bromium is not proclaiming that its microvisor is immune from attack. The microvisor has 10,000 lines of code and its hypercall API, while hardened, is absolutely not impenetrable.
“We can reduce the vulnerability surface from 108 to 104, and that works out to a factor of 104 increase in costs for the bad guys,” says Crosby. “The goal is to make it too expensive for the bad guy to attack you in the first place.”

The interaction of the OS, apps, and the Bromium microvisor and microVM (click to enlarge)
Because the microvisor has tight control over what tasks on a machine can access data, and what data in particular, it is also a means of preventing the loss or corruption of data on a PC. So if you click on something you shouldn’t have on the Internet and a piece of malware gets in, the clever Byzantine general (our kernel) rather than confronting the malware, can wrap the tasks that make up that malware in a microVM and let it pretend to overwrite Windows files.
Yup, it lies to them and puts those corrupted Windows files in a microVM, but the malware can’t know that. And when the malware is done writing on your panes of glass with spray paint, the microvisor deletes the files and the malware in the microVM and thus its attempted corruption are purged from the system.
You’ll notice that this approach to security works whether Windows is patched or not. Let’s hope this doesn’t make Microsoft complacent about security.
Bromium now has 40 employees, and Crosby says that they are doing “some very, very deep systems work.” The company is not talking products yet, but clearly the idea is to get PC OEMs on board with adding Bromium wares to the machines. “We’re in beta now, and we will GA when it is awesome,” says Crosby.
You can find out more about the Bromium architecture in this white paper (PDF). ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2012/06/20/bromium_microvisor_security/