Roundup Here’s a quick roundup of recent infosec news beyond what we’ve already reported.
Black Hat USA cans planned keynote speaker following outcry
This year’s Black Hat USA has axed keynote speaker US House rep Will Hurd (R-TX) after outcry over his politics and voting record.
Attendees and presenters threatened to boycott the annual security conference due to the congressman’s support for anti-abortion laws, efforts to defund Planned Parenthood, and unwillingness to back women in STEM, TechCrunch first reported.
Given the much-needed push for more diversity and inclusion in the worlds of technology and information security, Hurd’s invitation to speak at the event irked parts of the cyber-community. He is, for what it’s worth, said to be one of the more tech-aware congresscritters in America.
After 24 hours or less of pressure, Black Hat’s organizers said in a statement to The Register on Friday that Hurd will not be lecturing security nerds in Vegas this year as planned:
Black Hat has chosen to remove U.S. Representative, Will Hurd, as our 2019 Black Hat USA Keynote. We misjudged the separation of technology and politics. We will continue to focus on technology and research, however we recognize that Black Hat USA is not the appropriate platform for the polarizing political debate resulting from our choice of speaker. We are still fully dedicated to providing an inclusive environment and apologize that this decision did not reflect that sentiment.
Meanwhile, Hurd’s office responded:
And because this is the internet and it is 2019, we also have outcry over the outcry, which is generating backlash against the backlash…
Hey, so, who’s up for DEF CON, then?
Radiohead hackers beat band to post recordings
Fans of mopey British rock outfit Radiohead were given a treat this week when the band unexpectedly put online a collection of studio recordings to purchase and download – audio that, apparently, had been earlier stolen by hackers who threatened to publicly leak the files unless a ransom was paid. In response, the band released the recordings themselves via Bandcamp rather than pay out the six-figure demand.
That online release only came after the bad guys had already given up on receiving the dosh and had dropped the collection on the dark web. Researchers at Israeli cybersec outfit Sixgill claim they spotted the recordings linked from a Pastebin post that went up a full two days before the band decided to emit the songs officially, and they provided this screenshot to The Register to prove it:
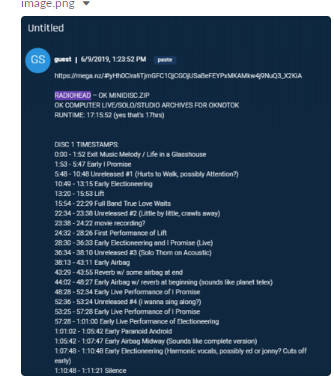
That doesn’t mean you should rifle through the dark web for the files, and ignore Radiohead’s official channel to get the tunes, however. Aside from being the right thing to do, each sale helps benefit climate change charity Extinction Rebellion.
Emuparadise loses million-plus user accounts to forum hack
Vintage gaming site Emuparadise is the latest website to see its user account details fall into the hands of hackers. A collection of more than a million accounts was reported to be on offer in crimeware forums and were added to tracking service HaveIBeenPwned.com. The hackers were said to targeted the emulation site’s user forums and made off with names, salted and hashed passwords, IP addresses, and email addresses.
Not a major breach, but if you have an Emuparadise account you should make sure your password is not being re-used on other sites.
Cisco posts patch for CSRF bug
Admins of Cisco IOS XE gear will want to spend a few extra minutes today checking for any applicable patches after Switchzilla issued a warning for a cross-site request forgery bug.
The vulnerability is only found in the web interface of IOS XE, but if exploited it could allow an attacker to perform arbitrary commands with the current user’s clearance level. Other versions of IOS and those that do not have the web interface enabled should be safe.
Evite incite user fright
Invitations service Evite has had to put up an alert after discovering an attacker had made off with a data backup file that had been archived all the way back in 2013.
While the archive is six years old, the information in it is rather sensitive. The hackers were able to get names, usernames, email addresses, passwords, and in some cases the user’s date of birth, phone number, and mailing address.
The company said it is in the process of notifying users, but everyone who was on the site back in 2013 would be well advised to change their password just to be safe.
Watchdog barks at MI5 for careless data handling
Britain’s iconic MI5 spy agency took heat this week after Blighty’s Investigatory Powers Commissioner found problems with the snoops’ handling of people’s data.
The watchdog said MI5 was not doing enough to secure the personal information it gathered and stored en masse under the power of warrants. In addition to not properly securing that sensitive data, it is said MI5 also held on to the info for far longer than is legally allowed.
Exim patches server flaw
Last week we warned of the command-execution flaw that had been disclosed for the Exim email server software. While admins could have patched the bug weeks ago by updating to the latest version, this week a patch was issued for earlier builds as well.
Those running Exim versions 4.87 through 4.91 will want to check out this announcement and make sure they have the fix in place, as working exploits for the flaw have recently been spotted being used in the wild to compromise vulnerable systems.
Report outs UK human rights champion as spyware house owner
British gallery owner and human rights campaigner Lana Peel has been accused of having ties to a notorious spyware developer.
The Guardian says that Peel, CEO of Serpentine Galleries, also has an ownership stake in NSO Group. That biz develops notorious surveillanceware Pegasus, which is sold to governments around the world to slip into targets’ devices so they can be snooped upon. NSO, which is majority owned by investment biz Novalpina Capital, claims it doesn’t flog its software to bad people, though human rights campaigners aren’t so sure.
“The Peel family has an investment in Novalpina. I have no involvement in the operations or decisions of Novalpina, which is managed by my husband, Stephen Peel, and his partners,” Lana Peel said in a statement.
In brief…
Meanwhile, Citizen Labs and its pals in academia have produced a report [PDF] on stalkerware and its effects.
AVG antivirus and Firefox clashed this week, resulting in people’s saved passwords disappearing due to a certificate update. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2019/06/15/security_roundup/