The US Cybersecurity and Infrastructure Security Agency (CISA) has become the latest government body to plead with admins to implement security best practices on Microsoft’s Office 365 platform.
The UK’s National Cyber Security Centre (NCSC) made a similar appeal in December 2018. The evidence, though, is that most users are not taking their tablets.
How many, for example, enable multi-factor authentication (MFA) on Office 365? MFA is where not only a password is required, but also a second factor, such as a text message sent to a mobile phone (frowned upon as vulnerable to interception) or a code from an authenticator app. MFA is top of the list when it comes to basic security advice for Office 365.
Exact figures are hard to come by, but it turns out that Microsoft publishes information about the security practices of its users, via a security dashboard available to Office 365 administrators.
The maximum “security score” is currently 707, though this should not be taken too seriously since it assumes use of other Microsoft services like InTune. The average Office 365 score is just 37, though, and that is a concern.
Looking at the Secure Score table, you would get 100 points simply by enabling all the MFA options. In fact, even by flinging a document or two into OneDrive, Microsoft will reward you with 10 points. You also get 10 points for non-expiring passwords, a reversal of former advice. Conclusion: the typical Office 365 account is miles behind in terms of security best practice.
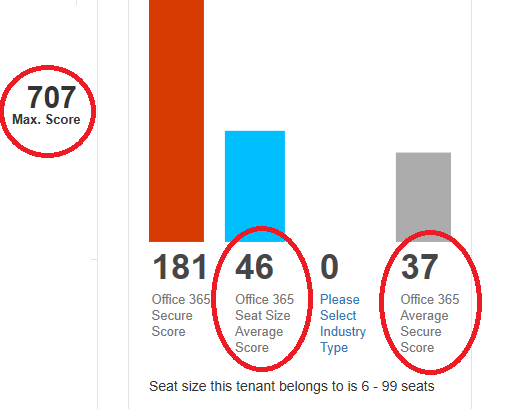
Typical Office 365 security settings are very low
This global average is no doubt pulled down by millions of tiny accounts and will improve as seat count increases. For a seat count of six to 99 the average increases to a massive… 46. It is fair to say that there is a great deal of nothing being done about adopting the vast array of security options on offer.
Last month, CollabTalk published a survey commissioned by Microsoft and four other groups on the subject of security and compliance practices in Office 365. Those surveyed were IT professionals, C-level executives and compliance officers globally. It also references an earlier 2017 survey of consultants and small businesses.
According to this earlier survey:
Most of the comments pointed to general confusion around cybersecurity with Office 365 products. In other words, they did not know what was available through the platform, whether these features were all (or in part) in use, or whether the features provided exceeded, met, or missed their industry and organizational requirements.
Amusingly, though:
100 per cent of respondents who had experienced a security breach did not think Microsoft security was sufficient, regardless of the cause of the breach.
The report concluded that “the overall governance of your Office 365 environment has less to do with the technology and more to do with the practices and procedures you put in place.”
While true up to a point, the complexity of what is on offer and the fact that most people accept the defaults is part of the problem. These defaults are also constantly changing, and some valuable features, like mailbox auditing, are enabled by default for new customers but not turned out automatically for existing ones.
Cost is another problem. Want Office 365 Advanced Threat Protection (ATP), for example? This service checks email attachments and links for malware, blocks malicious files in SharePoint online, and attempts to detect phishing attacks. ATP comes with the high-end E5, Education A5 or Microsoft 365 Business plans. Otherwise, it is $2.00 (£1.51) per user/month for Plan 1 or $5.00 (£3.80) for Plan 2, which adds automated investigation and response.

Microsoft goes to great lengths to polish Azure Active Directory’s password policies
READ MORE
It is a similar story with Azure Active Directory (AAD), the identity system used by Office 365. The bundled version does include MFA, so no excuses. If you want additional features such as conditional access based on device state, for example, you will need Premium P1 at extra cost; or Premium P2 for additional identity protection. In other words, Office 365 security is a product as well as a feature, and the desire to upsell plans for profit limits the extent of the built-in security.
Another issue with MFA is that users worry about being locked out of their account if they lose their phone, for example, and find the process of signing up, configuring an authenticator app, and responding to additional security prompts complex and annoying.
These are small inconveniences compared to the potential impact of a security breach. Users can and do yield login information easily by clicking a link in a convincing email. MFA, you would think, is a no-brainer unless you are really confident that every phishing email will be caught by email filters; and such faith is misguided. Some of those malicious emails may come from genuine contacts who have themselves been hacked.
The best way to improve Office 365 security? Diligent admins, yes, but that will always leave a large group of less fortunate users. The most effective change would be to improve the defaults, though this also has complications especially with something intrusive like MFA.®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2019/05/16/why_office_365_security_is_woeful_despite_government_fingerwagging/
![]()