New scam accuses you of child abuse, offers to remove evidence
Here’s a new twist to sextortion, the cybercrime that gets its name because it melds sex with extortion.
Usually, the approach is to send you an email saying, “We infected your computer with malware, we snooped via your webcam, we monitored your browsing…
…and we recorded you on a porn site, so send us money or we’ll send the recording to your friends and family.”
To reinforce the claim to have remote control over your computer, the crooks often add some personalised content into the email they send you.
For example, the crooks may include a password from one of your accounts, list your phone number, or set the From: line in the email to make it look as though they sent the message directly from your own email account.
Don’t panic if you see “personal” data in one of these spams. The passwords and phone numbers almost certainly come from a data breach – in fact, you might recognise the password as an old one you had to change because the service provider got hacked. And the From: header in an email is essentially part of the mail message itself – the sender can set it to anything they like.)
But there’s a new sort of sextortion message going around, and instead of asking you to pay to have a video file deleted, it’s inviting you to pay to have a corrupt law enforcement official modify your docket so you don’t get charged with a serious criminal offence:
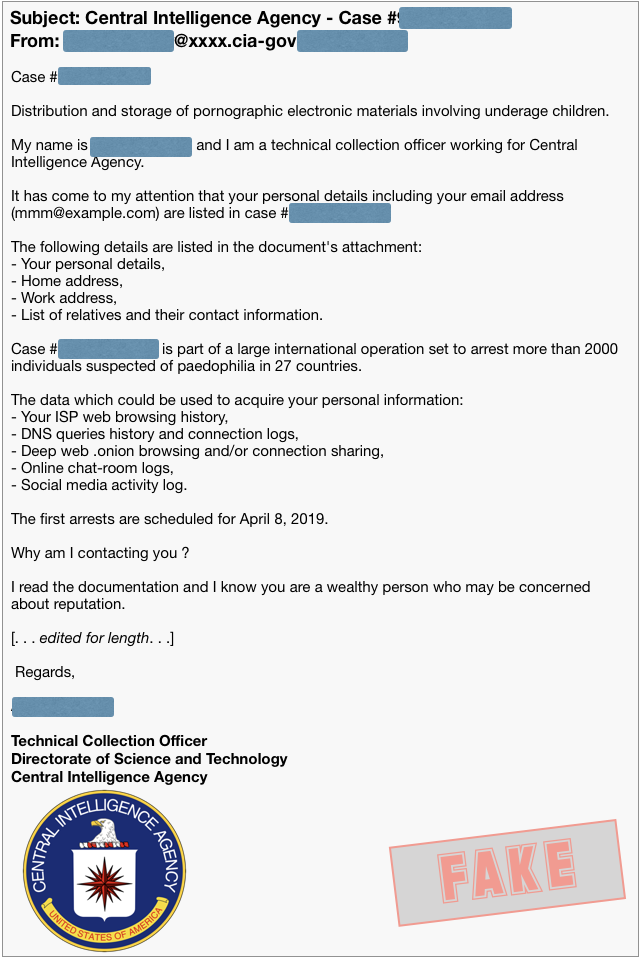
Having set the scene, the allegedly crooked CIA officer says:
I am one of several people who have access to those documents and I have enough security clearance to amend and remove your details from this case. Here is my proposition.
Transfer exactly $10,000 USD (ten thousand dollars – about 2.5 BTC) through Bitcoin network to this special bitcoin address:
3XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Upon confirming your transfer I will take care of all the files linked to you and you can rest assured no one will bother you.
Please do not contact me. I will contact you and confirm only when I see the valid transfer.
The case number, “agent’s” name and Bitcoin address change every time, but the rest remains the same: send money to buy your way out of a criminal case.
The good news, if you can call it “good”, is that in this instance the crooks are going too far to be believable – while a significant percentage of internet users do watch porn, fortunately only a tiny number are disseminators of child abuse material.
We’ve checked the Bitcoin addresses in a few samples of this scam and have found no evidence of anyone having paid up.
Nevertheless, it’s the thought that counts, and the way that the crooks are thinking here is both intimidating and disturbing – they’re not just insulting you but the CIA too, by presenting themselves as corrupt officials who will take a bribe to alter the course of an investigation.
As always: don’t engage, and don’t reply – not even if you think you have something cutting remarks you want to say to the crooks.
They’re crooks, after all, who are happy to make false accusations, to demean public officials, and to solicit bribes.
Delete the email, offensive though it is, and move on…
LEARN MORE: WATCH OUR VIDEO
(No video showing above? Watch on YouTube.)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/4Lk-PjfggFQ/