What do sexy selfies, search warrants, tax files have in common? They’ve all been found on resold USB sticks
About two-thirds of USB memory sticks bought secondhand in the US and UK have recoverable and sometimes sensitive data, and in one-fifth of the devices studied, the past owner could be identified.
These results come this week from a study conducted by the University of Hertfordshire in the UK and commissioned by Comparitech, a consumer product comparison website.
The researchers purchased 200 USB drives, 100 in the US and 100 in the UK between January and May 2018, from eBay, secondhand shops and conventional auctions. In the US, at least, most sellers demonstrated awareness of the need to erase data – only a single drive showed no sign of an erasure attempt. In the UK, 19 showed no sign of attempted cleansing.
Troublingly, the material recovered was often fairly sensitive. There were nude images of a middle-aged man, along with contact details. There were legal documents like a search warrant and risk assessments. There were financial papers dating back years, along with personal data. There were also tax forms, wage slips and the like.
From the data found, 20 former device owners in the US and 22 in the UK could be identified. The researchers, however, did not make an effort to contact those individuals to alert them to their poor data hygiene.
Sixty-four people in the US and 47 in the UK tried to delete their data, but didn’t actually manage it. Eight USB sticks in the US and 16 in the UK had been reformatted, but the data could be recovered “with minimal effort.”
About the same percentage of people managed to wipe their data successfully, presumably with a data erasing tool – 18 in the US and 16 in the UK.
There were also several drives that could not be read at all – six in the US and one in the UK – as well as one USB stick in the UK that could not be read because it was encrypted with BitLocker.
It’s not that people don’t know data should be deleted when disposing of drives. Rather they don’t know how to do so in a way that makes the data unrecoverable. People often believe that rituals like dragging files to the trash and selecting “Empty Trash” or one-pass reformatting of storage media actually erase files.
As anyone with even modest knowledge of IT security will tell you, that’s just not the case. Data deletion requires rather a bit of effort, which is why US standard bod NIST has more than 60 pages of guidance on the subject.
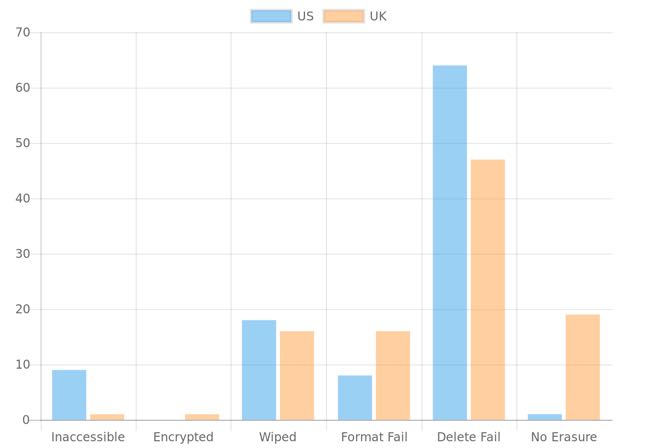
“This study would indicate that while in the US, some effort had been made to remove the data from the USB memory sticks in 99 per cent of the cases, in the UK this figure was only 81 per cent,” the study says. “This would indicate a higher level of awareness in the US to the potential issues.”
Despite this people in the US were no more likely to delete data successfully than those disposing of drives in the UK.
Computer makers could help matters by relabelling the “Empty Trash” menu to something more accurate like “Sweep Files Under the Rug” but computer users ultimately have to look after their own interests.
In an email to The Register, Paul Bischoff, editor of Comparitech, advised not cutting corners when erasing data. “If you’re throwing it out, destroy it with a hammer or drill first,” he said. “If you’re selling it, use secure erasure software or a full, low-level format – not a ‘quick’ format – to completely remove remnant data.” ®
Sponsored:
Becoming a Pragmatic Security Leader
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2019/03/14/usb_recoverable_data/



