Researchers Build Framework for Browser-Based Botnets
Researchers have created a new framework dubbed MarioNet that allows an attacker to control a victim’s browser and all of its resources.
Modern browsers have become more than simple windows into HTML documents; instead, they are “sophisticated browsing software that essentially behaves as an integrated operating system for web applications,” according to new research presented today at Network and Distributed Systems Security (NDSS) Symposium 2019.
The researchers – Panagiotis Papadopoulos, Panagiotis Ilia, Michalis Polychronakis, Evangelos P. Markatos, Sotiris Ioannidis, and Giorgos Vasiliadis – devised a framework for building persistent malicious networks on a browser-based foundation, which they detailed in their paper “Master of Web Puppets: Abusing Web Browsers for Persistent and Stealthy Computation.”
The power of malware that uses HTML5 and other browser-based software as an attack component stems from the fact that, by default, Web applications are understood to be trusted and can run client-side JavaScript code with no natural limitations.
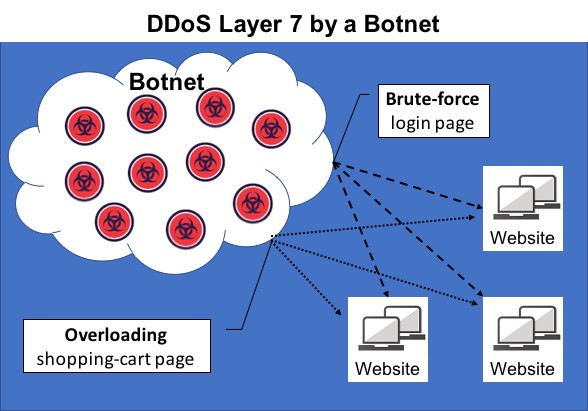
MarioNet is a three-step system involving components the researchers call the distributor, servant, and puppeteer. And it is these three components and the persistence they enable that make MarioNet something new.
The distributor is the infection piece, placing the rest of the package on the victim’s browser from a single visit to an infected website. The servant is the piece that becomes embedded in the victim’s browser, executing the malicious payload as directed by the puppeteer.
The puppeteer remains on the victim’s system, communicating with a C2 server, directing the execution of malicious code, and controlling the code’s use of computer resources in order to remain as elusive and evasive as possible.
“The immediate interest is persistence. The paper mentions that these infected sites, however they’re infected, they can have the infection piece removed [and] the attack persists,” says Mike Bittner, associate director of digital security and operations at The Media Trust. “That attack can take many forms, including DDoS traffic engines and cryptominers, credential skimmers, and banking remote-access Trojans.”
Unman Rahim, digital threat analyst at The Media Trust, says this new threat is critical because malicious hackers have been figuring out how to weaponize HTML5’s features.
“They’ve been using obfuscation/deobfuscation JavaScript to disguise malicious code. Now they can use service workers — scripts that offer rich online experiences, push notifications, and background syncs — to gain control of users’ browsers long after users have left the compromised site and to help attacks persist despite browser reboots,” Rahim says.
MarioNet is an evolution of the threat possible through HTML5. While there has been a growing trend of malware built on HTML5, Bittner says, “It’s a trend to make the browser an attack surface. The ability to communicate with a third party over the browser, though, is something you don’t see very often.”
The research raises another issue: academic computer researchers presenting details of an attack mechanism that had not previously been seen in the wild. “It’s a double-edged sword. It’s good because people like me have something to look out for and defend against, but it may be something that people didn’t know about before and can now take advantage of.”
“From a security professional aspect it’s something I wish we could share just among ourselves, but I think the good outweighs the bad,” he says.
Related Content:
- How to Create a Dream Team for the New Age of Cybersecurity
- 4 Payment Security Trends for 2019
- 8 Cybersecurity Myths Debunked
- Massive DDoS Attack Generates 500 Million Packets per Second
- New Attacks Target Recent PHP Framework Vulnerability
![]()
Join Dark Reading LIVE for two cybersecurity summits at Interop 2019. Learn from the industry’s most knowledgeable IT security experts. Check out the Interop agenda here.
Curtis Franklin Jr. is Senior Editor at Dark Reading. In this role he focuses on product and technology coverage for the publication. In addition he works on audio and video programming for Dark Reading and contributes to activities at Interop ITX, Black Hat, INsecurity, and … View Full Bio