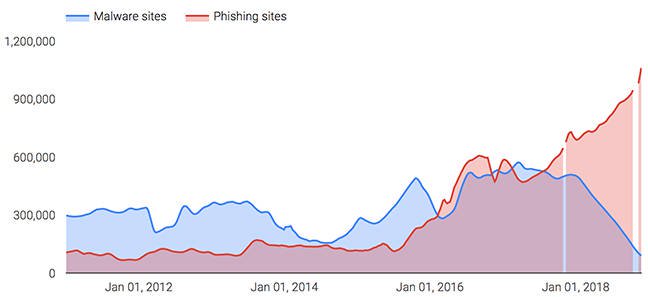
Setting the Table for Effective Cybersecurity: 20 Culinary Questions
I love to grill chicken. Aside from the fact that I enjoy the spicing, marinating, and grilling process, I also very much enjoy the results. Unfortunately, sometimes a little bit too much. But what does a chicken barbecue have in common with information security? Let me explain:
- Do you have the right ingredients? Even the best chefs will produce an inferior product if they begin with the wrong ingredients. In security, we need to make sure that we have the right data to meet our goals and mitigate the risk we’re most concerned about. With poor data, even the best security teams will struggle to produce results of any value.
- Are your ingredients fresh? Data must be right, but it also must be available when needed. A security team that can’t get to the data it needs when it needs it isn’t going to succeed in running security operations or investigating and responding to security incidents.
- Did you measure the ingredients properly? A security organization has access to an overwhelming amount of information. Unfortunately, some of that information adds no value to security operations and can have the opposite effect of reducing the effectiveness of the security team.
- Do the flavors complement each other and work together to improve taste? A security organization is made up of a number of different teams. Each team has a different function, and each team is important to the overall effectiveness of the security organization. If there are teams that aren’t adding value or that don’t work well with others, it brings everyone down.
- Do you have the right kitchen utensils? There are over 2,000 vendors in the security market. Some of them sell technology that will aid you in meeting your goals; others, less so. If a security organization doesn’t focus on acquiring the right technology to assist in meeting goals, it’s much harder for itself to achieve them.
- Are you spicing and marinating with the right technique? Even the best tools won’t do an organization any good if they aren’t leveraged properly. It isn’t enough just to install great technology. Technology needs to be configured in line with your operational needs and operated and maintained appropriately.
- Are you spicing and marinating for the right amount of time? All technology has a shelf life. As risk, threats, priorities, and business needs change, it would be naive to think that the same approaches and the same types of solutions will continue to fit the bill. Sometimes, an organization needs to take a step back and reassess.
- Is the grill at the right temperature? Even the best grill will ruin chicken if not set to the right temperature. Security operations needs to be set up to run efficiently and at the right pace. Otherwise, the organization runs the risk of getting bogged down in activities that don’t add value, or on the flip side, miss important events all together.
- Is the heat even? Setting the grill at the right temperature isn’t enough. The heat also needs to be distributed evenly. In security, there are many different activities that need to be given the appropriate attention. If attention shines disproportionately on one or a few activities, it takes away from other important activities.
- Are you grilling for the right amount of time? No matter how well you’ve prepared the chicken, if you grill it for too little or too much time, it will not come out well. Similarly, spending too little or too much time on analysis and investigation will lead an organization to jump to conclusions that can’t be substantiated or spend an inordinate amount of time poring over data that won’t lead to any tangible results.
- Did you dry out the chicken? There is such a thing as over-investigating an incident. If an incident can be analyzed, investigated, and resolved quickly, it should be.
- Did you choose side dishes that go well with the chicken? Security organizations exist first and foremost to mitigate and minimize the information security risk to the business. This involves working together with the business and cultivating cooperative relationships rather than operating in a vacuum or trying to force security on the organization against its will.
- Did you choose beverages that go well with the chicken? Business executives and the board need to make security a priority. Otherwise, without proper support, the security organization will be constantly be fighting an uphill battle it can’t win.
- Did you ruin your precious spicing and marinating work with sauces? A good security program should stand on its own. A weak one will need to be supplemented.
- Did you serve the chicken hot? A security team that provides timely and actionable information to the business serves the business well. The security team that arrives shaking its finger a day late and a dollar short doesn’t do anyone any good.
- Was the food ready when the guests arrived? Customers care first and foremost about protecting their data. When they ask how the organization protects their data, they want to feel confident that the organization takes custodianship seriously with the right processes.
- Did you invite the right mix of people? Security is a business function that requires the buy-in and collaboration of many different stakeholders: the board, executives, the business, customers, partners, and others. Make sure that the discussion around security is a constructive one that involves the right people at the table.
- Does the conversation suit the meal? The organizational conversation around security needs to be one that empowers the business to succeed securely. It can’t be one of security always being the team of “no.” And it also can’t be one of the business doing whatever it wants without any regard to security.
- Is there enough food for everyone? Resources are always constrained within a security organization. Projects, assets, and human resources need to be focused on value-added activities that can be sustained over time.
- Is there dessert? If the members of a security organization enjoy working together, work efficiently and effectively toward mitigating risk, and are innovative in their approach to security, that’s pretty much the icing on the cake.
Related Content:
- Higher Education: 15 Books to Help Cybersecurity Pros Be Better
- Good Times in Security Come When You Least Expect Them
- 8 Security Buzzwords That Are Too Good to Be True
Josh (Twitter: @ananalytical) is an experienced information security leader with broad experience building and running Security Operations Centers (SOCs). Josh is currently co-founder and chief product officer at IDRRA and also serves as security advisor to ExtraHop. Prior to … View Full Bio